02/08/2024 BullPhish ID release notes v2.94
Enhancements
Sorting feature added to campaign log tables
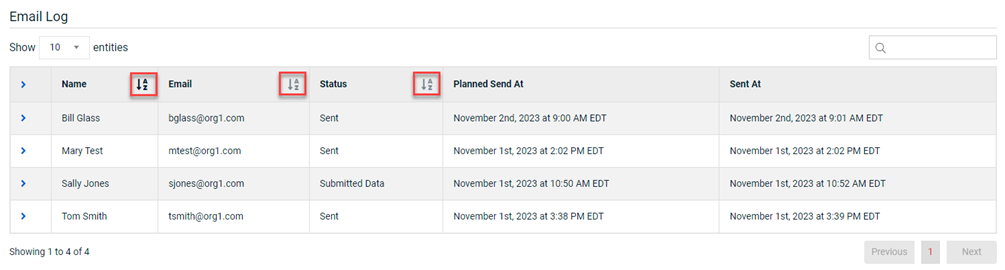
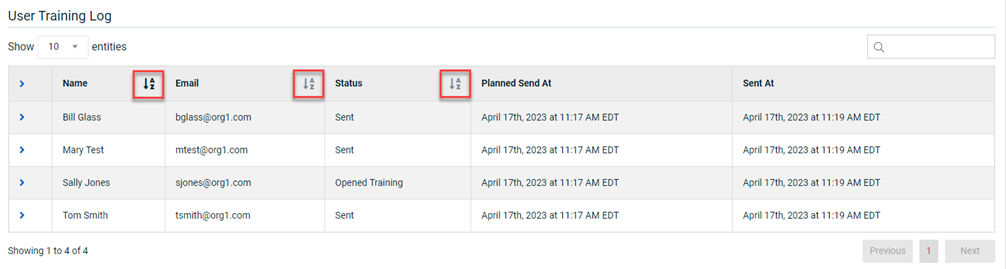
The ability to sort data in the phishing campaign and training campaign log tables has been added. The Email Log (phishing campaigns) and the User Training Log (training campaigns) are found on each campaign's Details page. By default, the table data is listed alphabetically by the target’s first name in the Name column.
Data can be sorted using the following columns:
-
Name: Alphabetically by the target’s first name.
-
Email: Alphabetically by the first letter in the email address.
-
Status: Chronologically based on each target’s campaign status.
-
Phishing campaign statuses: Sent > Opened > Clicked Link > Submitted Data
-
Training campaign statuses: Sent > Opened > Opened Training > Completed Training
Email Log example
User Training Log
Content updates
Updated phishing kits
Updated phishing kits are now available. Each is listed below (links to updated kit) along with an image of its email template and landing page.
-
Norton - Free Offer
Previous version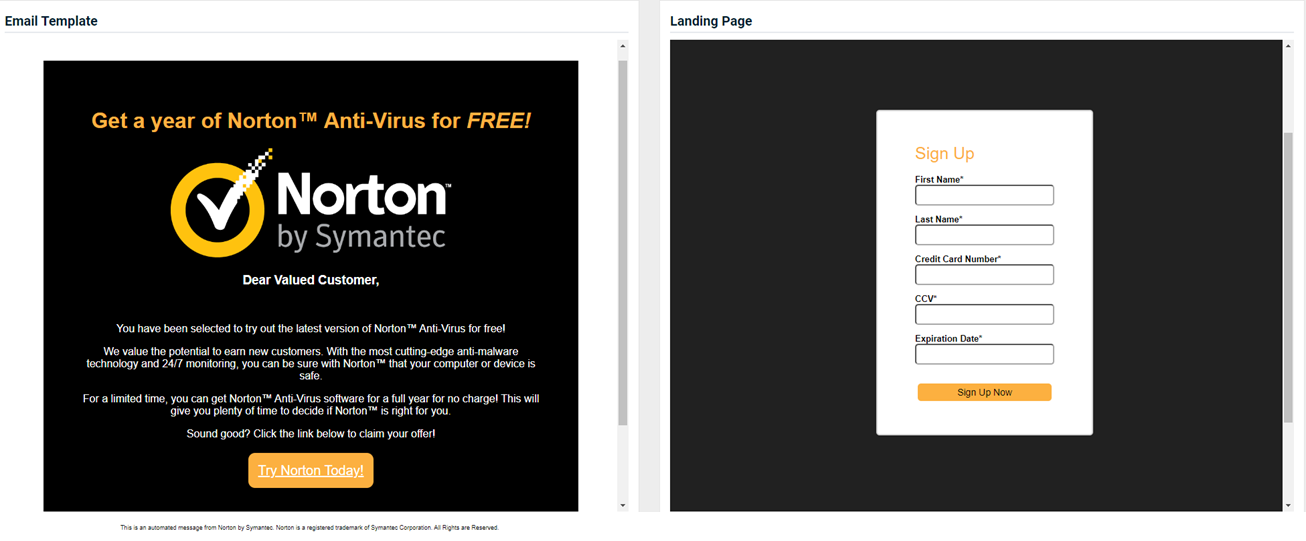
Updated version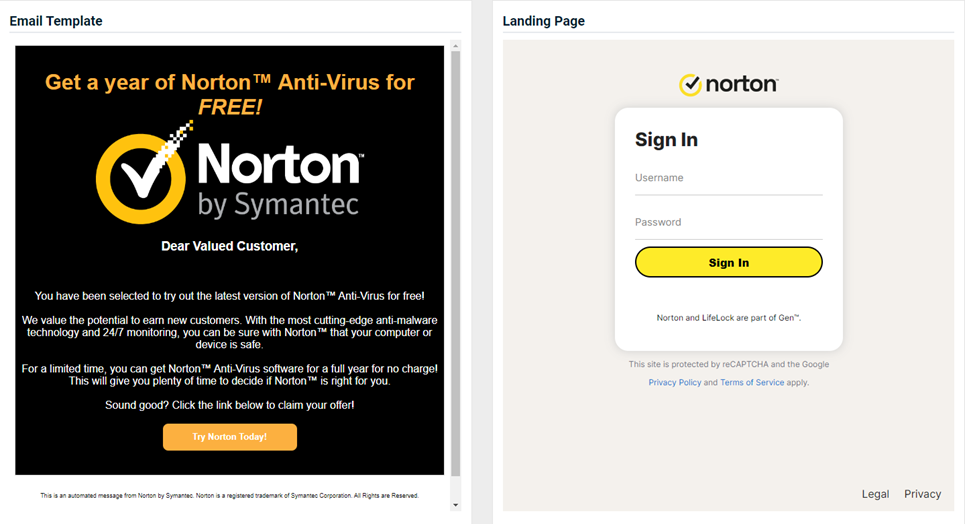
-
Xfinity - You're Receiving a Credit
Previous version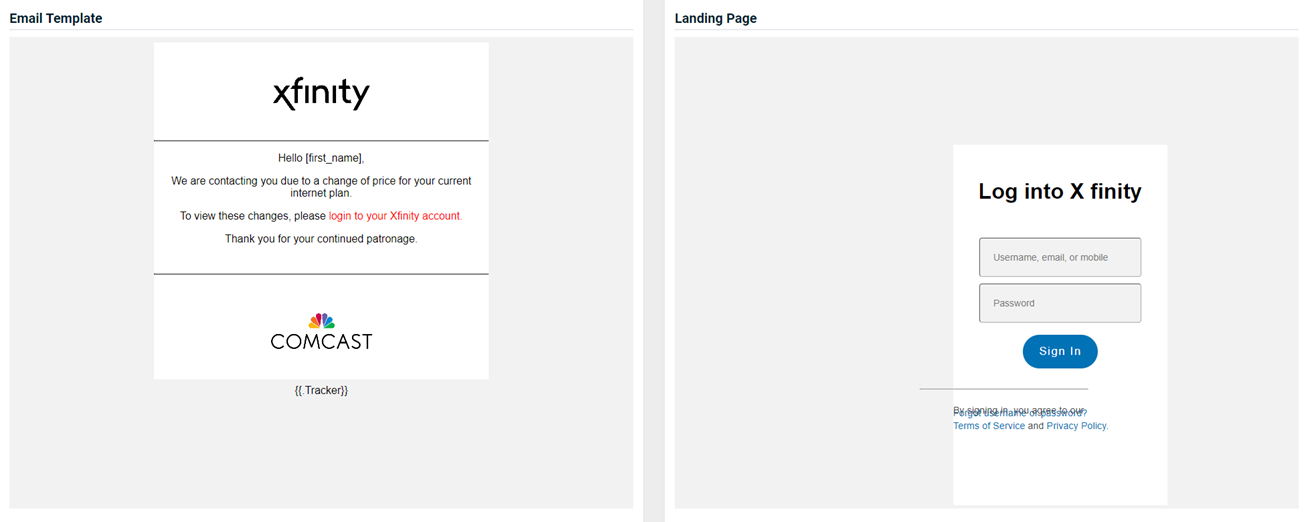
Updated version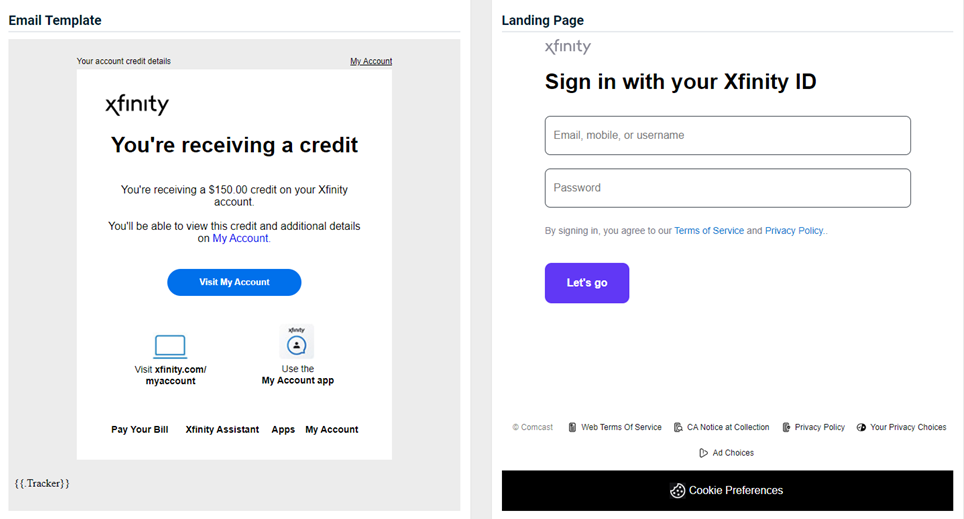
-
World Health Organization - Safety Measures
Previous version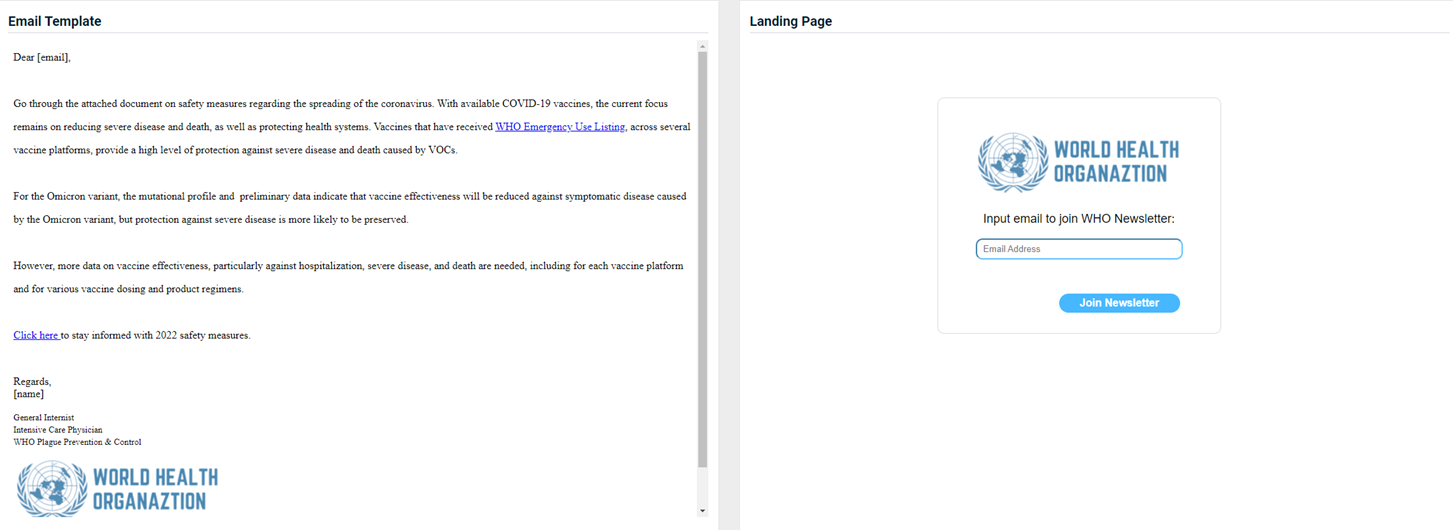
Updated version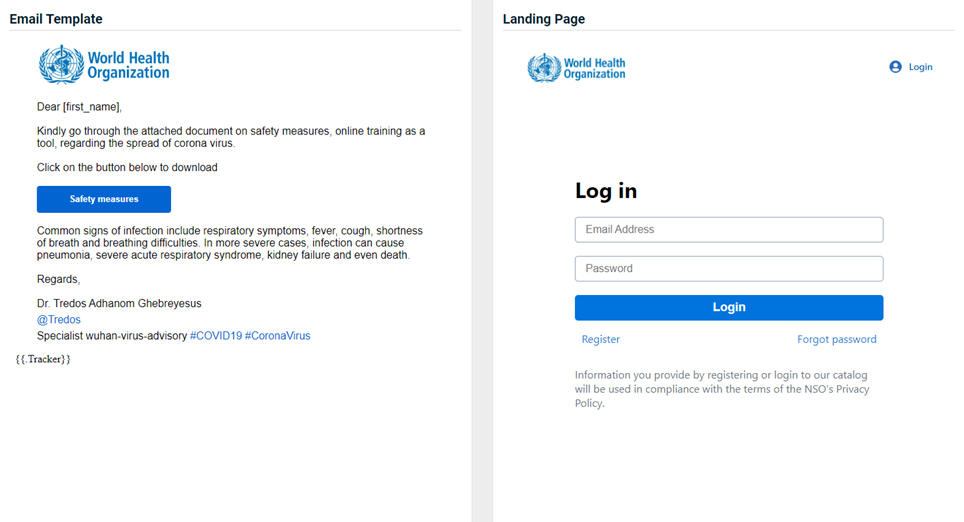
New training courses
New training courses are now available in the Training portal. Click the link to view the course.
- Business Email Compromise: Learn what a business email compromise attack is and examine the common tactics used in these attacks.
- Choosing Strong MFA Second Factors: In this course, second factor techniques are examined and the accounts where you should enable MFA are described.
- Common Attack Methods: In this course, you’ll examine the common phishing attack methods: pretexting, malicious links, and malicious attachments.
- Creating Strong Passwords: Examine techniques for creating, maintaining, and managing strong passwords.
- Dangers of Password Reuse: Examine how common and dangerous password reuse is and the reasons why users continue to reuse passwords.
- Intro to Social Engineering: In this course, you will learn how social engineering attacks work, which will help you identify them in the future.
- Pretexting: Learn about a specific type of social engineering attack known as a pretexting attack.
- Spotting and Reporting Phishing: Learn how to spot phishing emails and examine why it is essential to report them.