Mimecast safelisting guide
Using Mimecast security software, you can safelist (whitelist) BullPhish ID to allow your users to receive our simulated phishing and system emails.
If you run into problems while safe listing in Mimecast, we suggest you first reach out directly to Mimecast for assistance.
How to...
We advise creating a new permitted sender's policy within your Mimecast console to safelist the BullPhish ID.
NOTE Do not edit your default Permitted Sender Policy. Instead, create a new one.
- From the Mimecast Administration Console, open the Administration Toolbar.
- Select Gateway | Policies.
- Select Permitted Senders.
- Select New Policy.
- Select the below settings under the Options, Emails From, Emails To, and Validity sections. For more information, see Mimecast's Configuring a Permitted Senders Policy.
- Enter BullPhish ID IP Address in the Source IP Ranges Field.
IMPORTANT For an up-to-date list of BullPhish ID IP addresses, see our Reference guide for deliverability.
|
Option |
Settings |
|
Policy Narrative |
Phishing Tackle Permitted Senders |
|
Select Option |
Permit Sender |
|
Emails From |
|
|
Addresses Based On |
Both |
|
Applies From |
Everyone |
|
Specifically |
Applies to all Recipients |
|
Emails To |
|
|
Applies To |
Everyone |
|
Specifically |
Applies to all Recipients |
|
Validity |
|
|
Enable/Disable |
Enable |
|
Set policy as perpetual |
Always On |
|
Date Range |
All Time |
|
Policy Override |
Checked |
|
Bi-directional |
Unchecked |
|
Source IP Ranges (n.n.n.n/x) |
BullPhish IP addresses (found in our Reference guide for deliverability) |
Greylisting in Mimecast
Adding BullPhish ID to the permitted sender's list (see above) should bypass Greylisting. However, we recommend following the below Greylisting steps to improve email deliverability.
- From the Mimecast Administration Console, open the Administration Toolbar.
- Select Gateway | Policies.
- Select Greylisting.
- Select New Policy.
- Select the below settings under the Options, Emails From, Emails To, and Validity sections. Enter BullPhish ID IP Address in the Source IP Ranges Field. (For an up-to-date list of BullPhish ID IP addresses, see our Reference guide for deliverability.
|
Option |
Settings |
|
Policy Narrative |
BullPhish ID Greylist |
|
Select Option |
Take No Action |
|
Emails From |
|
|
Addresses Based On |
Both |
|
Applies From |
Everyone |
|
Specifically |
Applies to all Senders |
|
Emails To |
|
|
Applies To |
Everyone |
|
Specifically |
Applies to all Recipients |
|
Validity |
|
|
Enable/Disable |
Enable |
|
Set policy as perpetual |
Always On |
|
Date Range |
All Time |
|
Policy Override |
Checked |
|
Bi-directional |
Unchecked |
|
Source IP Ranges (n.n.n.n/x) |
BullPhish ID IP addresses (found in our guide Reference guide for deliverability) |
If you're spoofing the From or Reply-to domain on your template, please follow the below steps in Mimecast to allow simulated phishing emails to be sent from your domain.
- From the Mimecast Administration Console, open the Administration Toolbar.
- Select Gateway | Policies.
- Select Anti-Spoofing from the policies list.
- Select New Policy.
- Use the below settings under the Options, Emails From, Emails To, and Validity sections. For more information, read this article from Mimecast: Configuring an Anti-Spoofing Policy. Enter BullPhish ID IP Address in the Source IP Ranges Field. (For an up-to-date list of BullPhish ID IP addresses, see our Reference guide for deliverability).
|
Option |
Settings |
|
Options |
|
|
Policy Narrative |
Phishing Tackle Anti-Spoof Allow Policy |
|
Select Option |
Take No Action |
|
Emails From |
|
|
Addresses Based On |
Both |
|
Applies From |
Everyone |
|
Specifically |
This applies to all Senders |
|
Emails To |
|
|
Applies To |
Everyone |
|
Specifically |
Applies to all Recipients |
|
Validity |
|
|
Enable/Disable |
Enable |
|
Set policy as perpetual |
Always On |
|
Date Range |
All Time |
|
Policy Override |
Checked |
|
Bi-directional |
Unchecked |
|
Source IP Ranges (n.n.n.n/x) |
BullPhish ID IP addresses (found in our guide Reference guide for deliverability). |
|
Hostname(s) |
Leave blank |
To allow BullPhish ID simulated phishing emails from spoofed domains to reach your targets, you will want to create an Impersonation Protection Policy and an Anti-Spoofing Policy in the Mimecast Console.
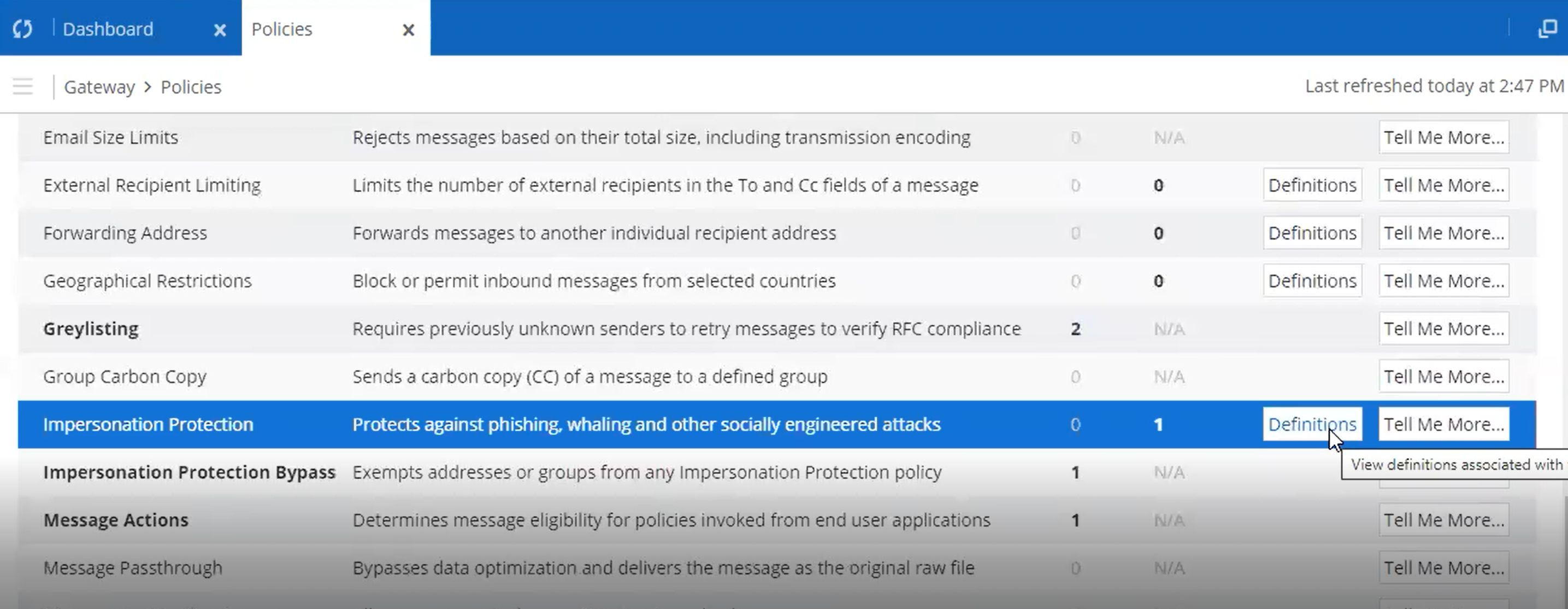
To begin, you’ll need to make an impersonation protection definition (if not already done).
- From the Mimecast Administration Console, open the Administration Toolbar.
- Choose Gateway | Policies.
- Hover over Impersonation Protection and click Definitions.
- Click New Definition.
- Name the definition something unique, like BullPhish ID Impersonation Protection Bypass Definition.
- Choose the relevant settings (shown below). For more information, see Mimecast's documentation in this article: https://community.mimecast.com/docs/DOC-1908#jive_content_id_Configuring_an_Impersonation_Protection_Definition.
|
Option |
Corresponding Settings |
|
Identifier settings |
|
|
Description |
BullPhish ID Impersonation Protection Bypass Def. |
|
Similar Internal Domain |
Checked |
|
Similar Monitored External |
Unchecked |
|
Similarity Distance |
1 |
|
Newly Observed Domain |
Unchecked |
|
Internal Username |
Checked |
|
Reply-to Address Mismatch |
Checked |
|
Targeted Threat Dictionary |
Checked |
|
Mimecast Threat Directory |
Checked |
|
Custom Threat Directory |
[Leave as default] |
|
Number of Hits |
2 |
|
General Actions |
|
|
Mark All Inbound Items as 'External' |
Unchecked |
- First, log into your Mimecast Administration Console.
- Click the Administration toolbar.
- Go to Gateway | Policies.
- Choose Impersonation Protection Bypass from the policies list.
- Click New Policy.
- Select the appropriate policy settings under the Options, Emails From, Emails To, and Validity sections. See Mimecast's Configuring an Impersonation Protection Bypass Policy article for more information on these settings.
NOTE In the Select Option field under Options, select the impersonation protection definition you want to be bypassed. If you have multiple purposes you would like to bypass, you will need to create a separate Impersonation Protection Bypass Policy for each one.
- Enter BullPhish ID IP Address in the Source IP Ranges field. (For an up-to-date list of BullPhish ID IP addresses, see our Reference guide for deliverability).
|
Option |
|
|
Policy Narrative |
BullPhish Impersonation Test |
|
Select Option |
Impersonation Protection Definition |
|
Emails From |
|
|
Addresses Based On |
Both |
|
Applies From |
External Addresses |
|
Specifically |
Applies to all External Senders |
|
Emails To |
|
|
Applies To |
Internal Addresses |
|
Specifically |
Applies to all Internal Recipients |
|
Validity |
|
|
Enable/Disable |
Enable |
|
Set policy as perpetual |
Always On |
|
Date Range |
All Time |
|
Policy Override |
Checked |
|
Bi-directional |
Unchecked |
|
Source IP Ranges |
BullPhish ID IP addresses (found in our Reference guide for deliverability) |
Mimecast's URL Protection service scans links sent within emails as they are delivered. Occasionally, this causes simulated phishing emails to trigger this service. Follow the below steps to create a URL Protection Bypass policy.
NOTE Configuring this policy is only necessary if Mimecast URL Protection has been enabled.
- From the Mimecast Administration Console, open the Administration Toolbar.
- Select Gateway | Policies.
- Select URL Protection Bypass.
- Select New Policy.
- Select the appropriate settings (below) under the Options, Emails From, Emails To, and Validity sections. See Mimecast's article on Configuring a URL Protection Bypass Policy for more information on these settings.
- Enter BullPhish ID IP Address in the Source IP Ranges field. (For an up-to-date list of BullPhish ID IP addresses, see our Reference guide for deliverability).
|
Option |
Settings |
|
Options |
|
|
Policy Narrative |
Phishing Tackle URL Protection Bypass |
|
Select Option |
Disable URL Protection |
|
Emails From |
|
|
Addresses Based On |
Both |
|
Applies From |
Everyone |
|
Specifically |
This applies to all Senders |
|
Emails To |
|
|
Applies To |
Internal Addresses |
|
Profile Group |
Applies to all Internal Recipients |
|
Validity |
|
|
Enable/Disable |
Enable |
|
Set policy as perpetual |
Always On |
|
Date Range |
All Time |
|
Policy Override |
Checked |
|
Bi-directional |
Unchecked |
|
Source IP Ranges (n.n.n.n/x) |
BullPhish ID IP addresses (found in our Reference guide for deliverability) |
|
Hostname(s) |
Leave blank |
If you'd like to use attachments in your simulated phishing tests, follow the steps below to increase the likelihood that emails with attachments from Bullphish will successfully arrive in your users' inboxes. Mimecast may still prevent the delivery of attachments. Set up a test after creating this policy to ensure your desired attachment goes through.
- From the Mimecast Administration console, open the Administration Toolbar.
- Select Gateway | Policies.
- Select Attachment Protection Bypass.
- Select New Policy.
- Select the appropriate settings (below) under the Options, Emails From, Emails To, and Validity sections. For more information, see Mimecast's article on Configuring a URL Protection Bypass Policy.
- Enter Bullphish IP Address in the Source IP Ranges field. (For an up-to-date list of Bullphish IP addresses, see our guide Reference guide for deliverability).
|
Option |
Settings |
|
Options |
|
|
Policy Narrative |
Bullphish Attachment Protection Bypass |
|
Select Option |
Disable Attachment Protection |
|
Emails From |
|
|
Addresses Based On |
The Return Address (Email Envelope From) |
|
Applies From |
Everyone |
|
Specifically |
This applies to all Senders |
|
Emails To |
|
|
Applies To |
Internal Addresses |
|
Profile Group |
Applies to all Internal Recipients |
|
Validity |
|
|
Enable/Disable |
Enable |
|
Set policy as perpetual |
Always On |
|
Date Range |
All Time |
|
Policy Override |
Checked |
|
Bi-directional |
Unchecked |
|
Source IP Ranges (n.n.n.n/x) |
BullPhish ID IP addresses (found in our Reference guide for deliverability). |
If you'd like to use attachments in your simulated phishing tests, follow the steps below to prevent attachments from being stripped from emails, potentially resulting in skewed test results.
- From the Mimecast Administration console, open the Administration Toolbar.
- Select Gateway | Policies.
- Select Attachment Protection Bypass.
- Select New Policy.
- Select the appropriate settings (below) under the Options, Emails From, Emails To, and Validity sections. For more information, see Mimecast's article on Configuring a URL Protection Bypass Policy.
- Enter Bullphish IP Address in the Source IP Ranges Field. (For an up-to-date list of Bullphish IP addresses, see our guide Reference guide for deliverability
|
Option |
Settings |
|
Options |
|
|
Policy Narrative |
Bullphish Attachment Management Bypass |
|
Select Option |
Disable Attachment Management |
|
Emails From |
|
|
Addresses Based On |
Both |
|
Applies From |
Everyone |
|
Specifically |
Applies to all Senders |
|
Emails To |
|
|
Applies To |
Everyone |
|
Profile Group |
Applies to all Recipients |
|
Validity |
|
|
Enable/Disable |
Enable |
|
Set policy as perpetual |
Always On |
|
Date Range |
All Time |
|
Policy Override |
Checked |
|
Bi-directional |
Unchecked |
|
Source IP Ranges (n.n.n.n/x) |
BullPhish ID IP addresses (found in our Reference guide for deliverability). |
If you are having issues with our emails being sent to your spam folder or being quarantined, you may want to set up this additional policy. First, you'll need to set up the inbound definition and then you can create the policy. Below are instructions on how to add this policy.
DNS Authentication - Inbound Definition Setup
- From the Mimecast Administration console, open the Administration Toolbar.
- Select Gateway | Policies.
- Click the Definitions drop-down menu.
- Select the DNS Authentication - Inbound option.
- Select New DNS Authentication - Inbound Checks.
- Create a name for the definition and leave all optionsunchecked.
- Click Save and Exit to save your changes.
DNS Authentication - Inbound Policy Setup
-
From the Mimecast Administration console, open the Administration Toolbar.
- Select Gateway | Policies.
- Select DNS Authentication - Inbound.
- Select New Policy.
- Select the appropriate settings (below) under the Options, Emails From, Emails To, and Validity sections. For more information, see Mimecast's article on Configuring a URL Protection Bypass Policy.
- Enter Bullphish IP Address in the Source IP Ranges field. (For an up-to-date list of Bullphish IP addresses, see our guide Reference guide for deliverability).
|
Option |
Setting |
|
Options |
|
|
Policy Narrative |
Bullphish DNS Auth Bypass |
|
Select Option |
No Authentication |
|
Emails From |
|
|
Addresses Based On |
Both |
|
Applies From |
Everyone |
|
Specifically |
Applies to all Senders |
|
Emails To |
|
|
Applies To |
Address Groups |
|
Profile Group |
Choose affected groups with Lookup button |
|
Validity |
|
|
Enable/Disable |
Enable |
|
Set policy as perpetual |
Always On |
|
Date Range |
All Time |
|
Policy Override |
Checked |
|
Bi-directional |
Unchecked |
|
Source IP Ranges (n.n.n.n/x) |
BullPhish ID IP addresses (found in our Reference guide for deliverability). |
If you'd like to prevent Mimecast from re-writing the links in the Phishing tests you send, you can do so by adding Bullphish's phish link domains as Permitted URLs in Mimecast. You can find a list of our phish link domains (sending domains) in our guide Reference guide for deliverability.
Keep in mind, we don't recommend creating an exception for this unless you also have exceptions for other senders already in place. Otherwise, seeing anything other than a rewritten Mimecast URL will be a red flag for users and may skew your results.
For more information on disabling link rewriting on permitted URLs, see Mimecast's article Targeted Threat Protection: Managed URLs.