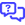04/07/2025 BullPhish ID release notes v2.121
New feature
Optimized business reports
To help ensure the readability and efficiency of monthly and quarterly business reports, new versions of Section 3 and Section 5 will be generated based on the criteria outlined below.
In Section 3, the version included in the report is based on the number of target actions and the number of kits within the report period.
Section 3 versions:
- Phished Users: When there are 100 target actions or less, the data is presented for each target.
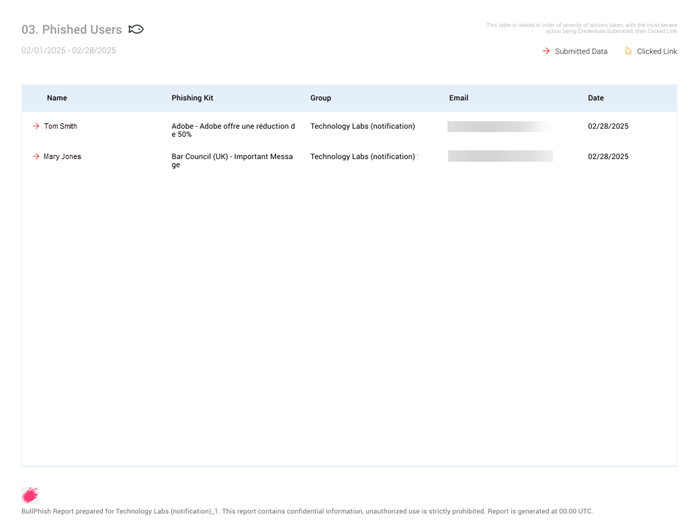
- Phishing Kits by Risk Level: When there are more than 100 target actions AND 150 kits or less, the data is summarized based on phishing kits. This version prevents overly long business reports from being generated.
If there are more than 100 target actions AND more than 150 kits, a note indicates that the maximum of 150 kits is being displayed.
NOTE The actions tracked are Submitted Data and Clicked Link. The Email Opened action is no longer being tracked.
In Section 5, the version included in the report is based on the number of target actions and the number of courses within the report period.
Section 5 versions:
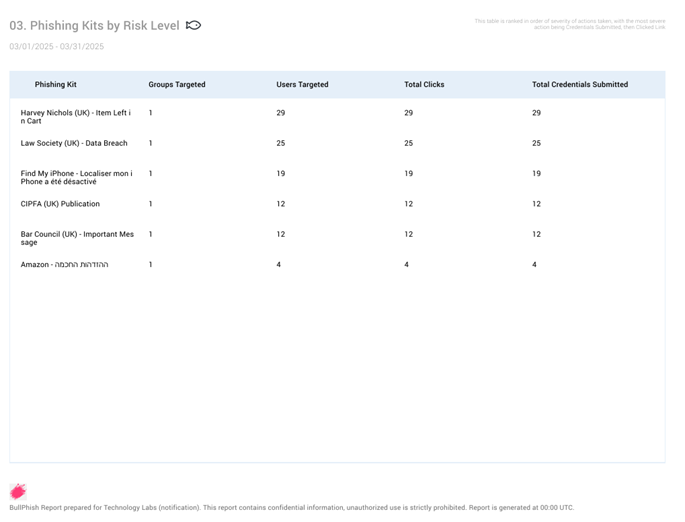
- Users by Risk Level: When there are 100 target actions or less, the data is presented for each target.
- Training Courses by Risk Level: When there are more than 100 target actions AND 150 courses or less, the data is summarized based on training courses, preventing overly long business reports from being generated.
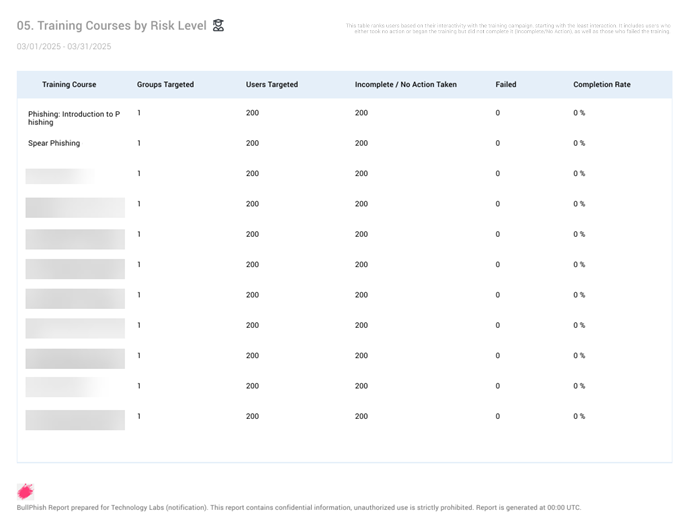
If there are more than 100 target actions AND more than 150 training courses, a note indicates that the maximum of 150 courses is being displayed.
NOTE The actions tracked are Incomplete, No Action, and Failed. The Passed status is no longer being tracked.
For more information about the specific data included in each version, see the article Business reports and user reports.
Content updates
New training courses
The following new training courses are now available in the Training portal:
- What is PHI/ePHI? Learn what PHI entails and how the transition to electronic PHI, or ePHI, impacts you.
- Introduction to Mobile Security: Learn about mobile device security and how to apply safe practices.
- Mobile Security - Mobile Storage: The importance of mobile device storage and the different methods available are explored.
The following training courses have been updated:
- GDPR Rights of Data Subjects Stored Processed Destroyed: Learn about the rights of data subjects under GDPR and how to remain compliant with the rules that govern the way data is stored, processed and destroyed.
- EU GDPR: Important Definitions: Important General Data Protection Regulation (GDPR) definitions are examined.
Translated training courses
The following translated training courses are now available in the Training portal:
| Course: English | Portuguese | French | Spanish | Dutch |
|---|---|---|---|---|
| Choosing Strong MFA Second Factors | Escolhendo Os Segundos Fatores Fortes De MFA VO | Choisir Des Deuxièmes Facteurs Forts Pour L’AMF VO | Elegir Segundos Factores De AMF Potentes VO | |
| Spotting and Reporting Phishing | Identificar E Denunciar Phishing VO | Repérage Et Signalement D’hameçonnage VO | Cómo Detectar Y Denunciar El Phishing VO | |
| Pretexting | Pretexto VO | Soutirage D’informations Confidentielles VO | Pretexting VO | |
| Smishing and Vishing | Smishing e Vishing VO | Hameçonnage Par Message Texte Et Hameçonnage Vocal VO | Smishing Y Vishing VO | |
| Intro to Social Engineering | Noções De Engenharia Social VO | Introduction Au Piratage Psychologique VO | Bases De Ingeniería VO | |
| Baiting | Isca VO | Appâtage VO | Cebo VO | |
| Tailgaiting and Piggybacking | Tailgating e Piggybacking VO | Passage En Double Et Accès À Califourchon VO | Tailgating y Piggybacking VO | |
| Business Email Compromise | Violação De E-mail Corporativo VO | |||
| What is an Insider Threat | Que É Uma Ameaça Interna? | Qu’est-ce Qu’une Menace Interne? VO | ||
| SIM Card Swap Scam | GOLPE DE TROCA DE CHIP | ESCROQUERIE PAR ÉCHANGE DE CARTE SIM | ESTAFA DE CAMBIO DE TARJETA SIM | BEDROG MET VERWISSELING VAN SIM-KAART |
| GDPR: GDPR for Data Breach notification For Processors: Organization’s Next Steps | Regulamento geral de proteção de dados da UE para notificação de violação de dados por processadores: Próximos passos da organização | RGPD de l’UE pour l’Avis d’atteinte à la protection des données des sous-traitants : Prochaines étapes de l’organisation | GDPR de la UE para la notificación de violación de datos para procesadores: Próximos pasos de la organización | EU AVG voor kennisgeving van gegevensinbreuk voor verwerkers: volgende stappen van de organisatie |
| GDPR for data processors | GDPR aplicado a processadores de dados | RGPD pour les sous-traitants des données | GDPR para procesadores de datos | AVG voor gegevensverwerkers |
| UK GDPR vs EU GDPR | GDPR no Reino Unido vs GDPR na União Europeia | RGPD du R.-U. c. RGPD de l’UE | GDPR del Reino Unido frente al GDPR de la UE | Britse AVG vs EU AVG |
| EU GDPR: What is GDPR? | O QUE É GDPR? | QU’EST-CE QUE LE RGPD? | ¿QUÉ ES EL GDPR? | Wat is de AVG? |