Kaseya spring release: Bullphish ID
This page details each Bullphish ID release launched during the Kaseya Spring release.
New feature
Optimized business reports
To help ensure the readability and efficiency of monthly and quarterly business reports, new versions of Section 3 and Section 5 will be generated based on the criteria outlined below.
In Section 3, the version included in the report is based on the number of target actions and the number of kits within the report period.
Section 3 versions:
- Phished Users: When there are 100 target actions or less, the data is presented for each target.
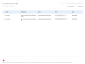
- Phishing Kits by Risk Level: When there are more than 100 target actions AND 150 kits or less, the data is summarized based on phishing kits. This version prevents overly long business reports from being generated.

If there are more than 100 target actions AND more than 150 kits, a note indicates that the maximum of 150 kits is being displayed.
NOTE The actions tracked are Submitted Data and Clicked Link. The Email Opened action is no longer being tracked.
In Section 5, the version included in the report is based on the number of target actions and the number of courses within the report period.
Section 5 versions:
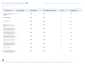
- Users by Risk Level: When there are 100 target actions or less, the data is presented for each target.
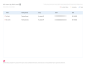
- Training Courses by Risk Level: When there are more than 100 target actions AND 150 courses or less, the data is summarized based on training courses, preventing overly long business reports from being generated.
If there are more than 100 target actions AND more than 150 training courses, a note indicates that the maximum of 150 courses is being displayed.
NOTE The actions tracked are Incomplete, No Action, and Failed. The Passed status is no longer being tracked.
For more information about the specific data included in each version, see the article Business reports and user reports.
Content updates
New training courses
The following new training courses are now available in the Training portal:
- What is PHI/ePHI? Learn what PHI entails and how the transition to electronic PHI, or ePHI, impacts you.
- Introduction to Mobile Security: Learn about mobile device security and how to apply safe practices.
- Mobile Security - Mobile Storage: The importance of mobile device storage and the different methods available are explored.
The following training courses have been updated:
- GDPR Rights of Data Subjects Stored Processed Destroyed: Learn about the rights of data subjects under GDPR and how to remain compliant with the rules that govern the way data is stored, processed and destroyed.
- EU GDPR: Important Definitions: Important General Data Protection Regulation (GDPR) definitions are examined.
Translated training courses
The following translated training courses are now available in the Training portal:
| Course: English | Portuguese | French | Spanish | Dutch |
|---|---|---|---|---|
| Choosing Strong MFA Second Factors | Escolhendo Os Segundos Fatores Fortes De MFA VO | Choisir Des Deuxièmes Facteurs Forts Pour L’AMF VO | Elegir Segundos Factores De AMF Potentes VO | |
| Spotting and Reporting Phishing | Identificar E Denunciar Phishing VO | Repérage Et Signalement D’hameçonnage VO | Cómo Detectar Y Denunciar El Phishing VO | |
| Pretexting | Pretexto VO | Soutirage D’informations Confidentielles VO | Pretexting VO | |
| Smishing and Vishing | Smishing e Vishing VO | Hameçonnage Par Message Texte Et Hameçonnage Vocal VO | Smishing Y Vishing VO | |
| Intro to Social Engineering | Noções De Engenharia Social VO | Introduction Au Piratage Psychologique VO | Bases De Ingeniería VO | |
| Baiting | Isca VO | Appâtage VO | Cebo VO | |
| Tailgaiting and Piggybacking | Tailgating e Piggybacking VO | Passage En Double Et Accès À Califourchon VO | Tailgating y Piggybacking VO | |
| Business Email Compromise | Violação De E-mail Corporativo VO | |||
| What is an Insider Threat | Que É Uma Ameaça Interna? | Qu’est-ce Qu’une Menace Interne? VO | ||
| SIM Card Swap Scam | GOLPE DE TROCA DE CHIP | ESCROQUERIE PAR ÉCHANGE DE CARTE SIM | ESTAFA DE CAMBIO DE TARJETA SIM | BEDROG MET VERWISSELING VAN SIM-KAART |
| GDPR: GDPR for Data Breach notification For Processors: Organization’s Next Steps | Regulamento geral de proteção de dados da UE para notificação de violação de dados por processadores: Próximos passos da organização | RGPD de l’UE pour l’Avis d’atteinte à la protection des données des sous-traitants : Prochaines étapes de l’organisation | GDPR de la UE para la notificación de violación de datos para procesadores: Próximos pasos de la organización | EU AVG voor kennisgeving van gegevensinbreuk voor verwerkers: volgende stappen van de organisatie |
| GDPR for data processors | GDPR aplicado a processadores de dados | RGPD pour les sous-traitants des données | GDPR para procesadores de datos | AVG voor gegevensverwerkers |
| UK GDPR vs EU GDPR | GDPR no Reino Unido vs GDPR na União Europeia | RGPD du R.-U. c. RGPD de l’UE | GDPR del Reino Unido frente al GDPR de la UE | Britse AVG vs EU AVG |
| EU GDPR: What is GDPR? | O QUE É GDPR? | QU’EST-CE QUE LE RGPD? | ¿QUÉ ES EL GDPR? | Wat is de AVG? |
Emails were sent via SMTP despite Graphus integration
Issue:
Emails were mistakenly sent via SMTP instead of the Graphus service for some SMBs. This occurred for SMBs whose integration status was re-enabled after support for multiple sub-domains was introduced. Although the integration status showed as active, Graphus was not part of the delivery process, leading to incorrect email routing.
Fix:
Now, when the integration status is active, all emails are correctly routed through the Graphus service.
Fix
Issue
When a partner with the Per Users account type has more active targets than the total number of licenses purchased, the Insufficient Licenses banner is displayed on each of the partner's BullPhish ID pages. This is the correct behavior.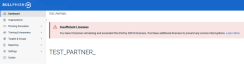
However, when the partner's account type was switched from Per Users to Per Organizations, the Insufficient Licenses banner was still displayed. This banner applies to the Per Users account type only and therefore, should not have been displayed when switching to the Per Organizations account type.
This issue has been resolved. Now, when a partner's account type is switched from Per Users to Per Organizations, the Insufficient Licenses banner will not be displayed.
Issue
For organizations with an active Graphus integration, training and phishing campaign emails were still being sent via SMTP. This issue has been resolved. All campaign emails are now being delivered via the Graphus API for organizations with active Graphus integration.
Enhancements
BullPhish ID welcome email and DarkWeb ID account
For a user that has both DarkWeb ID and BullPhish ID accounts, the BullPhish ID welcome email sent to the user now includes key points regarding these accounts:
- BullPhish ID and DarkWeb ID share the same login credentials. This includes username, password, and multi-factor authentication (MFA) settings.
- Updating or resetting your password on BullPhish ID will automatically update it on DarkWeb ID.
- Once you activate either account, your credentials will work seamlessly across both platforms.
This information has been added to all of the BullPhish ID welcome email templates (user does not have a KaseyaOne account, has a KaseyaOne account, login with KaseyaOne account is required) where the user has a DarkWeb ID account.
Here is an example of the login with KaseyaOne account required email.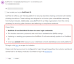
Fixes
Issue
SMB Privileged Users received an error when navigating to the Training Portal Administration page. This issue has been resolved. Now, when an SMB Privileged User selects Training & Awareness > Training Portal, the Training Portal Administration page is displayed.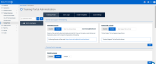
Fixes
Issue
SMB Privileged Users were not able to see any directories on the Directories page for their organization unless they applied the Organization filter. This issue has been resolved. Now, when an SMB Privileged User accesses the Directories page, the directories for their organization are listed without the need to apply the Organization filter.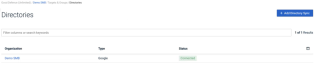
Fixes
Issue
Targets who had failed a training course were still receiving training email reminders to complete the course. This been fixed and this scenario is now excluded from receiving training email reminders.
Issue
A custom sending profile could not be selected for a new or updated phishing kit if the kit was being assigned to an SMB organization that is listed 21 or later on the partner's Organization page.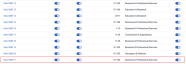
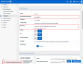
This issue has been resolved. Now, a custom sending profile can be selected for a new or updated phishing kit when it is assigned to SMB organizations listed 21 or later on the partner's Organization page.
Issue
The wrong Training Course Expiration value was shown on the training campaign's Edit page. In this example, the Start Date and Expiration Date on the training campaign's Details page indicate a course duration of 6 months. But the campaign's Edit page shows a Training Course Expiration value of 7 days.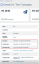
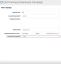
This has been fixed. The Training Course Expiration field will now show the correct value (6 months in our example) based on the campaign's start and expiration dates.
Issue
In the quarterly and monthly business reports, the statistics in the details tables for both phishing and training campaigns were sometimes calculated incorrectly. While the values in the graph were correct, the total of the individual campaign status values sometimes did not equal the totals shown in the graph, as shown for the No Action Taken status below.
This issue has been resolved and the total of the individual campaign status values will equal the totals shown in the graph.
Graphus integration was limiting number of licensed users to 20
On January 14, 2025, an enhancement was added to the v2.115 release where targets across multiple domains are supported when integrating BullPhish ID with Graphus.
After the release, an issue was discovered where BullPhish ID was failing to recognize some users as protected, even though they were correctly marked as protected on the Graphus side.
BullPhish ID was recognizing a maximum of 20 users per domain as licensed in Graphus. When more than 20 users were active, the system treated the additional users as unlicensed, causing the organization's status to display an Error. Therefore, all of the organization's targets received campaign emails via SMTP.
This issue has now been resolved. Moving forward, all users protected by Graphus will be counted as licensed and will receive emails through Graphus instead of the SMTP service.
Enhancement
BullPhish ID integration with Graphus now supports targets across multiple domains
When integrating a BullPhish ID organization with Graphus, all targets, regardless of their domain, are now included in the integration. Previously, targets could only belong to a single domain for the integration to work. Now, as long as all targets are protected by Graphus, they can belong to different domains or subdomains.
For organizations that were integrated with Graphus before this update, a banner will appear notifying them that domain restrictions have been removed. This means that all domains and subdomains for these organizations are now automatically included in the integration.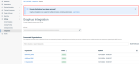
The Graphus Integration table has been updated and now shows the name of the integrated organization, the status of the integration, and the date and time the integration was updated. 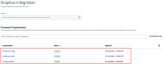
For more information, refer to the article BullPhish ID integration with Graphus.
Issue
When sorting kits by the Open Rate, Click Rate, or Submit Data Rate columns on the Phishing Kits page, a duplicate kit entry was created in the table for any kit that was used in a campaign. 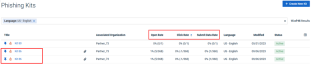
This issue has been resolved and all duplicate kit entries have been removed.
NOTE If a kit was not used in a campaign, a duplicate was not created in the table.



