Release notes
This article is your go to resource to learn about new BullPhish ID features, product enhancements, and application fixes.
2026
- BullPhish ID February 19, 2026 v2.141 release notes
- February 18, 2026 - Allowlisting new global sending domains
- BullPhish ID February 10, 2026 v2.140 release notes
- BullPhish ID January 22, 2026 v2.139 release notes
- BullPhish ID January 20, 2026 v2.138.01 release notes - Hot Fix
- January 12, 2026 Improved INKY + BullPhish ID Integration
2025
- BullPhish ID December 11, 2025 v2.137 release notes
- BullPhish ID November 27, 2025 v2.136 release notes
- BullPhish ID November 13, 2025 v2.135 release notes
- BullPhish ID November 6, 2025 v2.134 release notes
- BullPhish ID October 20, 2025 v2.133 release notes
- BullPhish ID October 9, 2025 v2.132 release notes
- BullPhish ID September 25, 2025 v2.131 release notes
- BullPhish ID August 21, 2025 v2.130 release notes
- BullPhish ID August 11, 2025 v2.129 release notes
- BullPhish ID July 28, 2025 v2.128 release notes
- BullPhish ID June 26, 2025 v2.126 release notes
- BullPhish ID June 16, 2025 v2.125.03 release notes - Hot Fix
- BullPhish ID June 5, 2025 v2.125.02 release notes - Hot Fix
- BullPhish ID May 30, 2025 v2.125.01 release notes - Hot Fix
- BullPhish ID May 29, 2025 v2.125 release notes
- BullPhish ID May 20, 2025 v2.124 release notes
- 05/05/2025 BullPhish ID release notes v2.123
- 04/17/2025 BullPhish ID release notes v2.122
- 04/07/2025 BullPhish ID release notes v2.121
- 03/28/2025 BullPhish ID release notes v2.120.01 - Hot Fix
- 03/10/2025 BullPhish ID release notes v2.119
- 02/26/2025 BullPhish ID release notes v2.118
- 02/06/2025 BullPhish ID release notes v2.117
- 01/27/2025 BullPhish ID release notes v2.116
- 01/21/2025 BullPhish ID release notes v2.115.02 - Hot Fix
- 01/08/2025 BullPhish ID release notes v2.115
2024
- 12/12/2024 BullPhish ID release notes v2.114
- 11/28/2024 BullPhish ID release notes v2.113
- 11/18/2024 BullPhish ID release notes v2.112
- 11/04/2024 BullPhish ID release notes v2.111
- 10/21/2024 BullPhish ID release notes v2.110
- 10/08/2024 BullPhish ID release notes v2.109
- 09/05/2024 BullPhish ID release notes v2.108
- 08/22/2024 BullPhish ID release notes v2.107
- 08/08/2024 BullPhish ID release notes v2.106
- 07/29/2024 BullPhish ID release notes v2.105
- 07/23/2024 New self-guided onboarding feature
- 07/11/2024 BullPhish ID release notes v2.104
- 06/28/2024 BullPhish ID release notes v2.103
- 06/17/2024 BullPhish ID release notes v2.102
- 05/13/2024 BullPhish ID release notes v2.99
- 05/09/2024 BullPhish ID release notes v2.98.02 - Hot Fix
- 05/08/2024 BullPhish ID release notes v2.98.01 - Hot Fix
- 04/19/2024 BullPhish ID release notes v2.98
- 04/08/2024 BullPhish ID release notes v2.97
- 03/07/2024 BullPhish ID release notes v2.95
- 02/08/2024 BullPhish ID release notes v2.94
- 01/26/2024 BullPhish ID release notes v2.93
- 01/18/2024 BullPhish ID release notes v2.92.01 - Hot Fix
- 01/17/2024 BullPhish ID release notes v2.92
- 01/04/2024 BullPhish ID release notes v2.91.01 - Hot Fix
2023
New Features
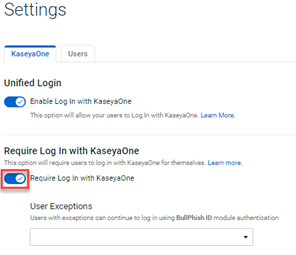
Require Log In with KaseyaOne
The Require Log In with KaseyaOne feature forces users to login with their KaseyaOne credentials to access BullPhish ID. When the feature is enabled by an organization, users can no longer log into BullPhish ID locally with their BullPhish ID credentials.
Enabling the Require Log In with KaseyaOne feature allows users to authenticate with their KaseyaOne modules using just one set of credentials. This provides a smoother user experience and increased security.
You can select users to whom you want to provide an exception to this requirement. The selected users will be able to log into BullPhish ID with their BullPhish ID credentials while still having the option to log in using the KaseyaOne login method.
The Require Log In with KaseyaOne feature is available on the Organizations > Settings page. KaseyaOne Unified Login must be enabled to enable the Require Log In with KaseyaOne feature.
For more information, see the following articles:
- Enabling KaseyaOne Unified Login for your BullPhish ID organization
- Requiring users to log in with KaseyaOne
Content updates
-
Logging into BullPhish ID
This article describes the updated methods for logging into BullPhish ID based on KaseyaOne Unified Login scenarios. The method you use is determined by the following circumstances:- Whether KaseyaOne Unified Login is enabled for your organization.
- If KaseyaOne Unified Login is enabled, whether login with KaseyaOne is required.
- Whether you have a KaseyaOne account.
The article also includes first-time login and subsequent login instructions.
-
Microsoft has changed the name of Azure Active Directory to Microsoft Entra ID. Therefore, the article Chapter 7.3.1: Integrating with Azure Active Directory has been renamed Chapter 7.3.1: Integrating with Microsoft Entra ID. The article content has been updated as well to reflect the name change. For more information, see the Microsoft article New name for Azure Active Directory.
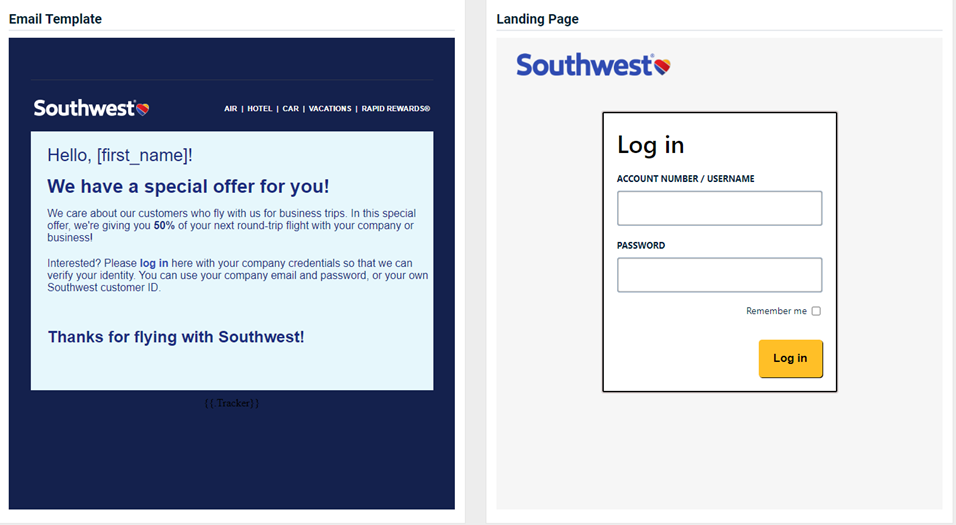
Updated and new phishing kits
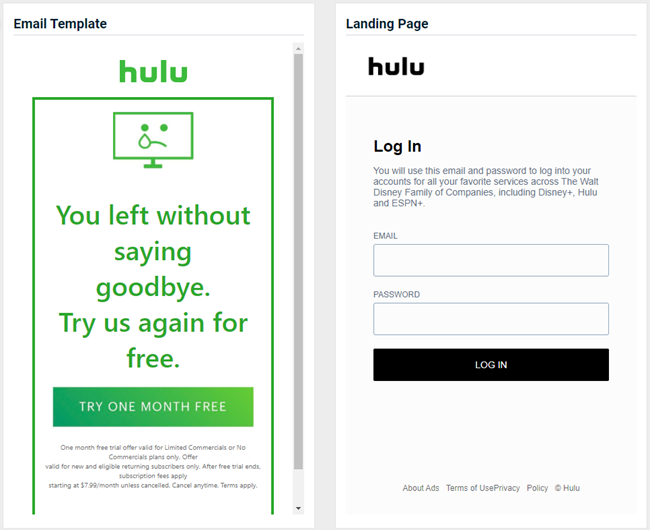
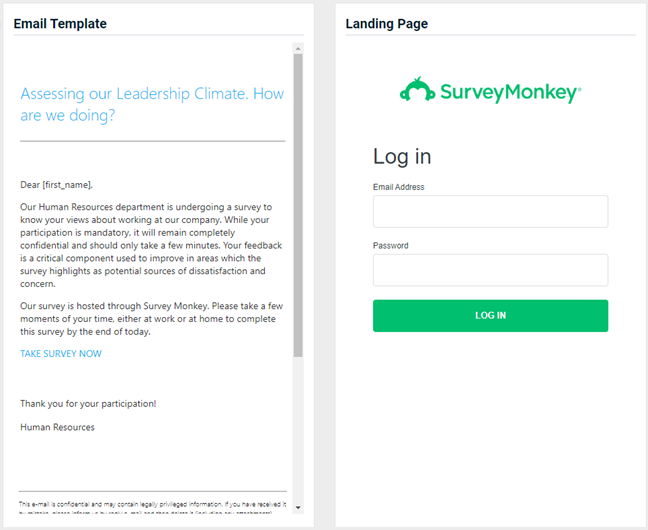
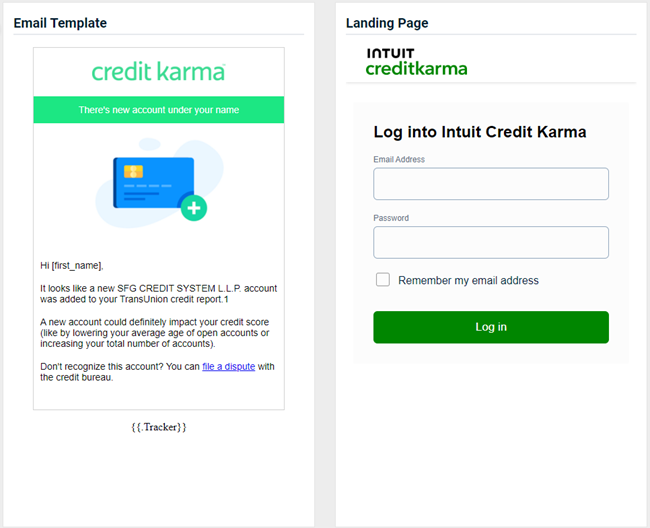
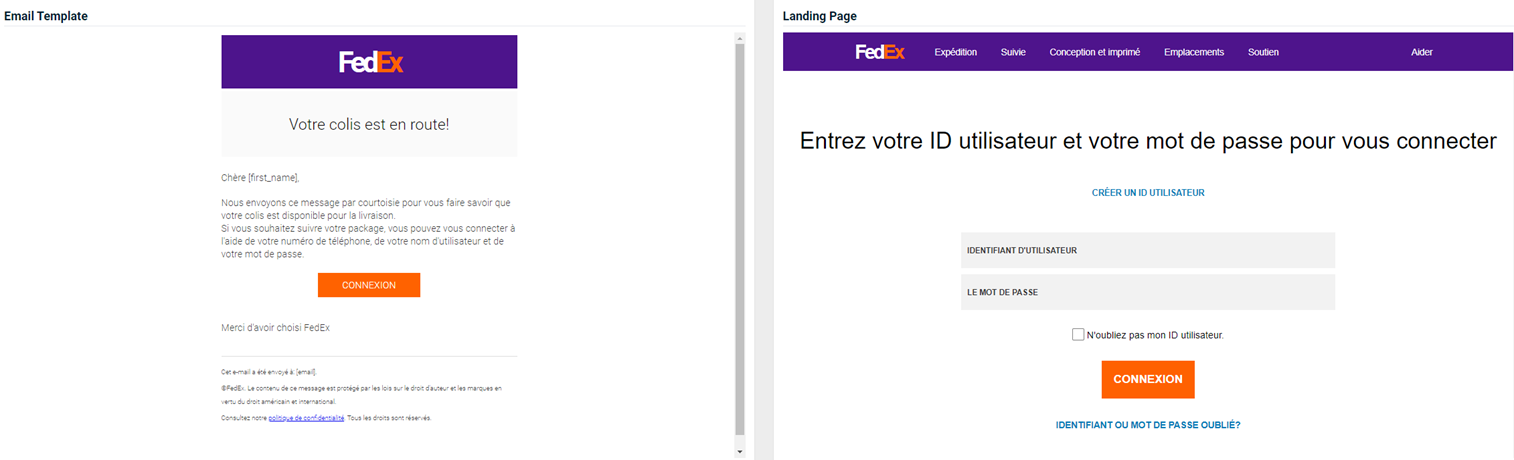
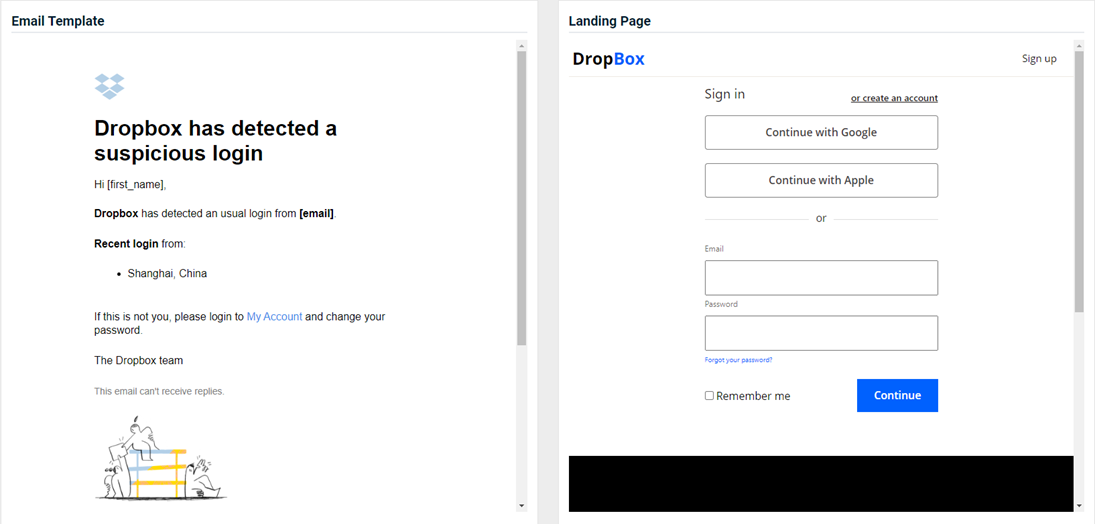
Updated and new phishing kits are now available. Each is listed below (links to updated version/new kit) along with an image of its email template and landing page.
-
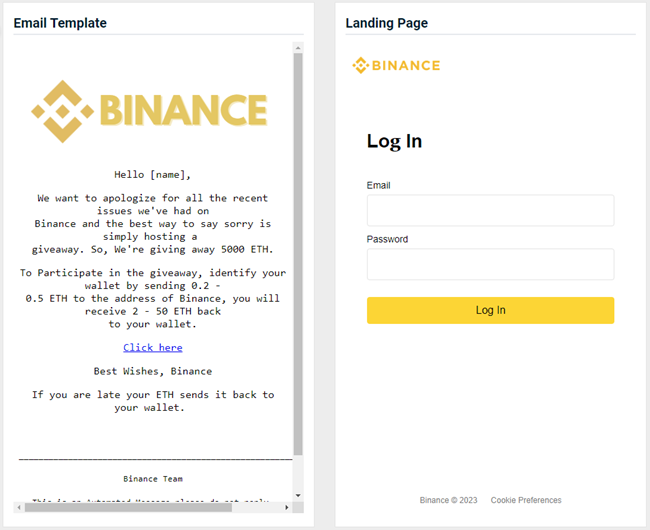
USPS - Mail-In Ballot
Previous version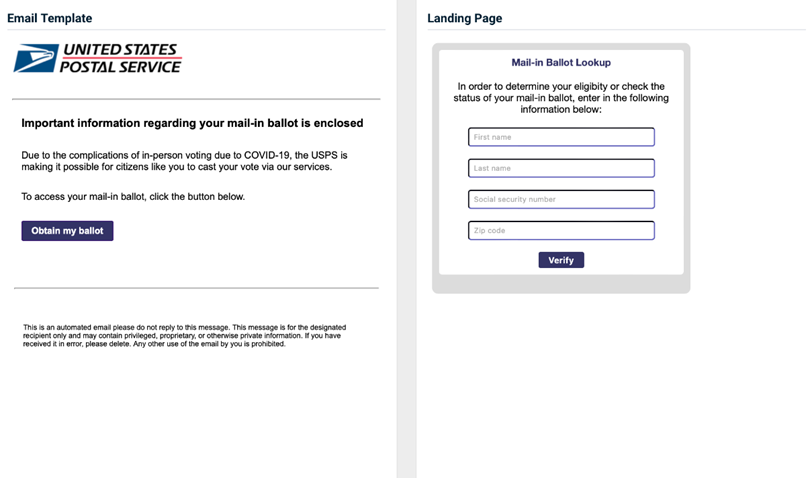
Updated version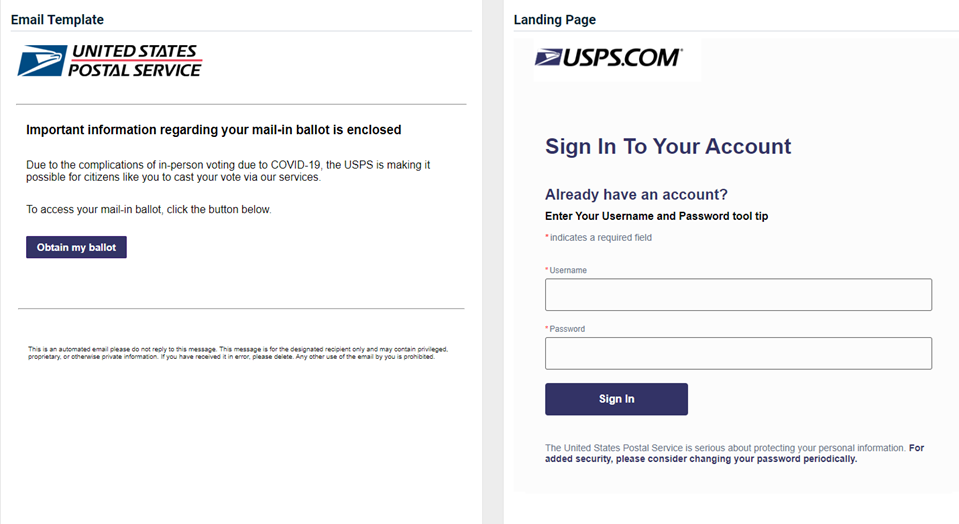
-
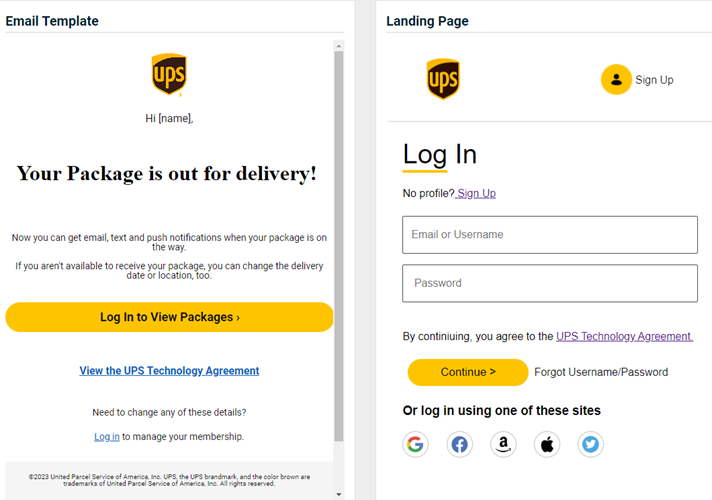
USPS - Delivery Notification
Previous version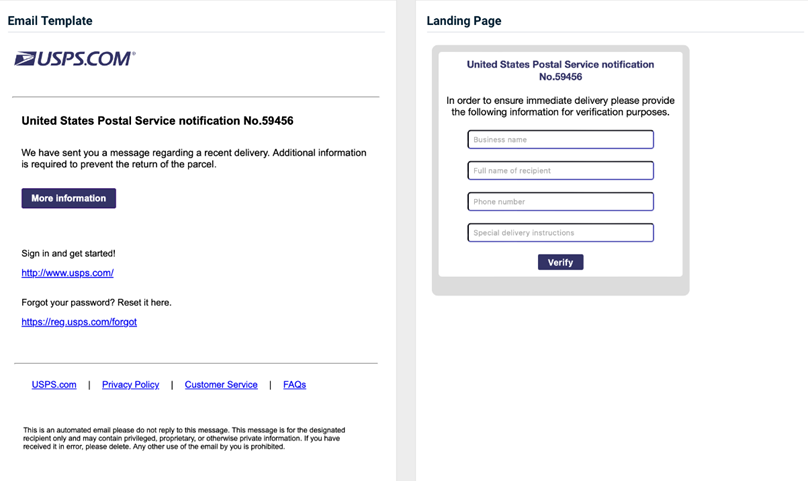
Updated version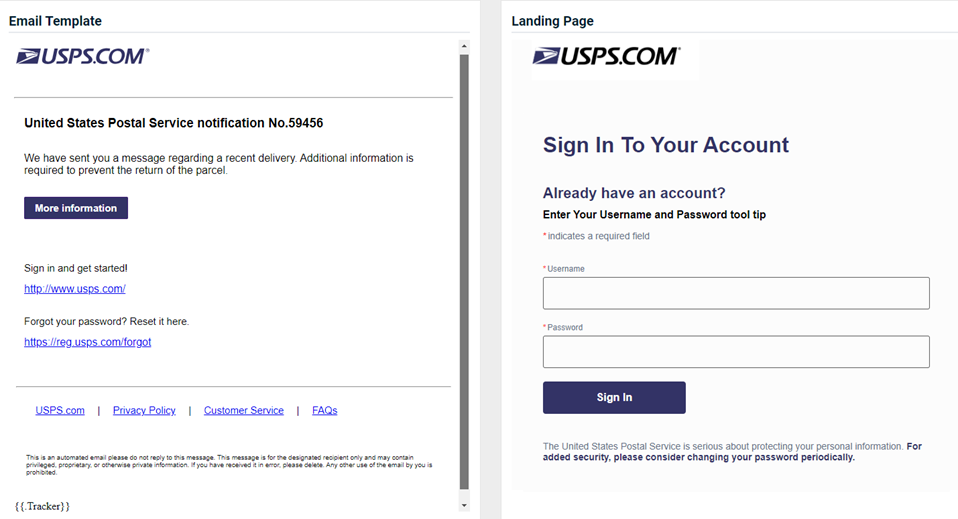
-
State Farm - Discount Offer
Previous version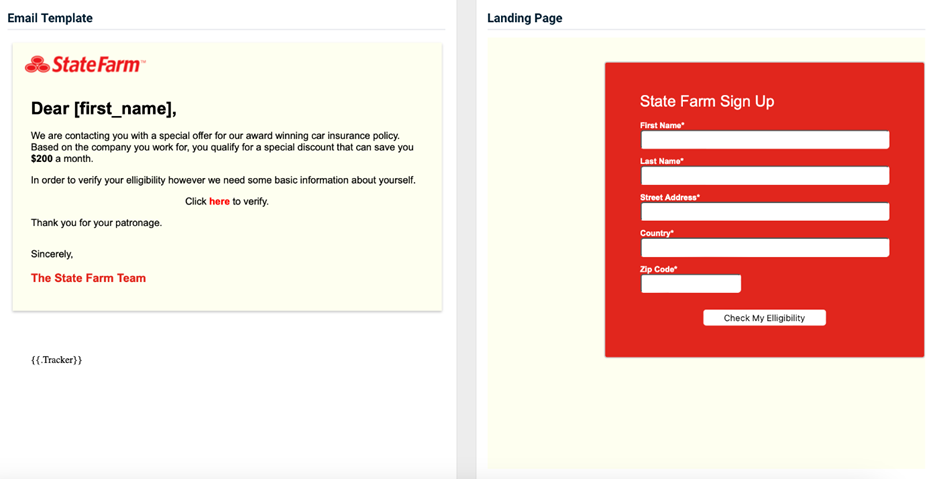
Updated version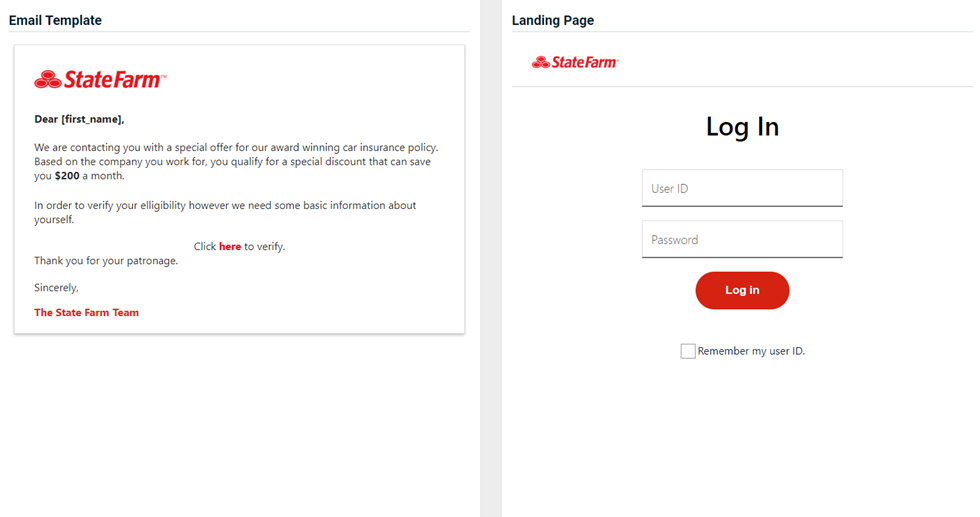
-
Vote.Org - Donate To Election
Previous version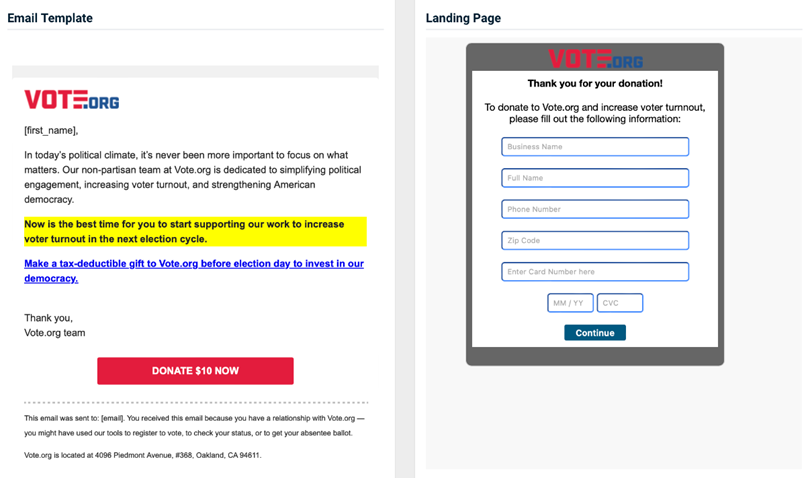
Updated version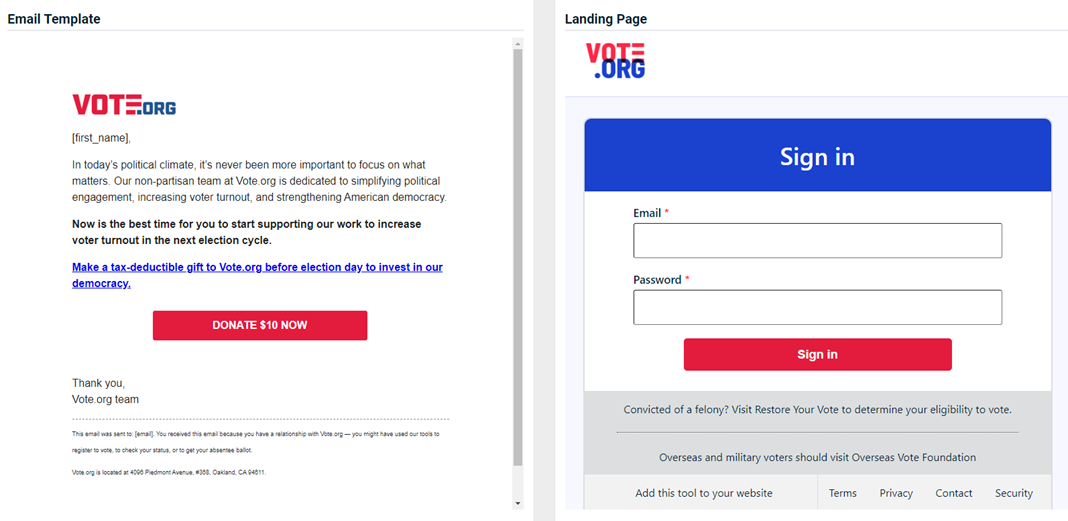
-
Venmo - Gift Card Offer
Previous version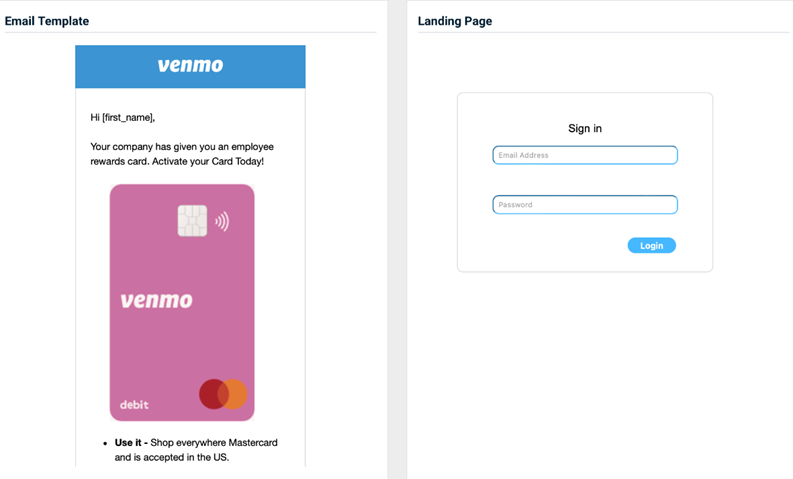
Updated version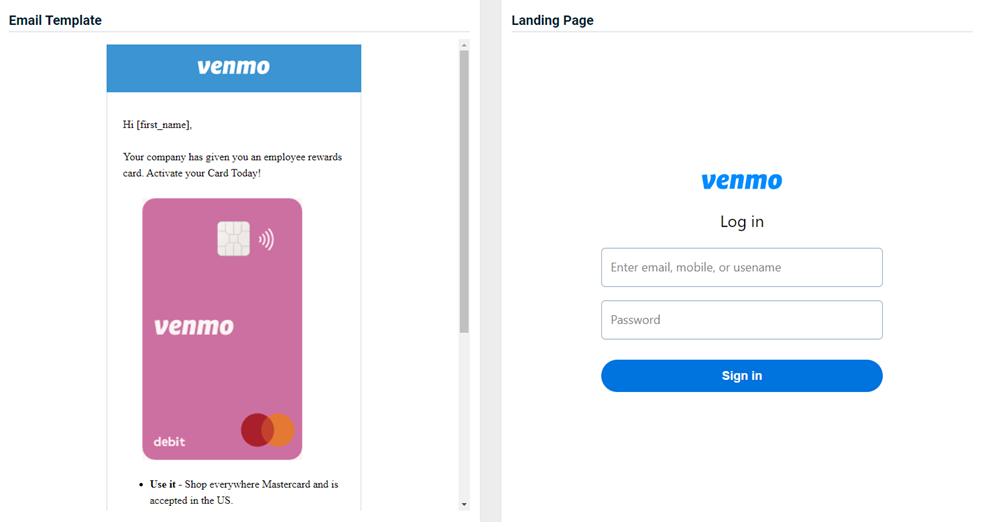
-
Venmo - New Device Alert
Previous version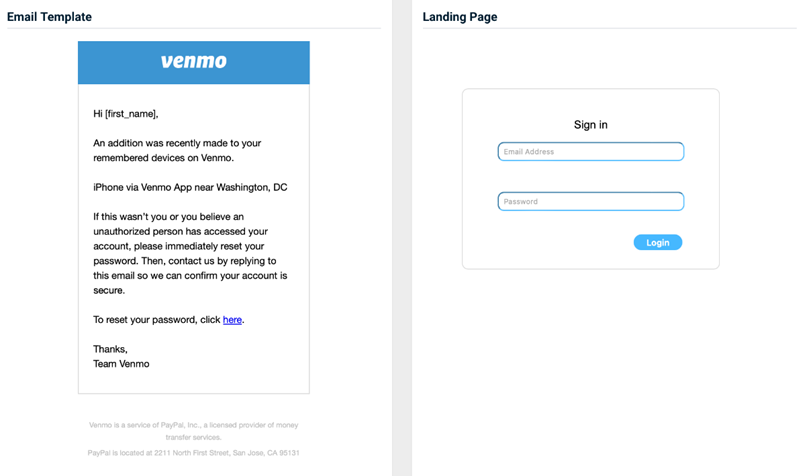
Updated version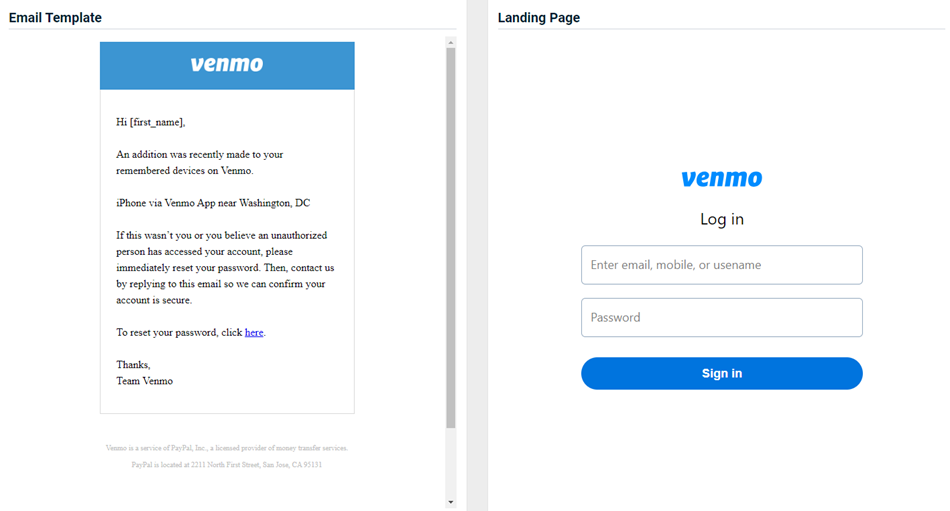
-
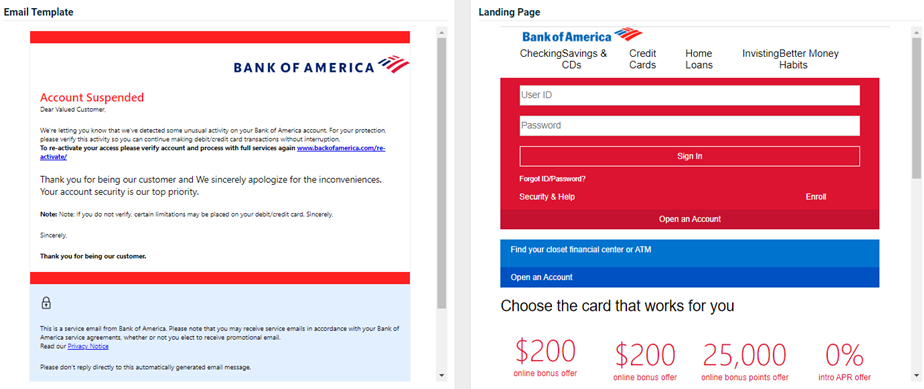
Spotify - Account Suspended
Previous version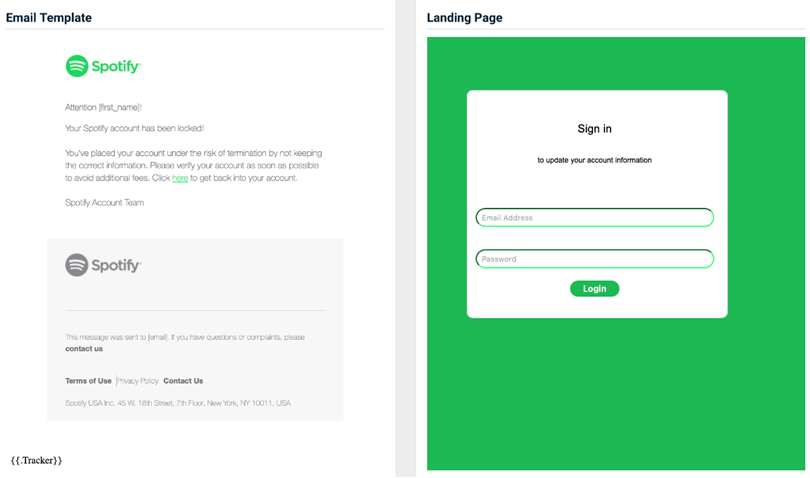
Updated version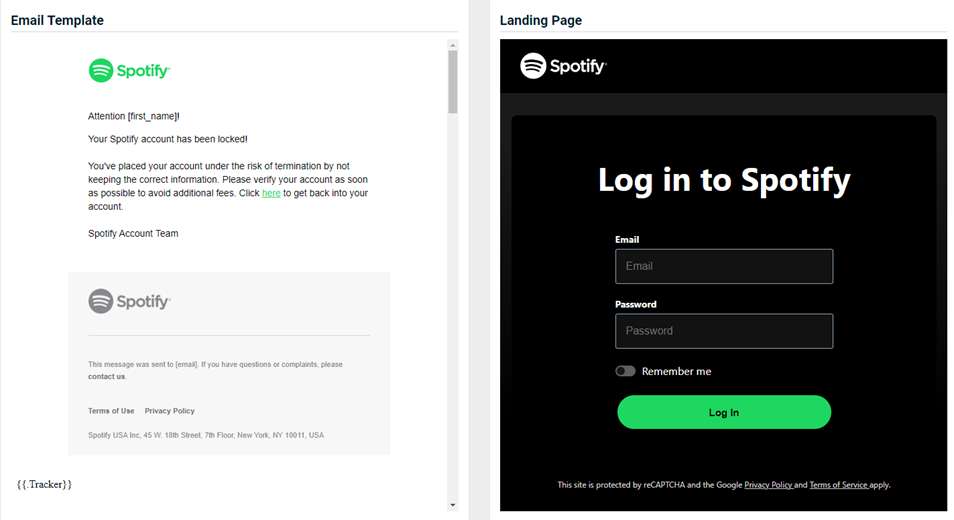
-
Twitter - Locked Account
Previous version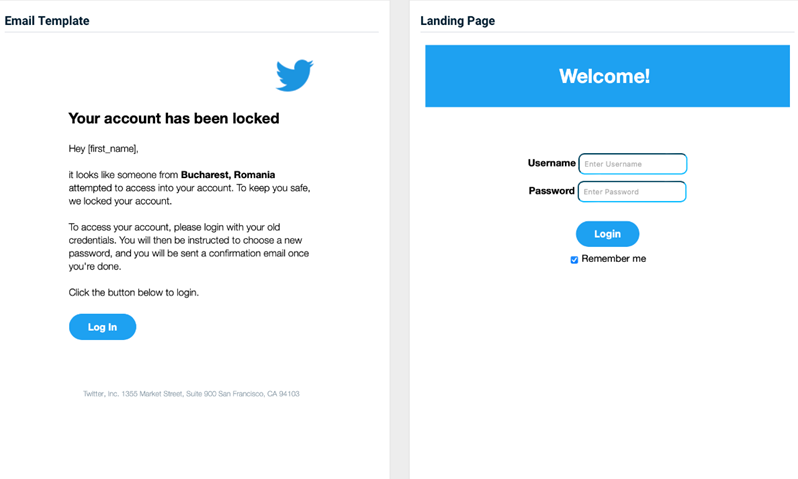
Updated version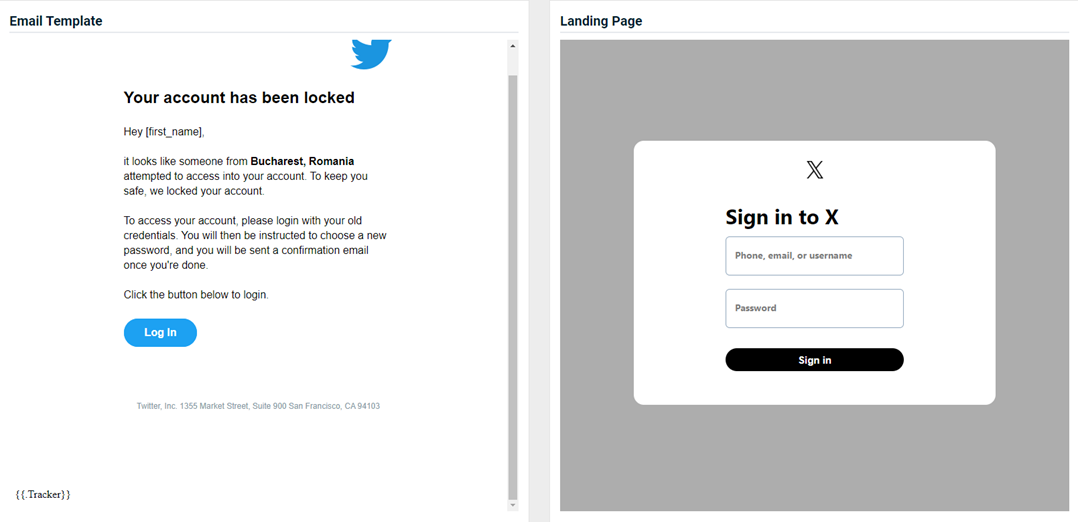
-
Tigerpaw - Assessment Software
Previous version
Updated version
Enhancements
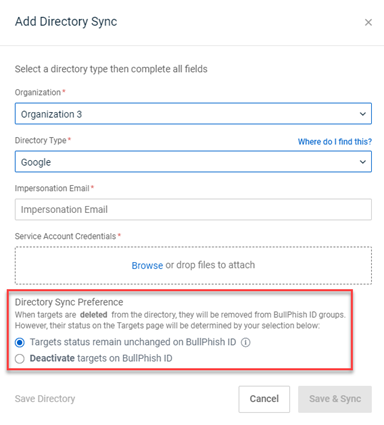
Directory Sync Preference message revised
The message in the Directory Sync Preference modal has been revised to clarify the outcome when targets are deleted from an organization’s directory.
When targets are deleted from an organization’s directory, the targets are automatically removed from the synced BullPhish ID groups. However, each target’s status on the Targets page is determined by selecting one of the following options:
- Targets status remain unchanged on BullPhish ID: (Selected by default) Each target is available on the Targets page in its original Active or Inactive Status.
- Deactivate targets on BullPhish ID: Each target is available on the Targets page with their status updated to Inactive.
Content updates
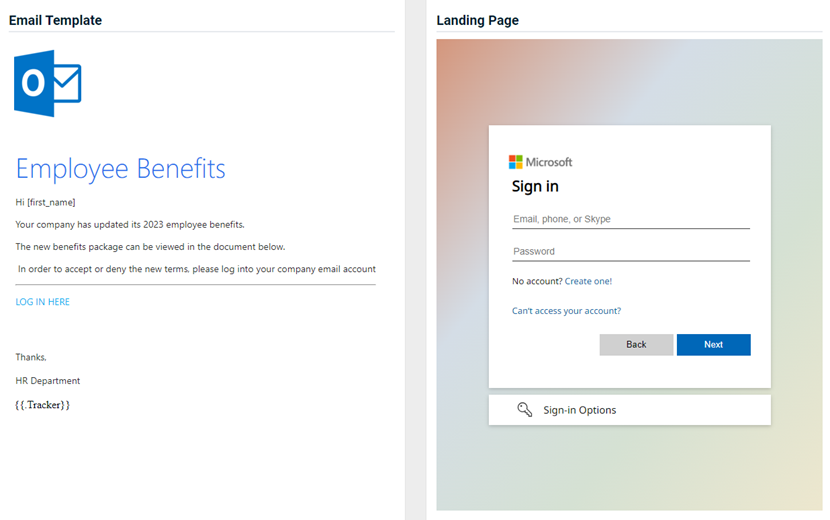
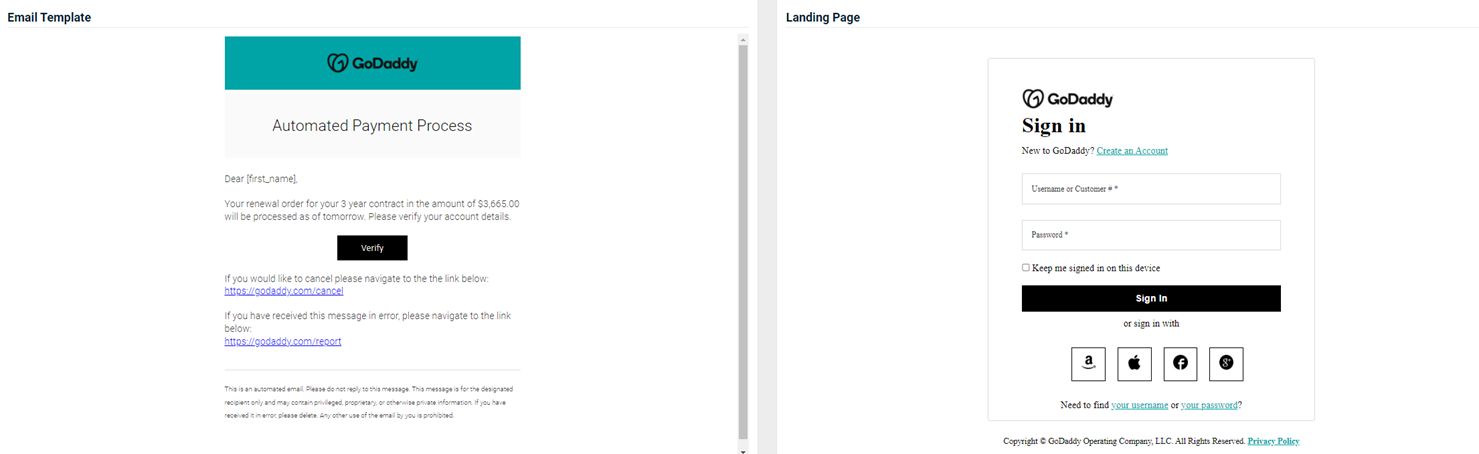
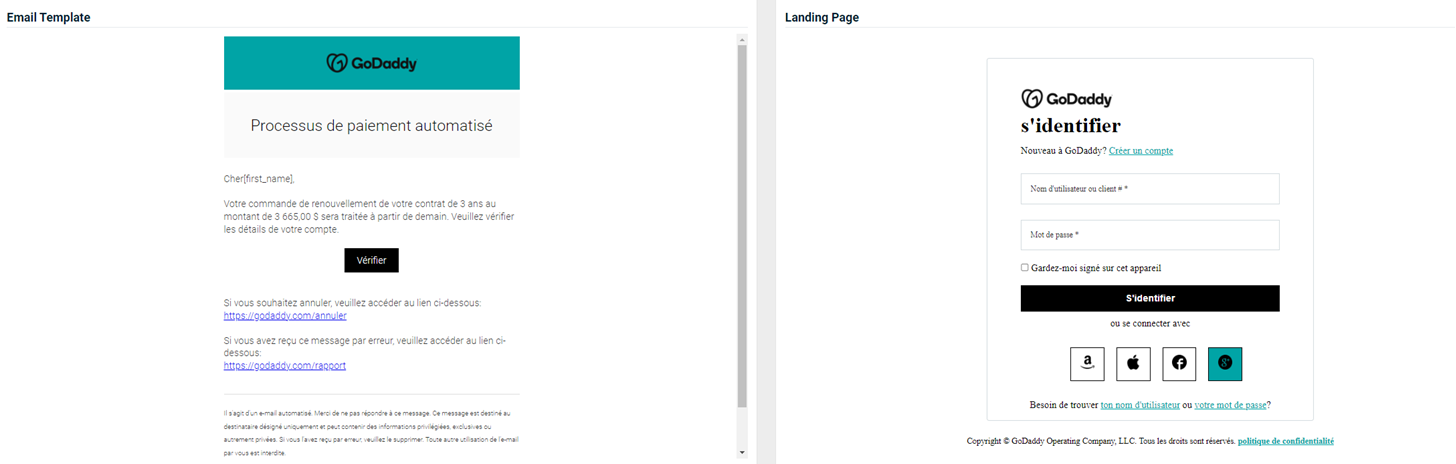
Updated and new phishing kits
Updated and new phishing kits are now available. Each is listed below (links to updated version/new kit) along with an image of its email template and landing page.
- OneDrive – Document Invite
Previous version
Updated version
- SharePoint - Remote Work Policy
Previous version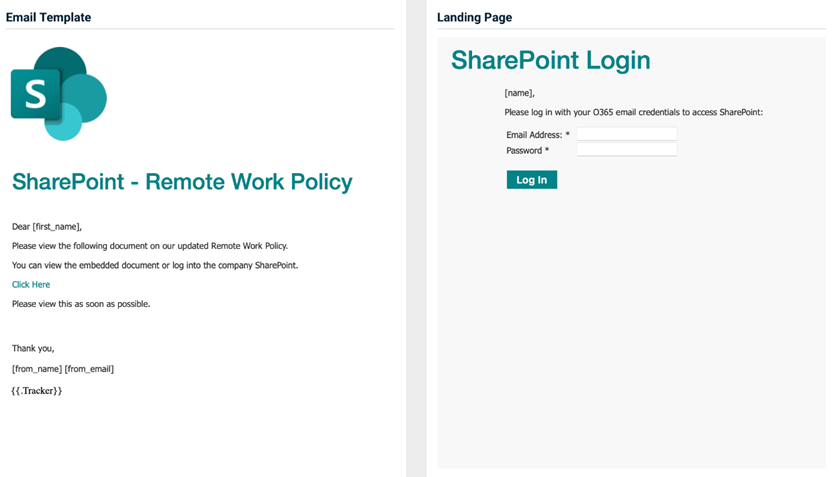
Updated version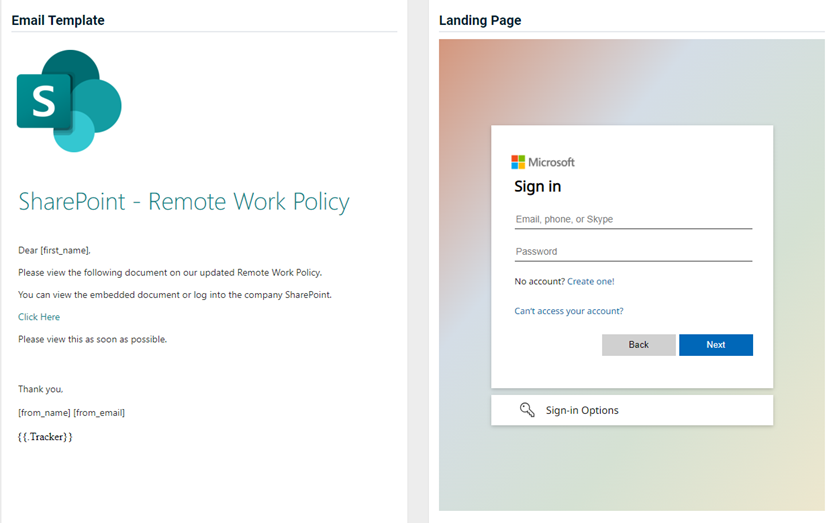
- MyKaplan - Special Offer
Previous version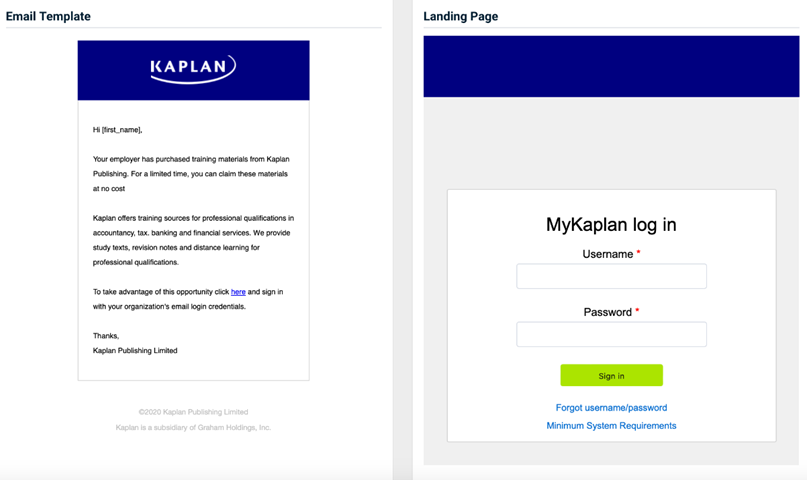
Updated version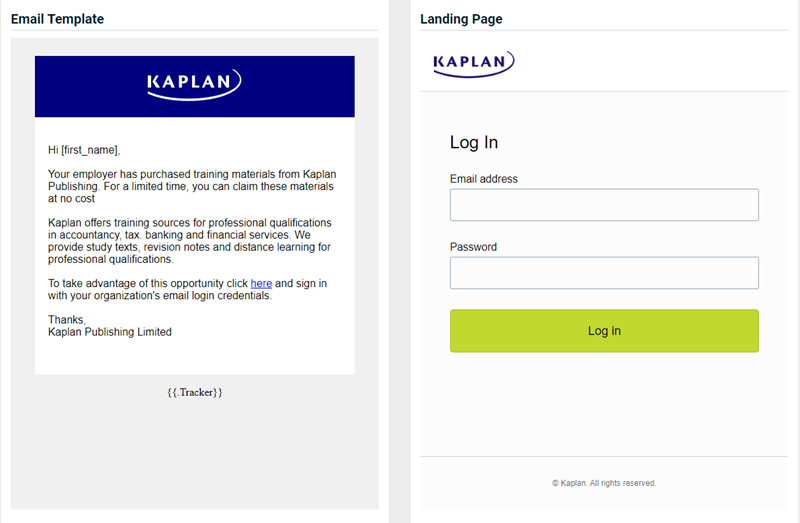
- PayPal – Fraudulent Activity
Previous version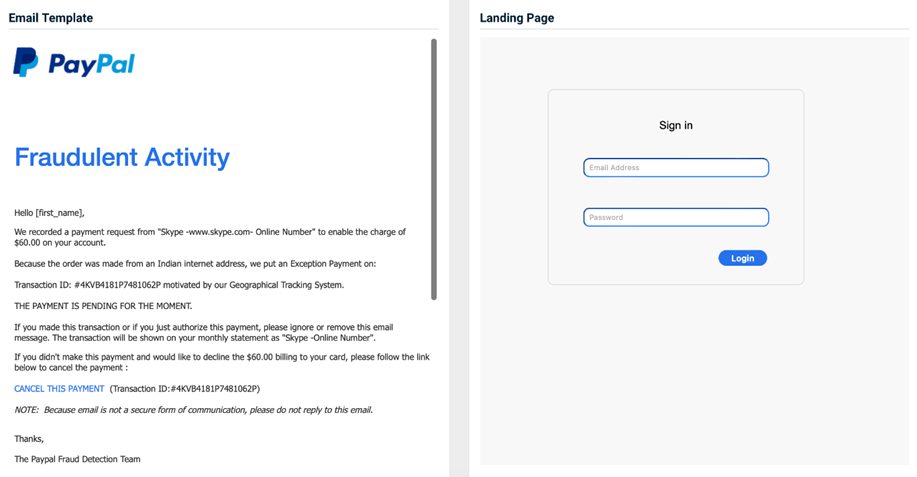
Updated version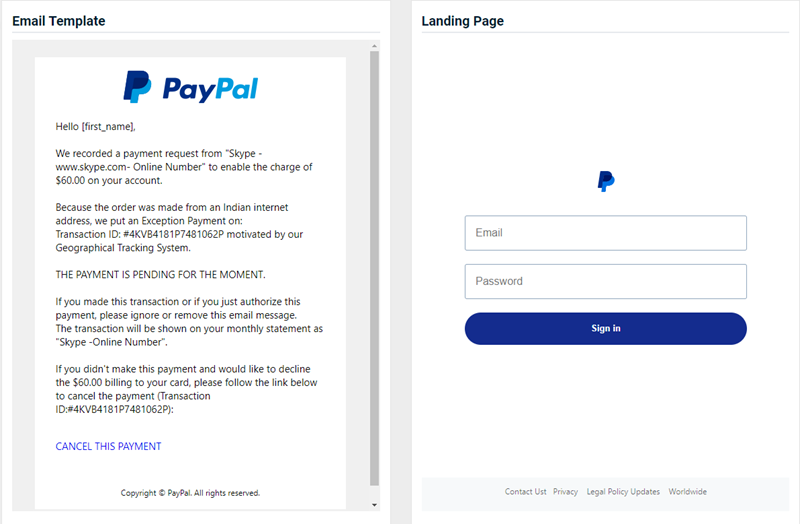
- Schedulicity - Important Message
Previous version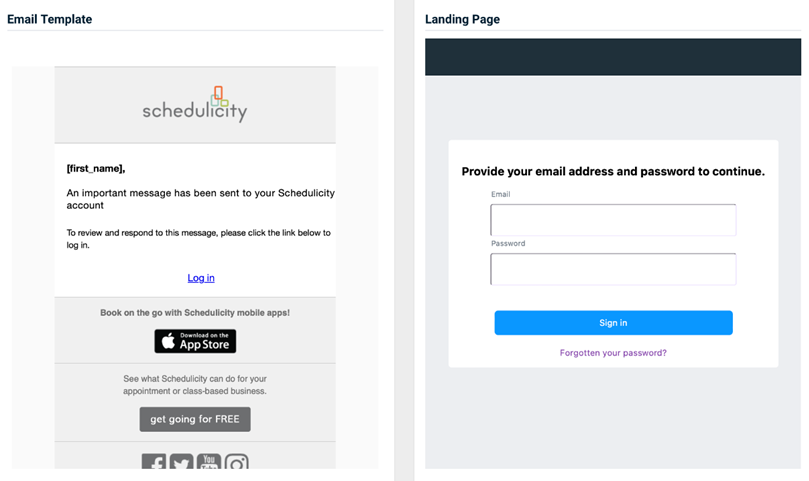
Updated version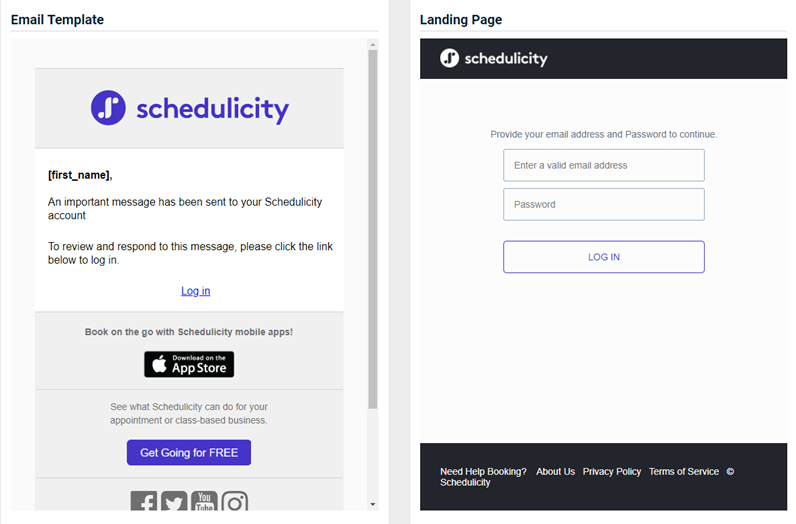
- Staples - Invoice Request
Previous version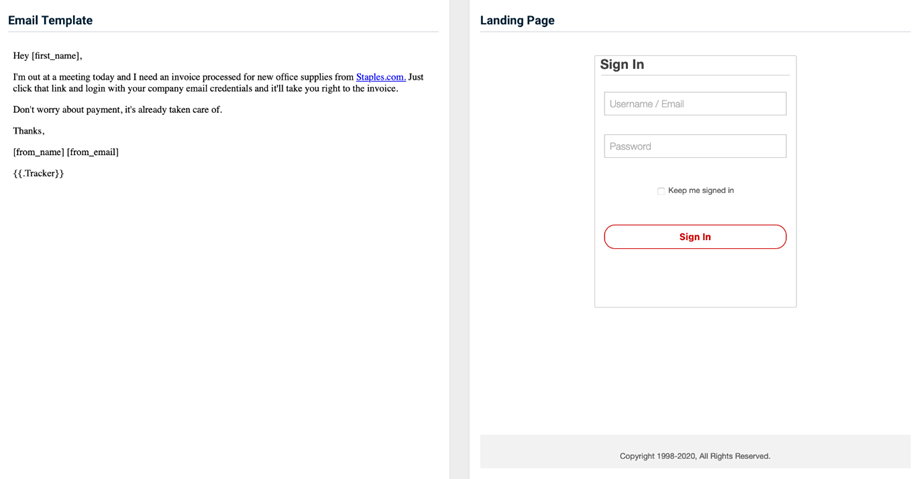
Updated version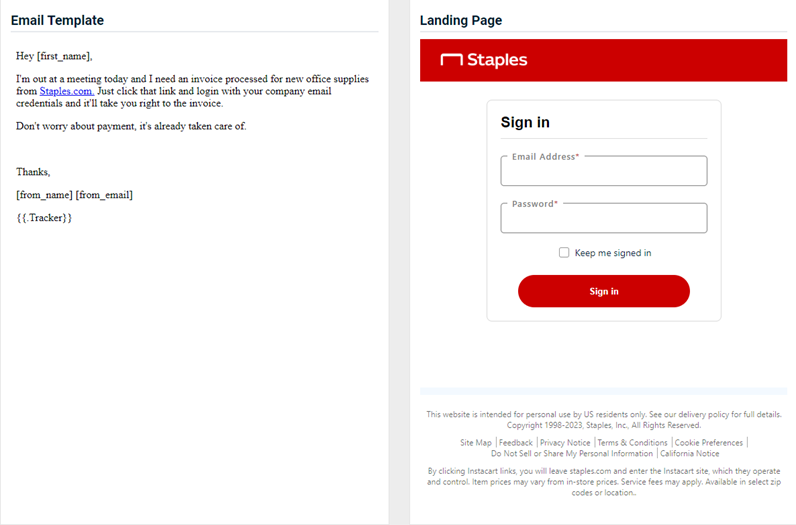
NOTE The following phishing kits are no longer available: Social Security - Future Changes, Social Security Administration - Verification.
Enhancements
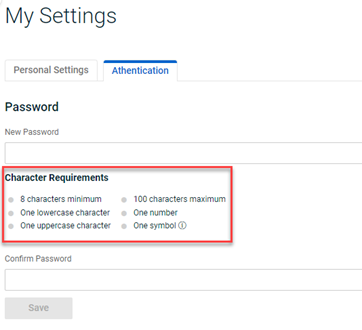
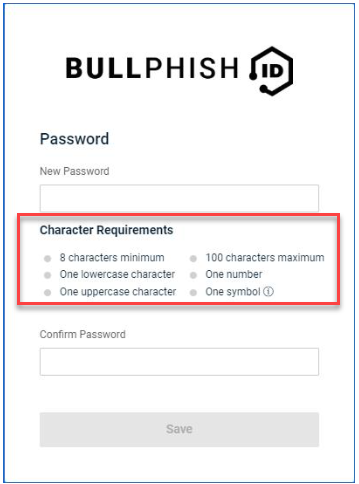
Updated password policy
IMPORTANT Users are not required to update their passwords at this time. Going forward, the new policy will be enforced for new accounts and password resets.
Enhanced BullPhish ID password requirements have been implemented to ensure better security. The password requirements apply to DarkWeb ID as well.
The password policy requirements are listed below, with new requirements listed in bold:
- Minimum of 8 characters in length.
- Maximum of 100 characters in length.
- Minimum of 1 lowercase character (new).
- Minimum of 1 uppercase character.
- Minimum of 1 number.
- Minimum of 1 symbol (A tooltip in the password modal identifies the acceptable characters.).
- Cannot include a username.
- Last three passwords cannot be reused.
The password policy requirements are displayed on the following pages:
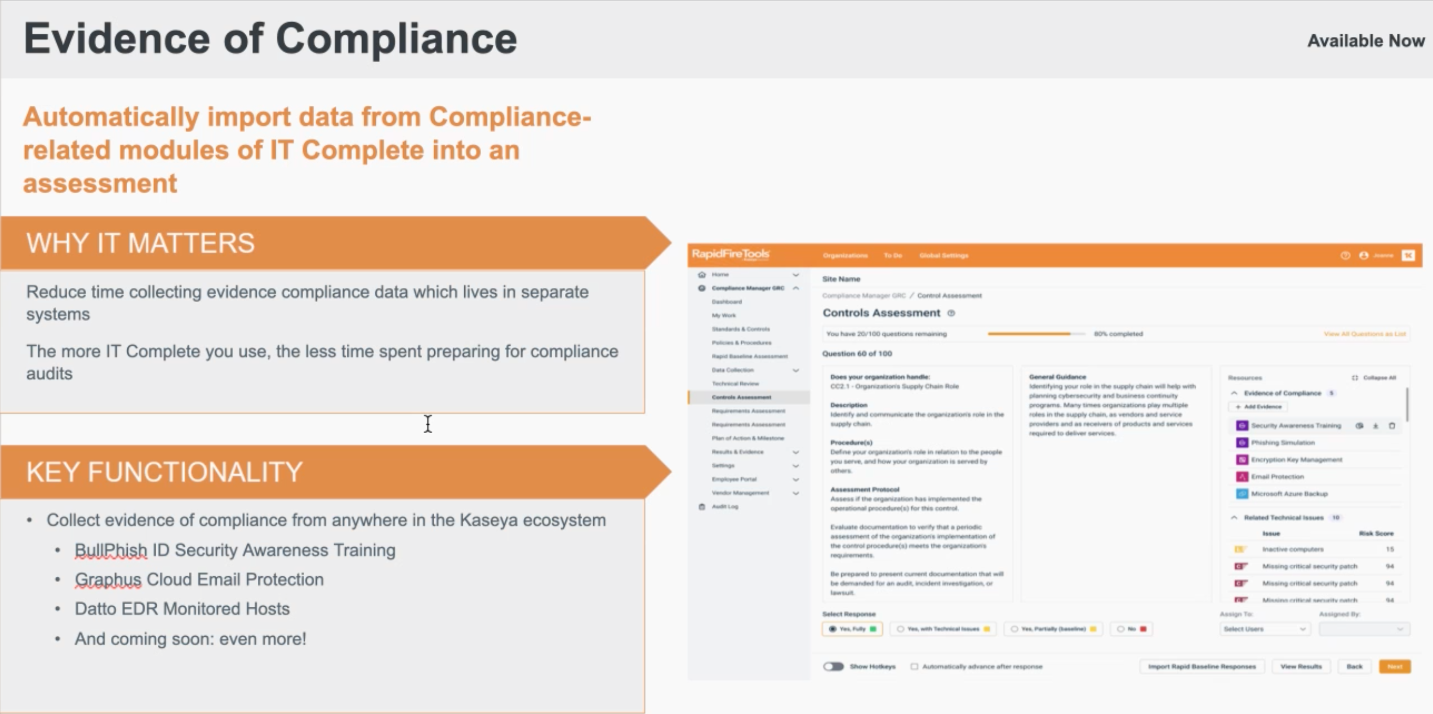
New integration
The Compliance Manager GRC Integration is now live. Compliance Manager GRC users will gain significant advantages by automatically importing proof of security awareness training from BullPhish ID. This will result in:
- Reduce time collecting evidence compliance data which lives in separate systems;
- The more IT Complete you use, the less time spent preparing for compliance audits;
- Details available to prove that they are actively conducting security awareness trainings: Name, Course Name, and Date Passed.
For more information, see the article Evidence of Compliance Integration.
Content updates
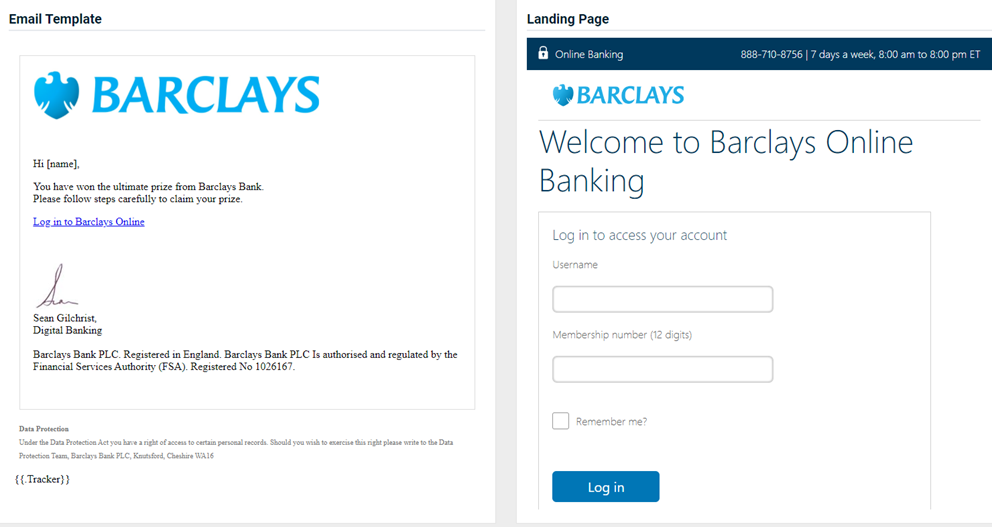
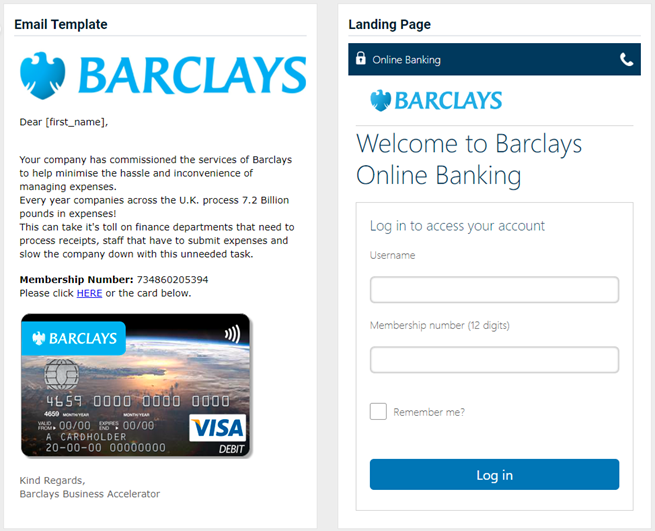
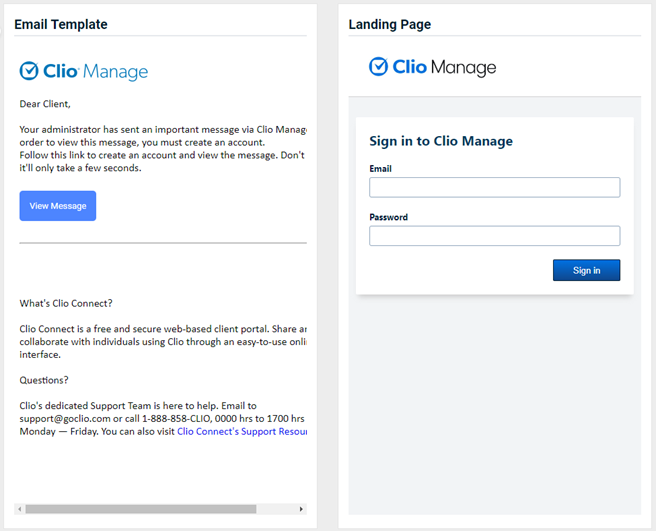
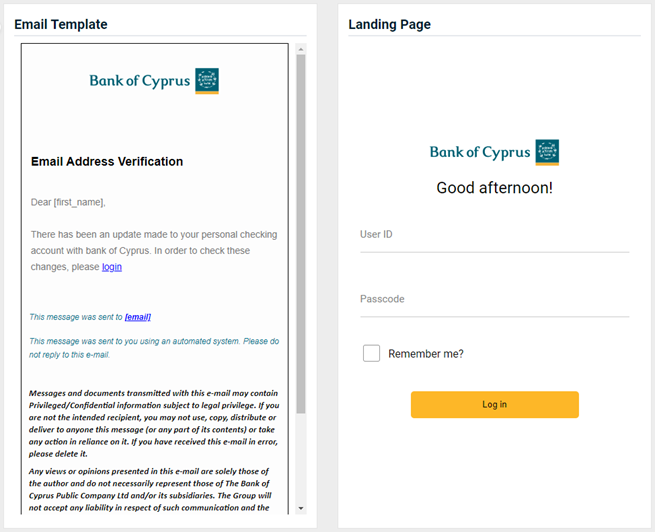
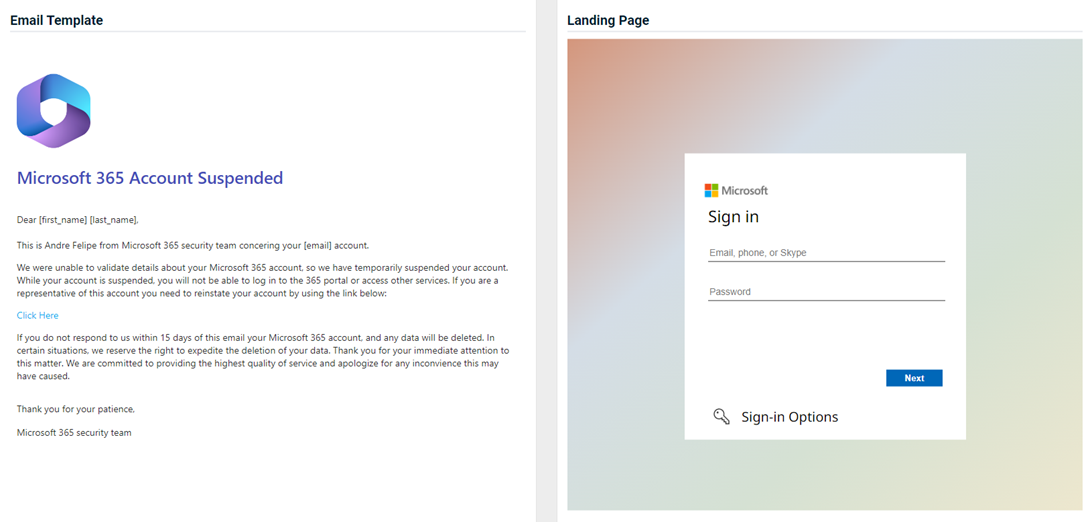
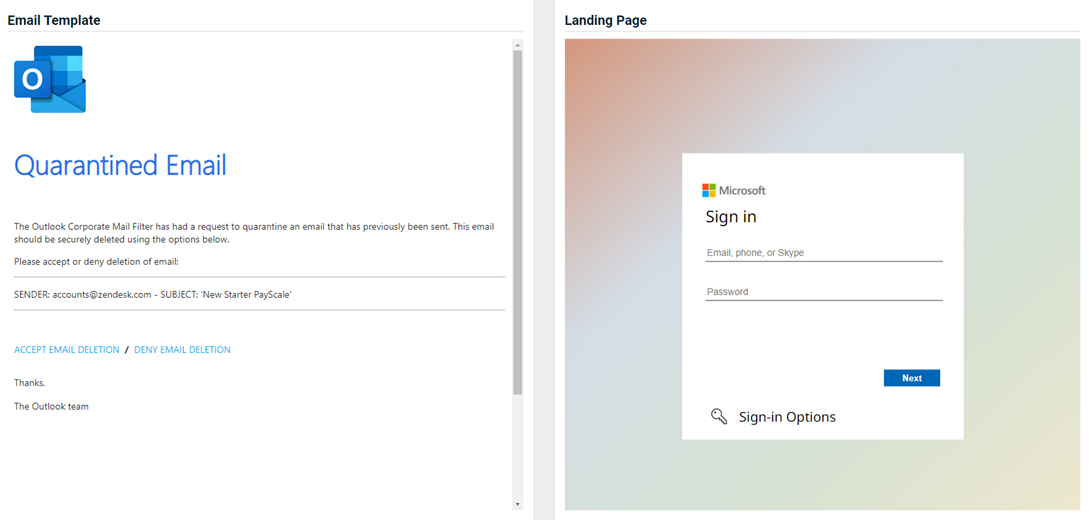
Updated and new phishing kits
Updated and new phishing kits are now available. Each is listed below (links to updated version/new kit) along with an image of its email template and landing page.
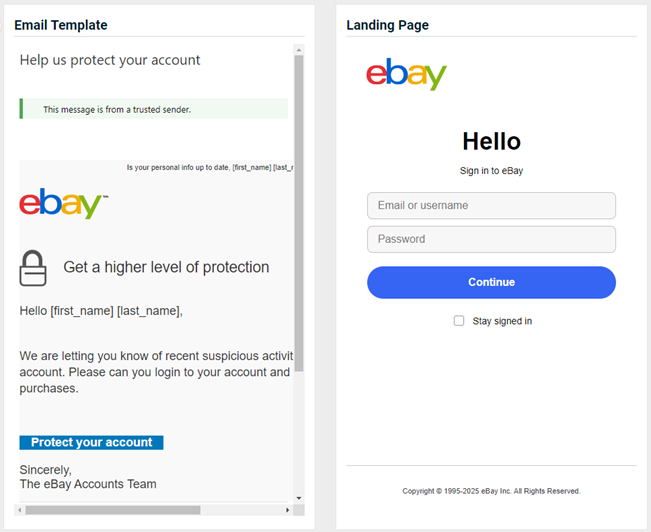
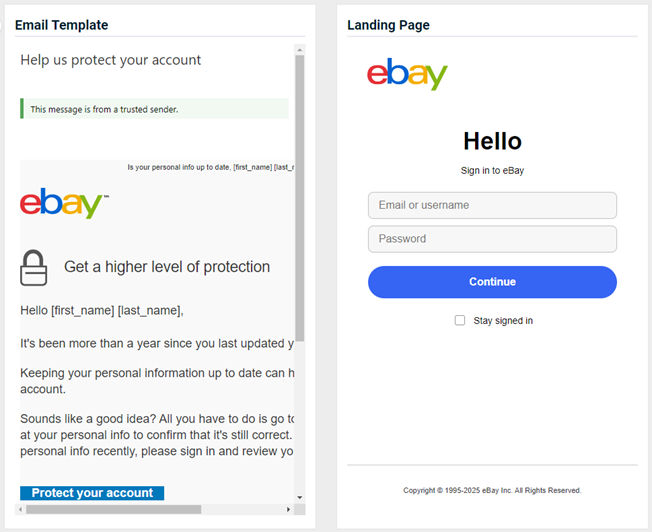
- Chase Bank - Account Closed
Previous version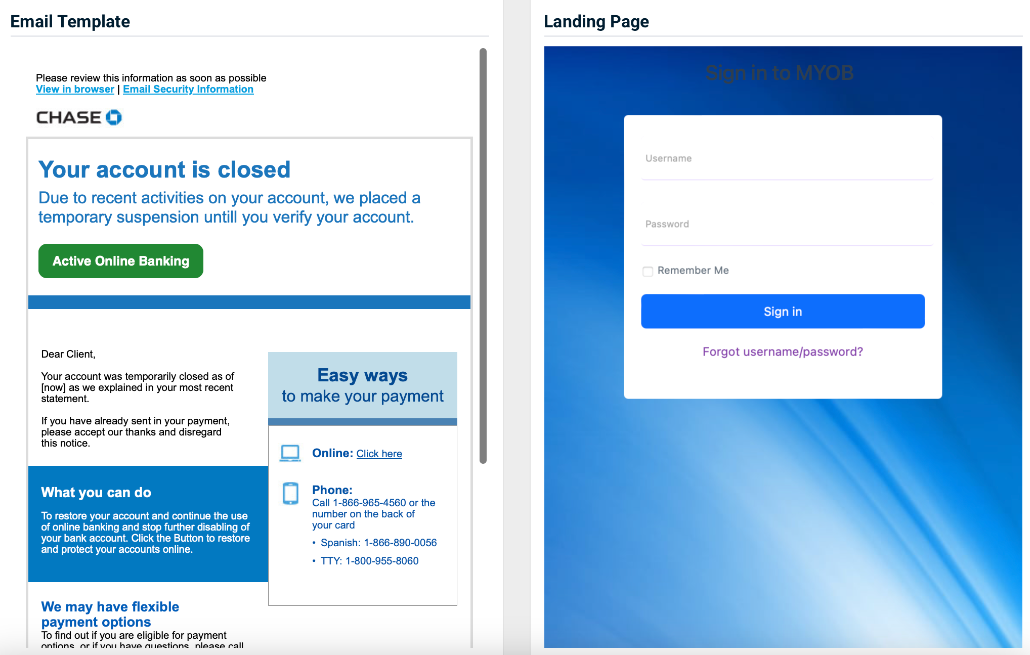
Updated version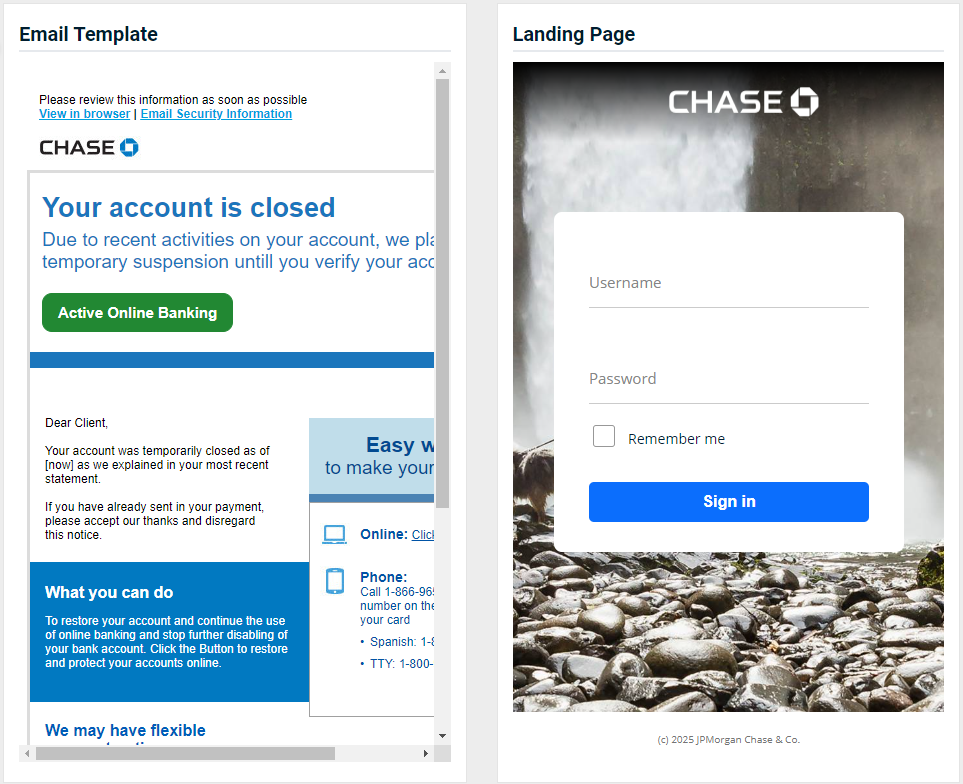
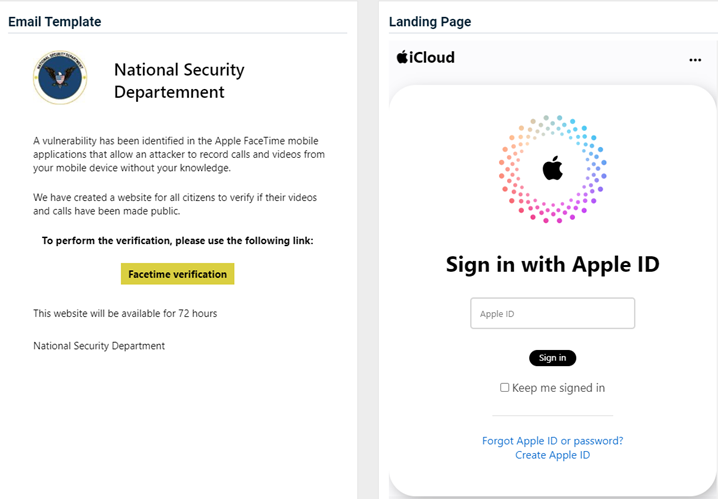
- iCloud - Storage Full
Previous version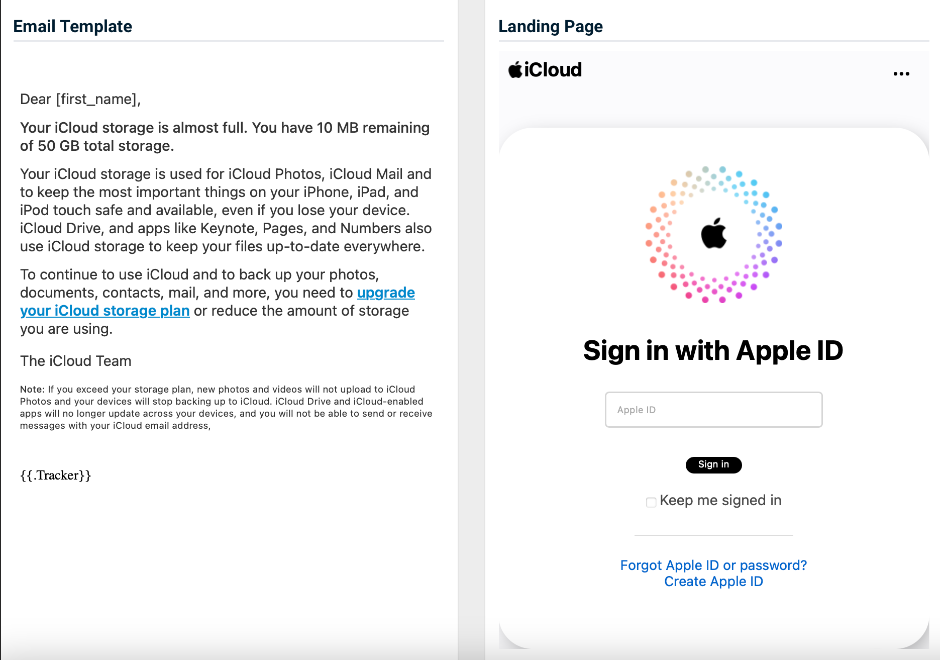
Updated version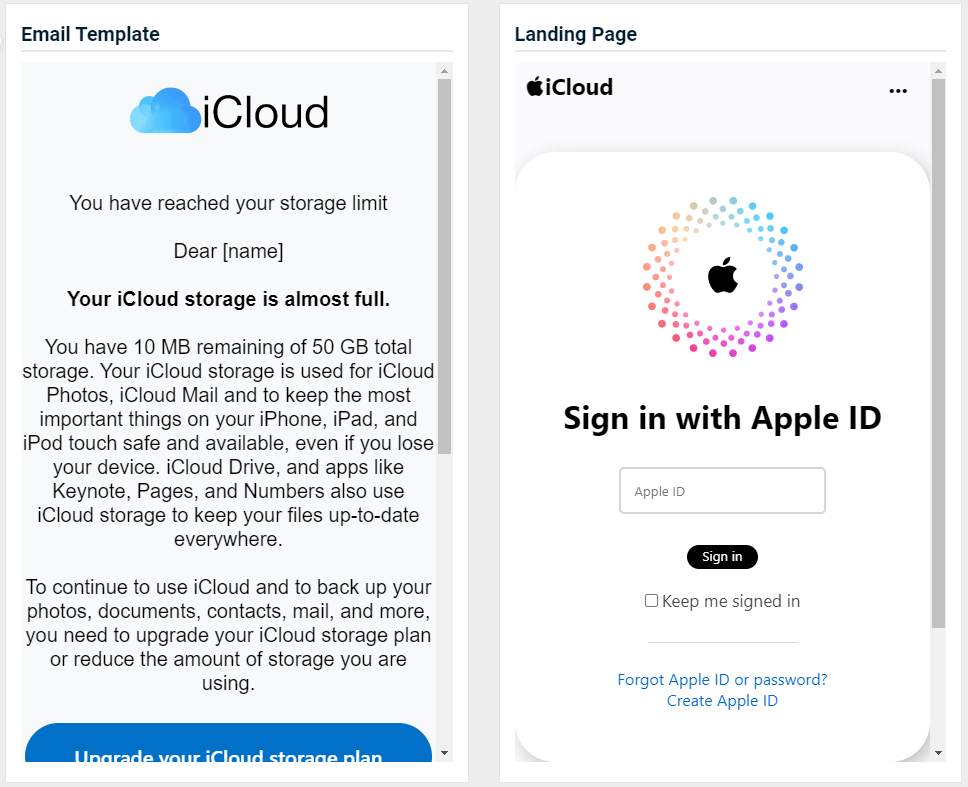
- McAfee - Antivirus Disabled
Previous version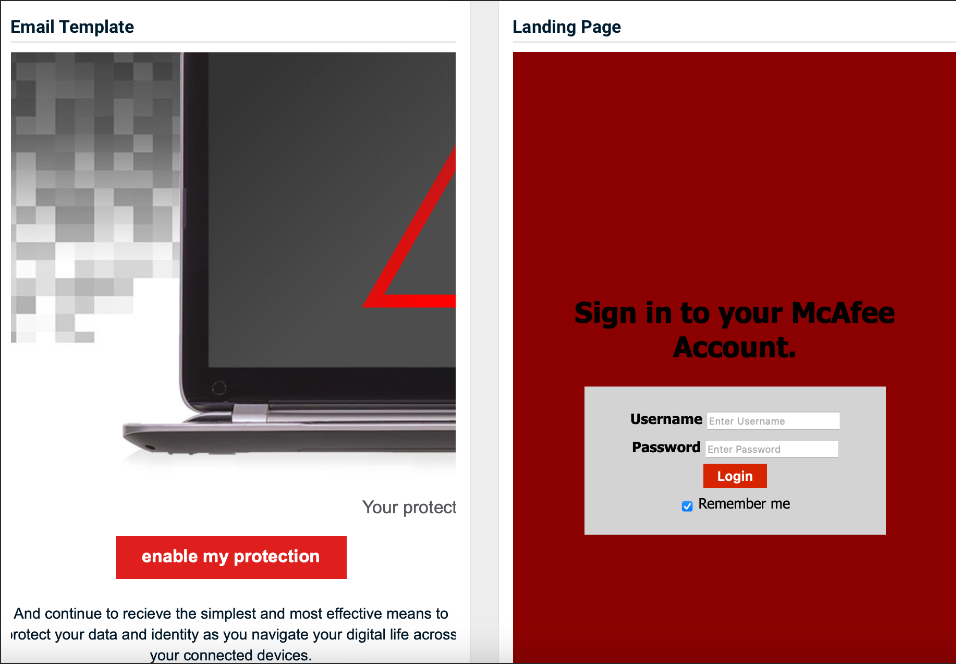
Updated version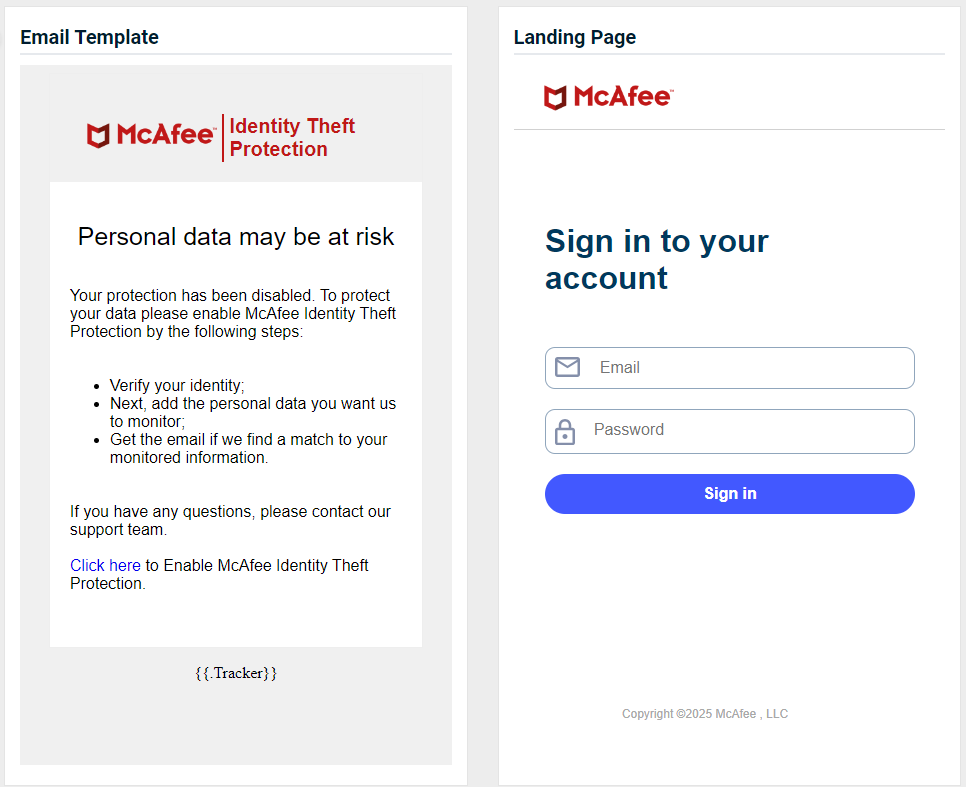
- H&R Block - Verify Email
Previous version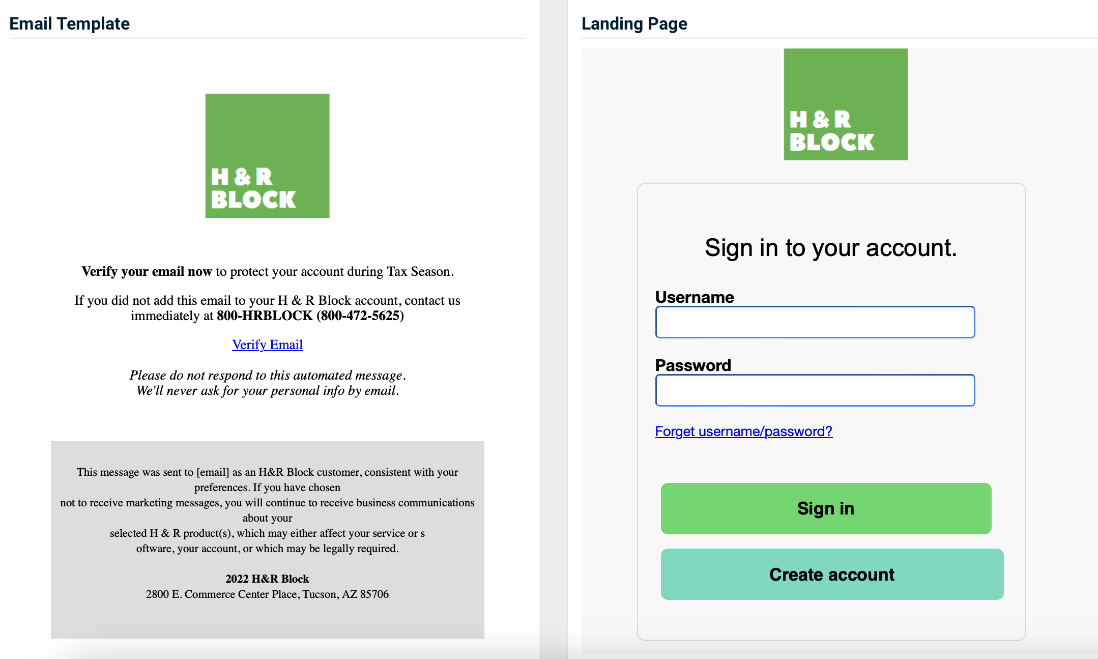
Updated version
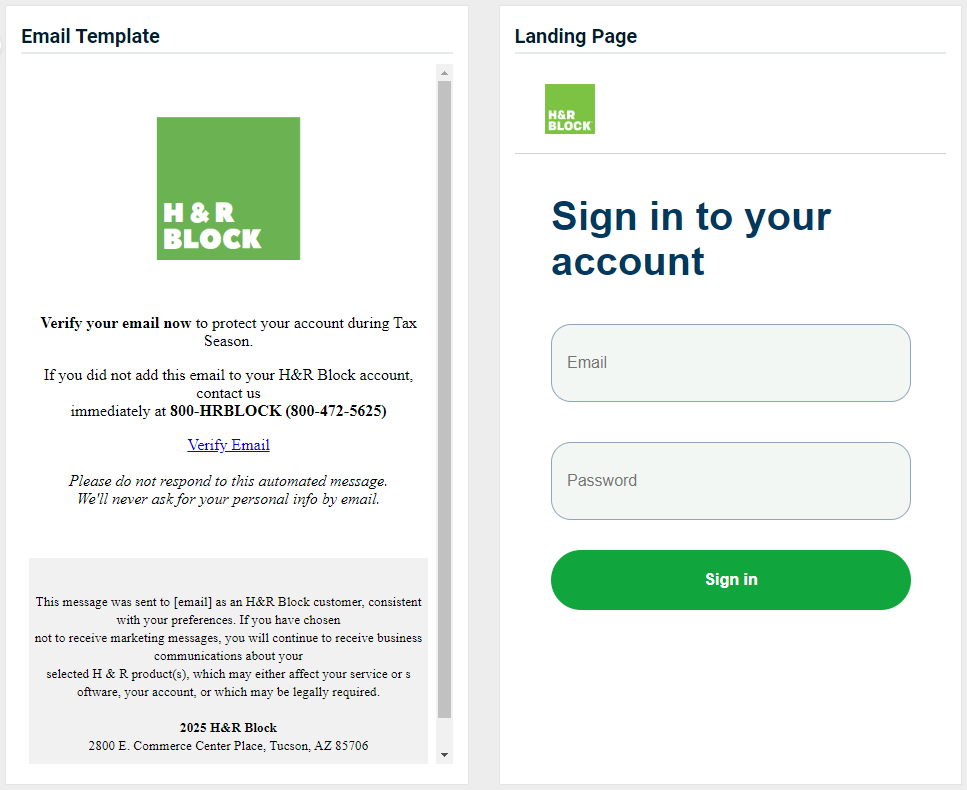
- Office 365 Password Notification
Previous version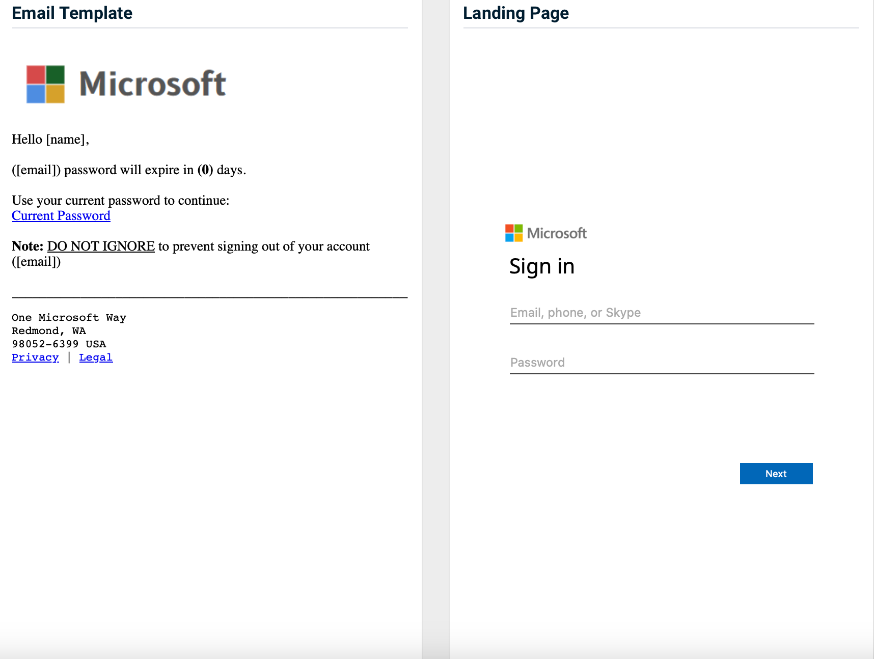
Updated version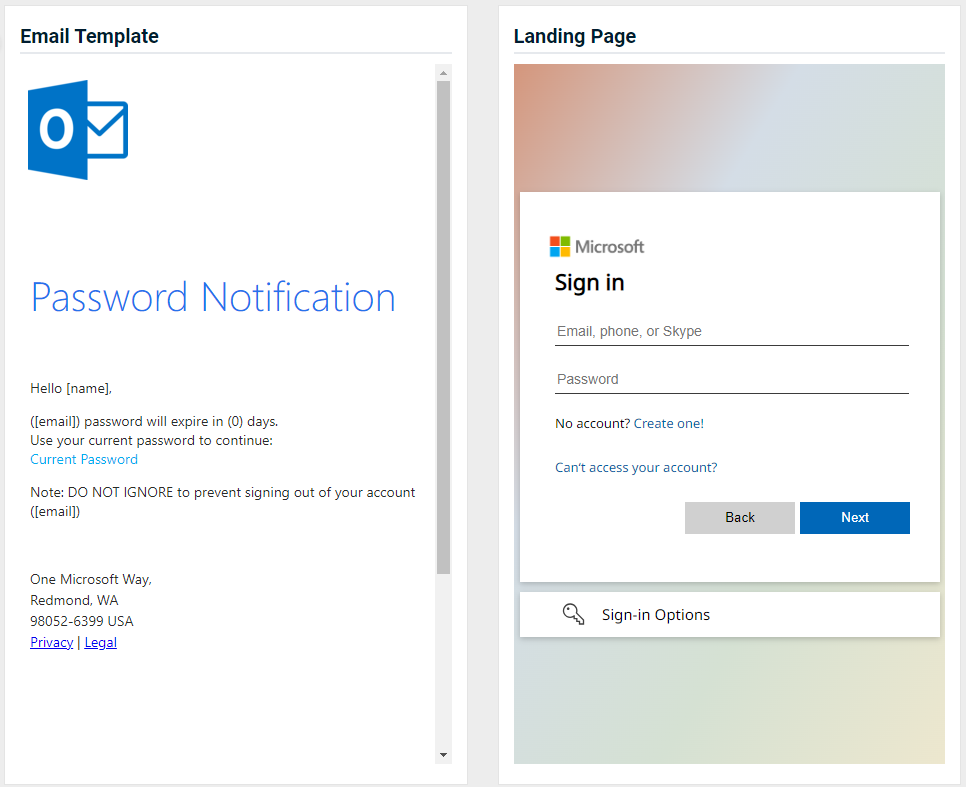
- Office 365 - Suspicious Login
Updated version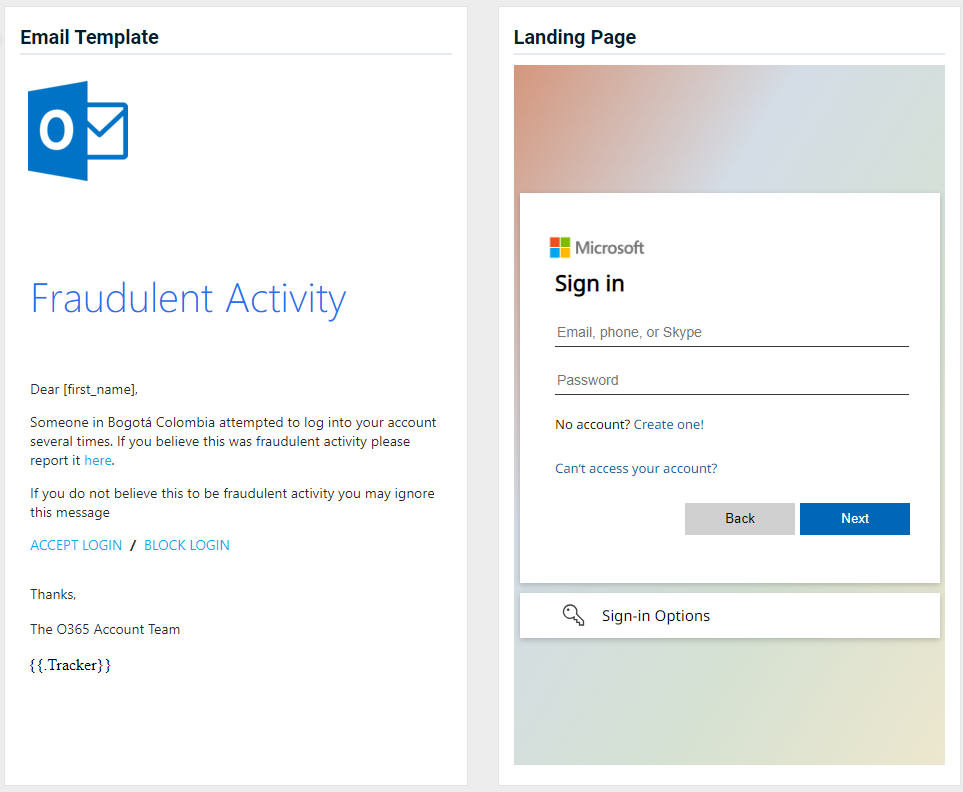
- Office 365 - Exchange Service Outage
Updated version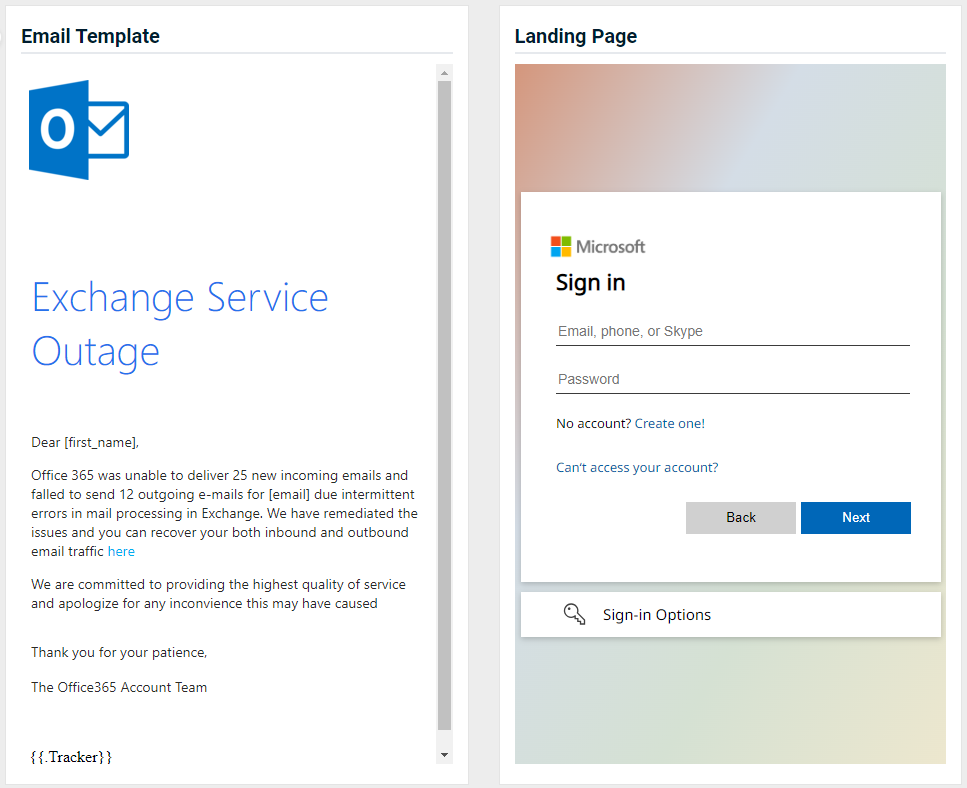
- Office 365 - Suspension Notice
Updated version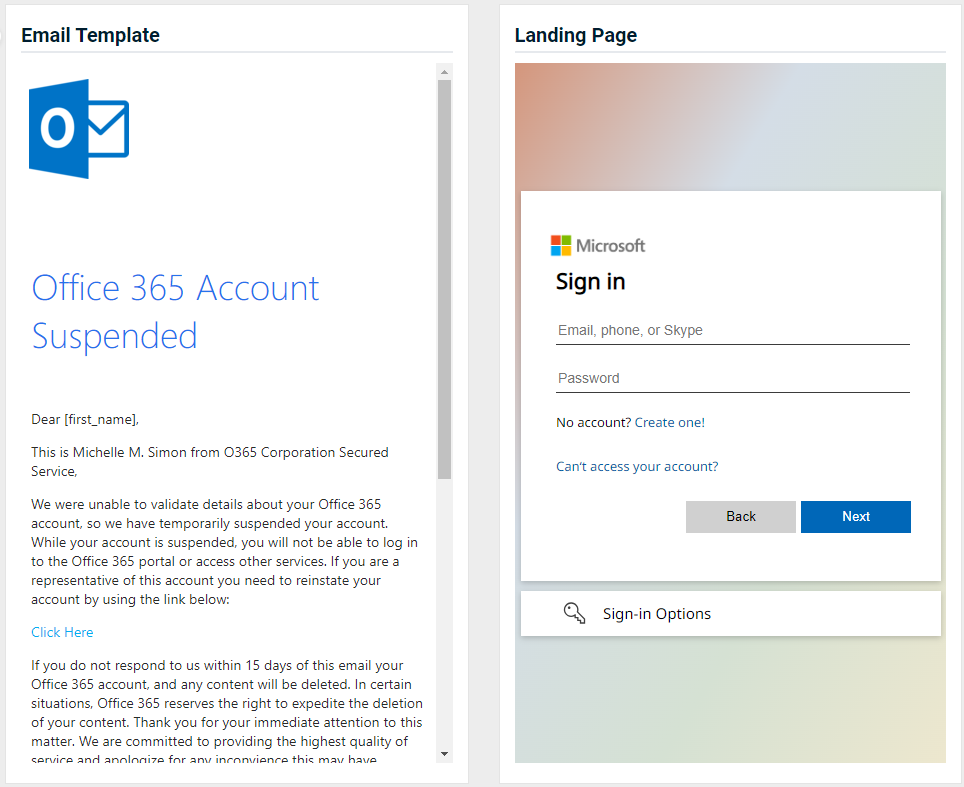
- Office 365 Re-Authentication Detection
Previous version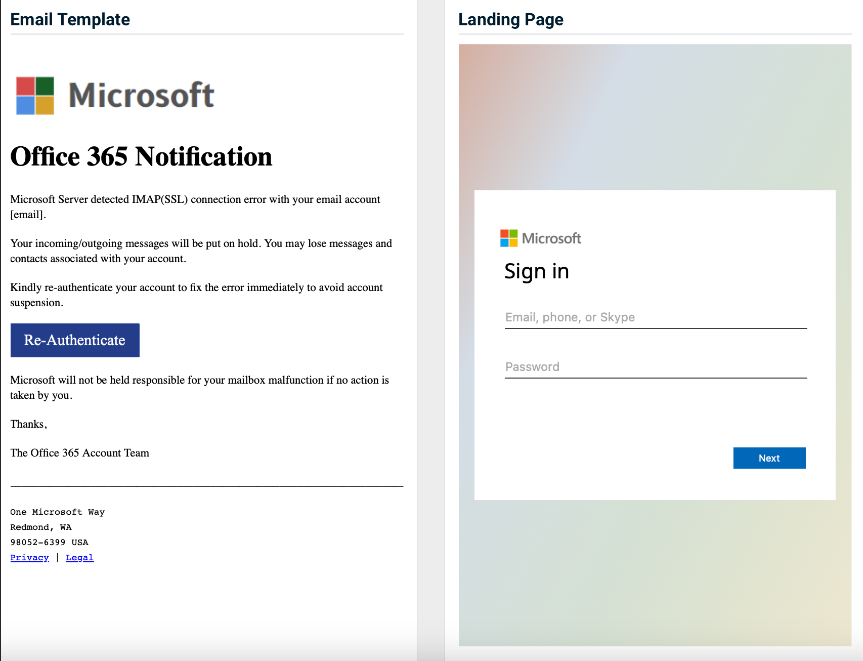
Updated version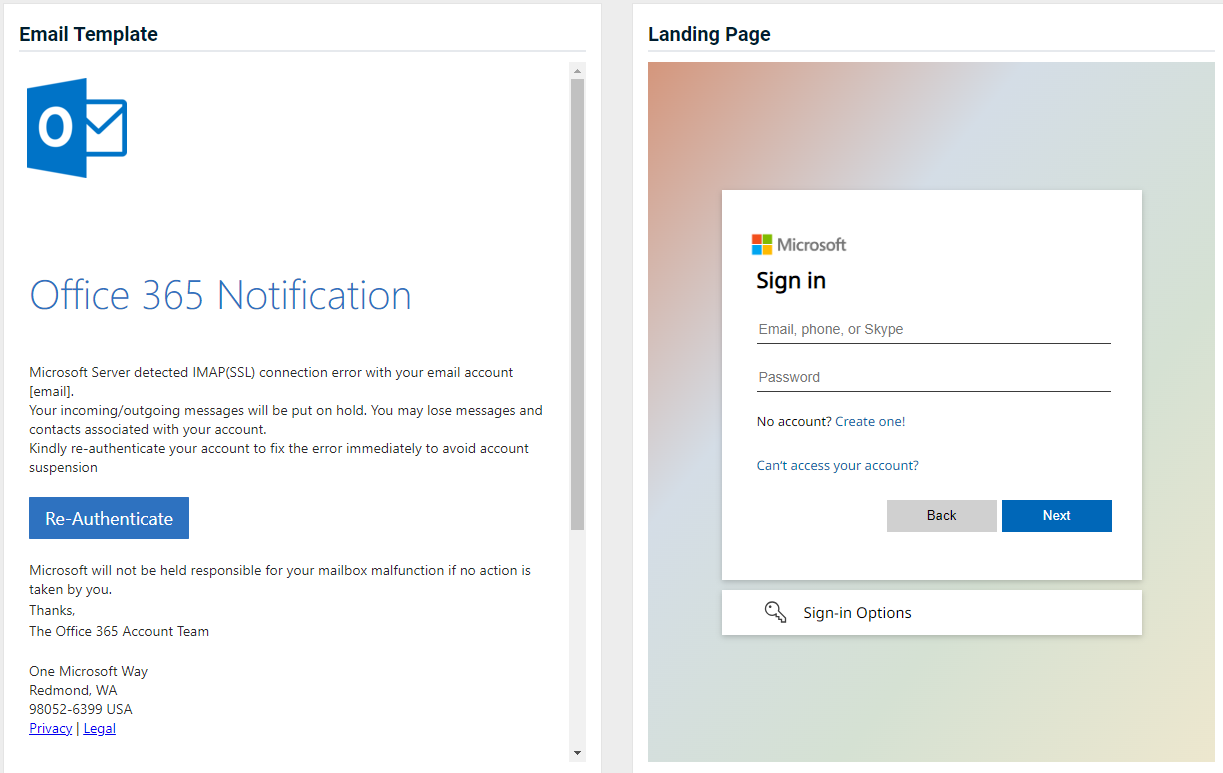
- Netflix - Update Account
Previous version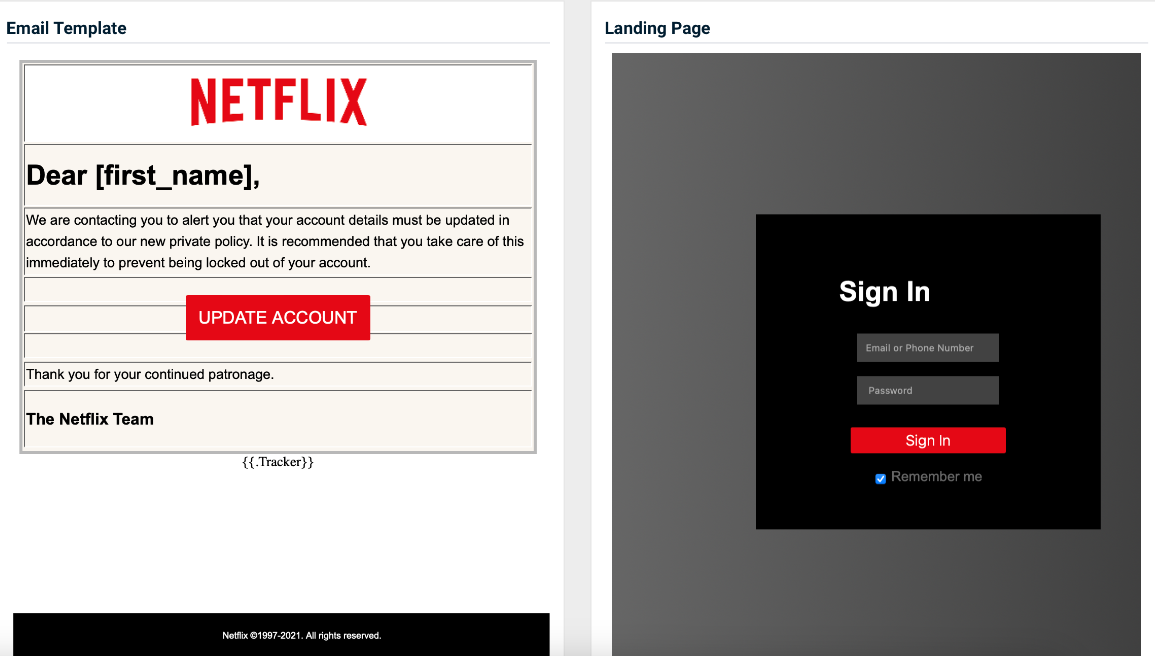
Updated version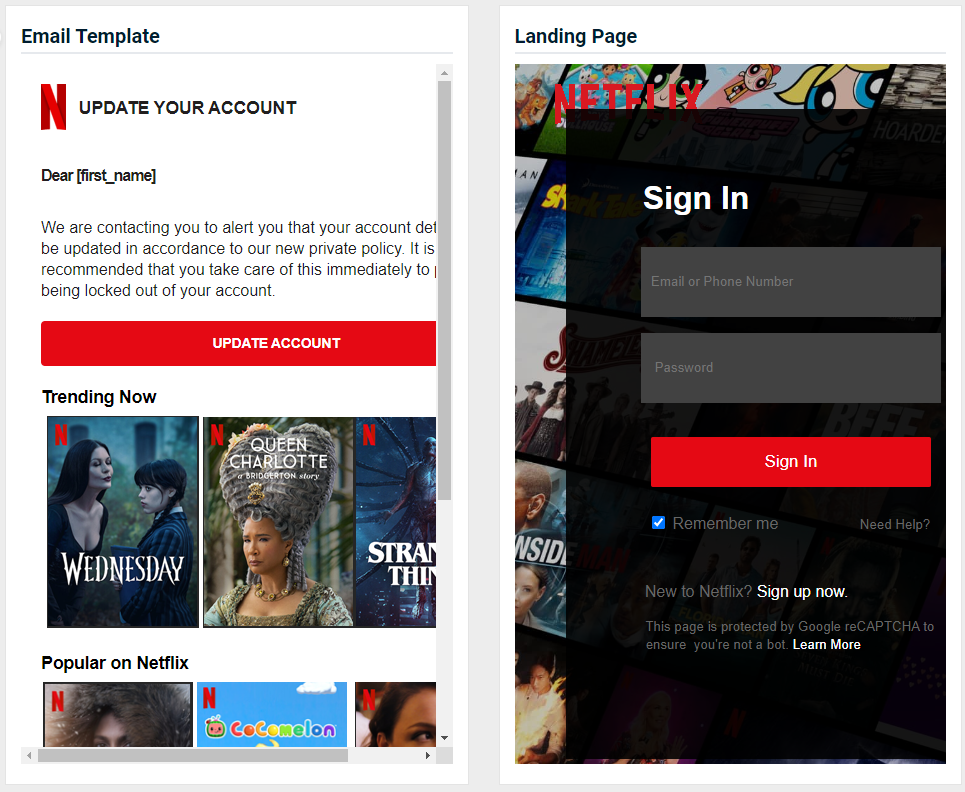
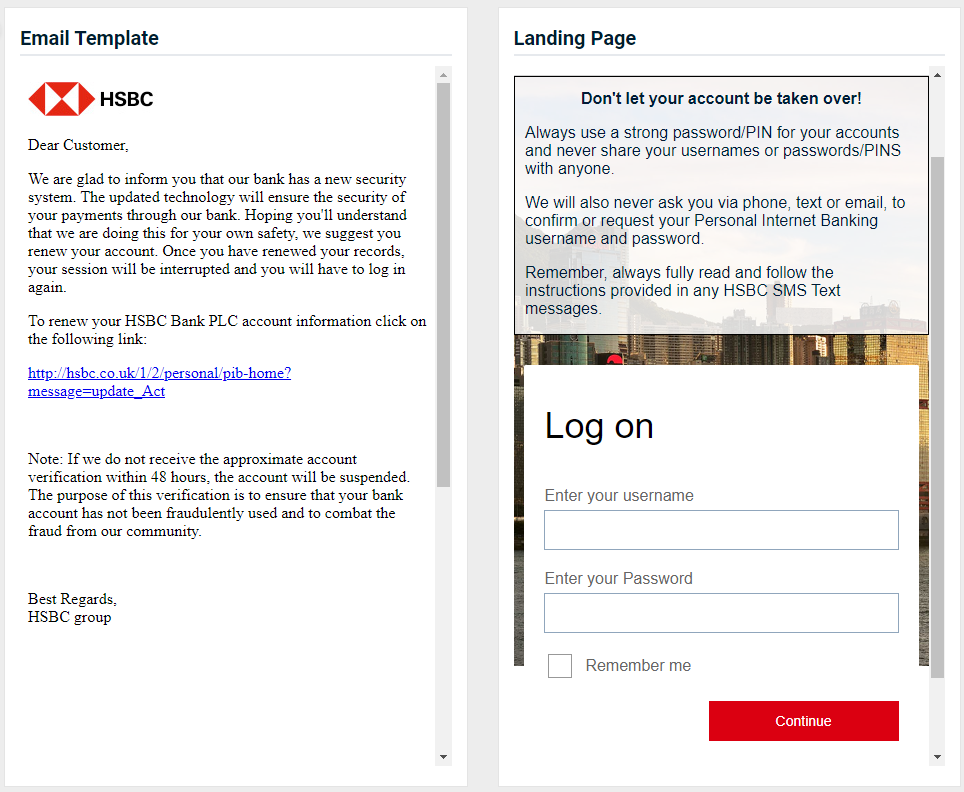
- HSBC – Security Improvement v1 (available along with new v2 below)
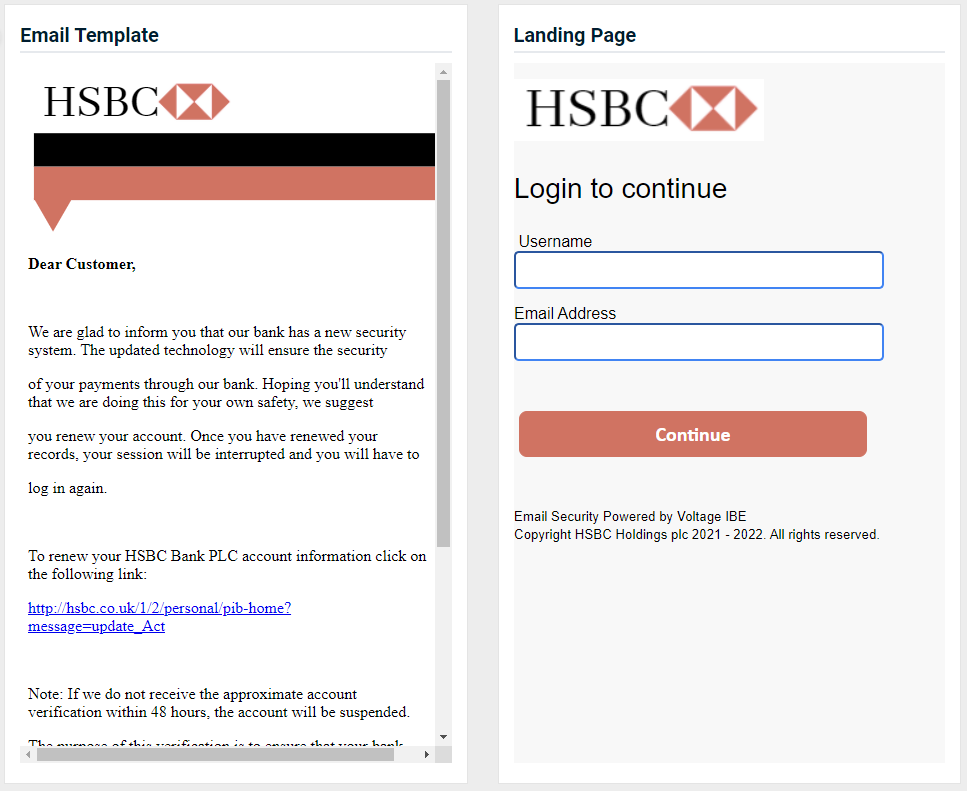
- HSBC – Security Improvement v2 (New)
- OneDrive – Changes to OneDrive
Previous version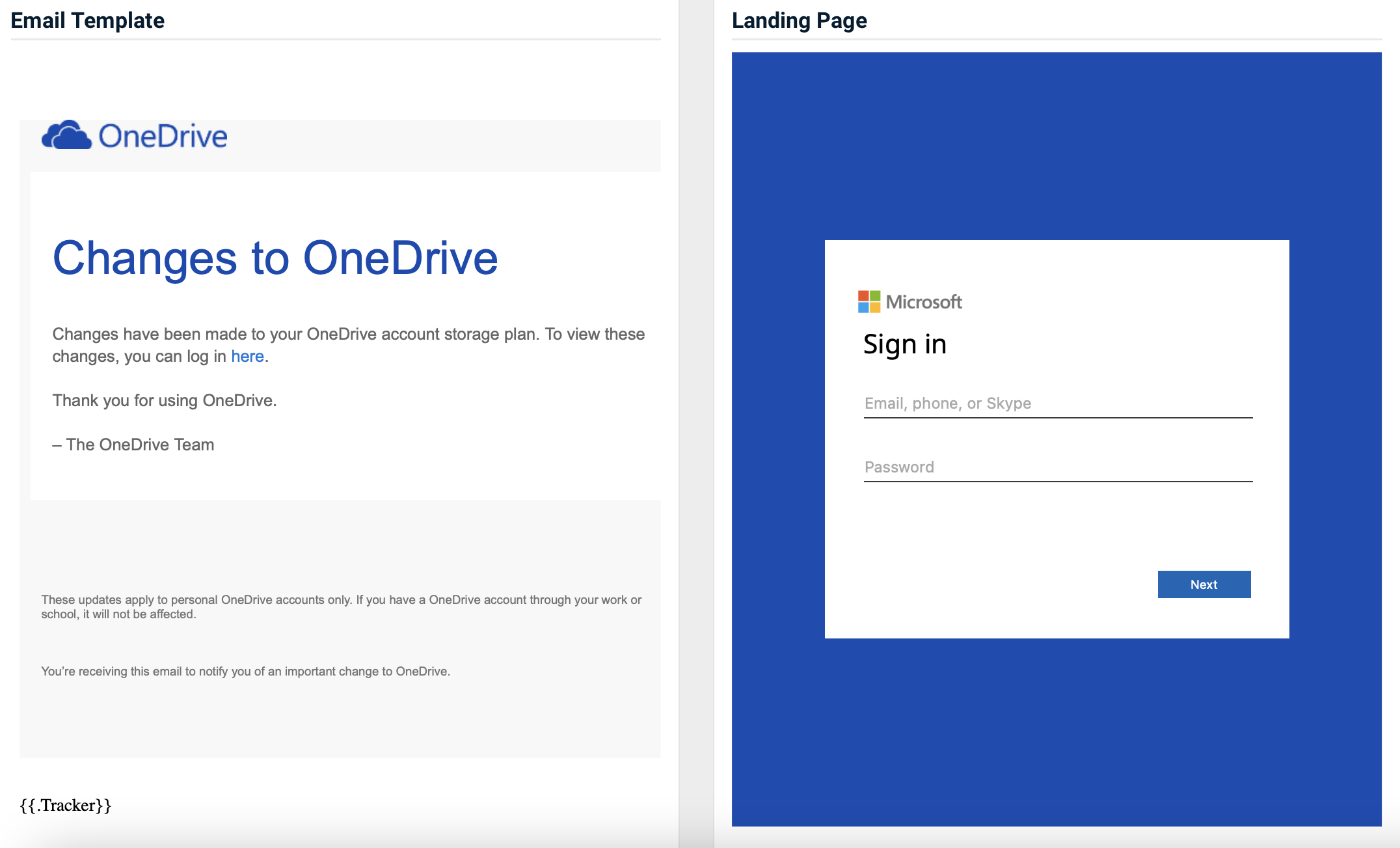
Updated version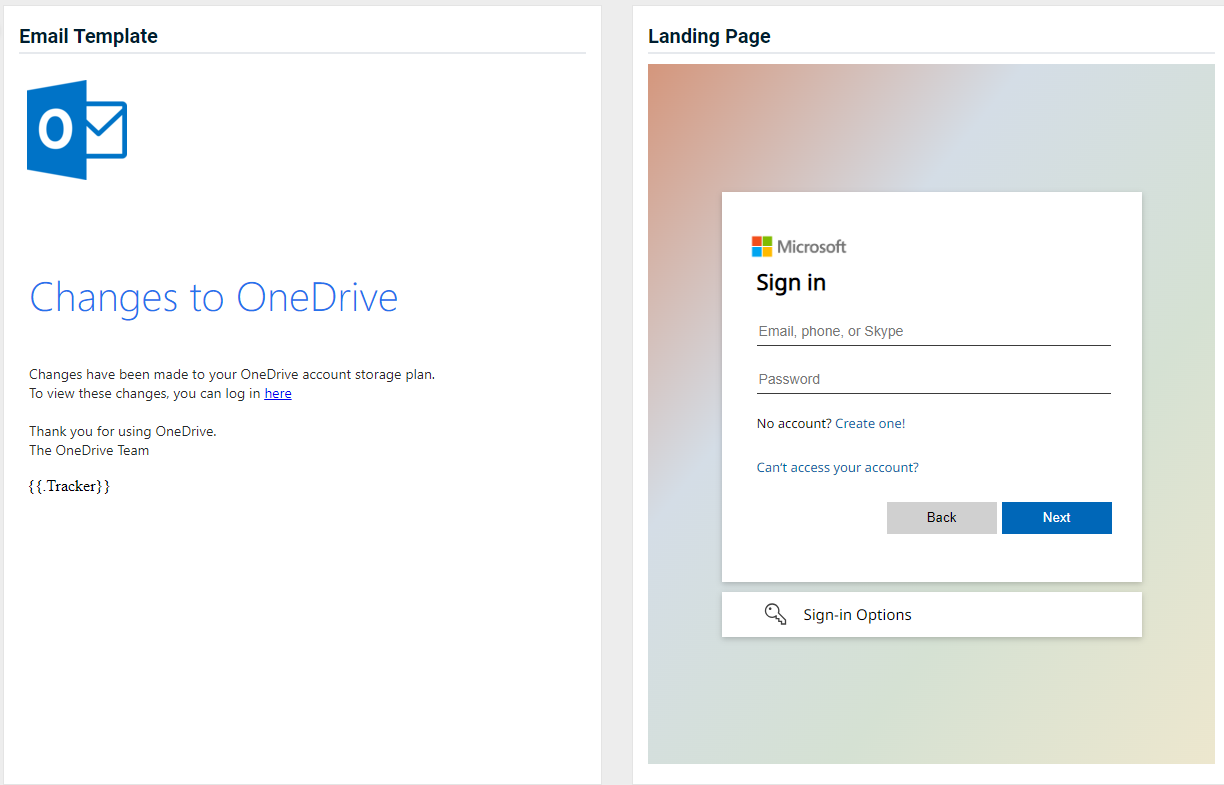
Some users have experienced the following phishing campaign issue: When clicking a link in a phishing campaign email, a warning message was displayed indicating that the destination site appears to be dangerous.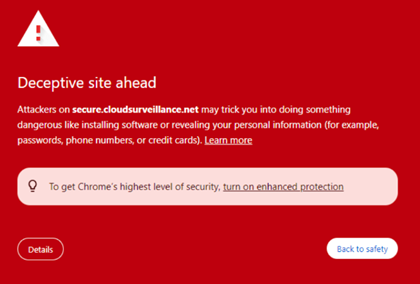
This problem has been addressed, and users will now be directed to the intended landing page without encountering the previous warning message.
Fixes
Issue 1
When recreating a phishing or training campaign, the groups attached to the original campaign were not automatically attached to the recreated campaign.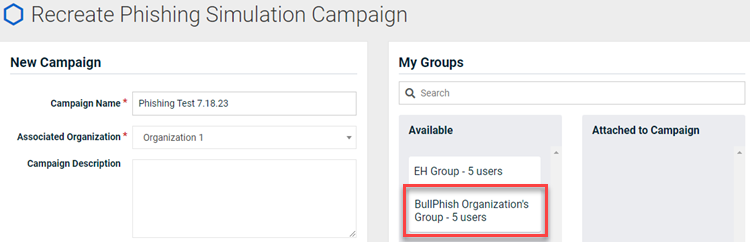
Fix
Now when recreating a campaign, the groups attached to the original campaign are automatically attached to the recreated campaign.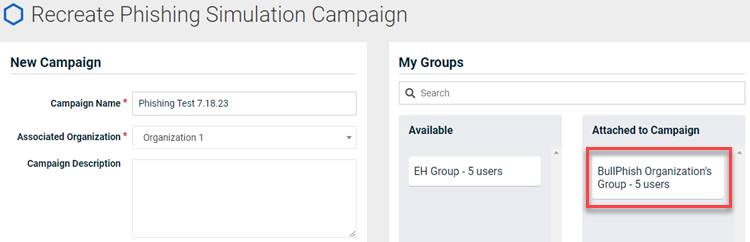
Issue 2
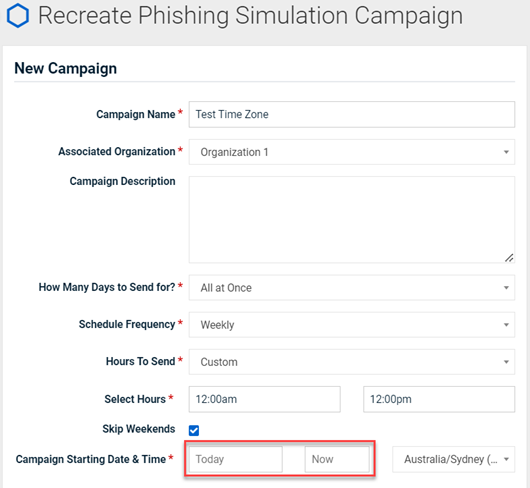
In the Re-create Campaigns modal, the Campaign Starting Date & Time field appears greyed out and therefore, disabled. However, the field is enabled and date and time values can be selected.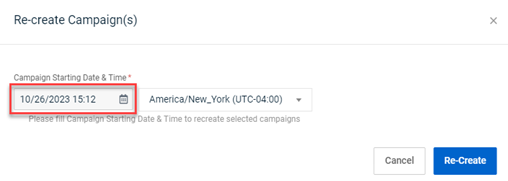
Note: The Re-create Campaigns modal is displayed by selecting a campaign’s check box on the Phishing Dashboard or the Training & Awareness Dashboard and clicking Recreate.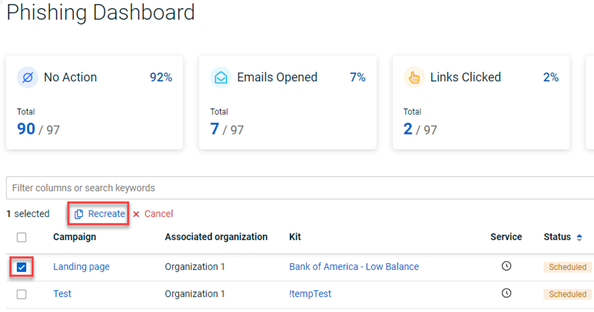
Fix
The Campaign Starting Date & Time field no longer appears greyed out.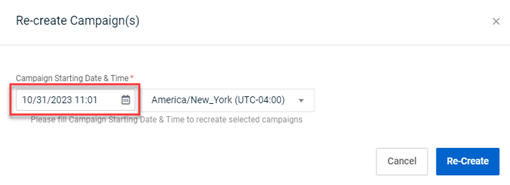
Issue 3
Phishing kit attachment icons were not displayed in phishing campaign emails that were opened in Gmail.
Fix
Phishing kit attachment icons are now displayed in phishing campaign emails that are opened in Gmail.
Content updates
Updated phishing kits
Updated phishing kits are now available. Each is listed below along with an image of its email template and landing page.
Enhancements
User reports now include campaign start date
Each campaign’s start date and time are now conveyed in the phishing and training user reports. The start date and time appear after the phishing kit name/training course and the campaign name.
Also, the campaign’s start date and time indicate the time zone selected when the campaign was created. The time zone is abbreviated (e.g., PST) if an abbreviation exists. If there is not an abbreviation, the full name of the time zone is displayed.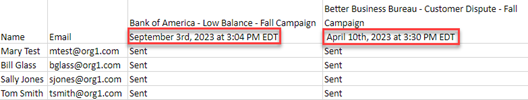
For more information, see the article Business reports and user reports
Mandatory email field in CSV file
The CSV format text in the Import Targets modal now includes an asterisk next to the Email field, indicating that the Email field is required in the CVS file for each target.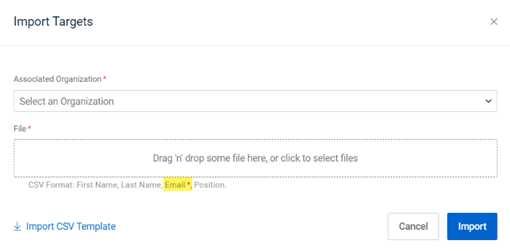
New Status field added to CSV target export file
A new Status column has been added to the CSV target export file that shows whether each target is Active or Inactive.
Example CSV file with Status column: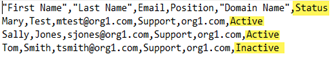
Select columns for CSV target export file
When exporting a list of targets to a CSV file, you now have the option of selecting the column data you would like included in the file. In the Export Targets modal, all of the columns are selected by default. If you clear a column’s check box, its data won’t be included in the CSV file.
Email addresses are included in the file by default.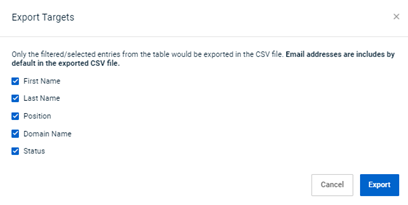
For more information, see the article How do I use the Export CSV button?
Content updates
Whitelisting guides updated
The following IP addresses highlighted in red have been removed from the whitelisting guides. We have moved to a new cluster in AWS and therefore, they are no longer necessary.
- 34.237.252.20 (SMTP Server IP- Where we send Phishing & Training Emails from)
- 168.245.13.192 (SendGrid IP - Needed for sending notification emails but only if you are using Dark Web ID as well as BullPhish ID)
- 54.211.230.155 (NAT gateway IP - IP address of background processes that initiate sending Phishing & Training Emails)
- 18.223.13.154 (Fallback - Secondary IP)
- 3.18.16.105 (Fallback - Secondary IP)
- 3.18.67.92 (Fallback - Secondary IP)
- 3.17.244.221 (Fallback - Secondary IP)
- 3.18.32.205 (Fallback - Secondary IP)
Welcome email revised
The email invitation sent to new users has been revised.
Subject Welcome to BullPhish ID – Account Setup Information
Hi _______,
_________ has invited you to join BullPhish ID.
BullPhish ID offers a user-friendly platform for security awareness training combined with realistic phishing simulations. These trainings are designed to minimize cyber vulnerabilities stemming from human mistakes. Additionally, using BullPhish ID can help organizations meet the criteria necessary for securing cyber insurance and adhering to compliance standards.
To begin, click here to accept the invitation.
Enhanced landing page for phishing kits
The text and formatting on the phishing landing page has been improved. All phishing kits created going forward will use this landing page.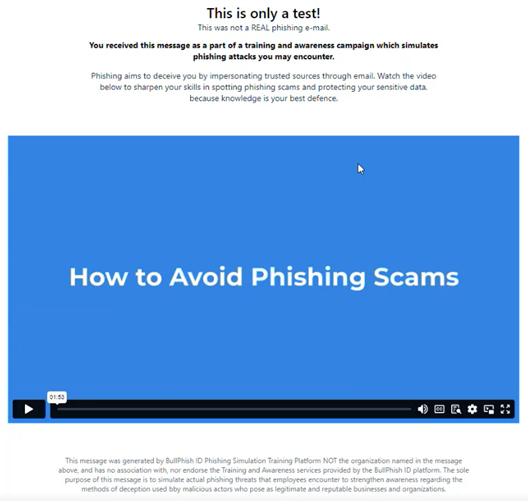
New/updated phishing kits
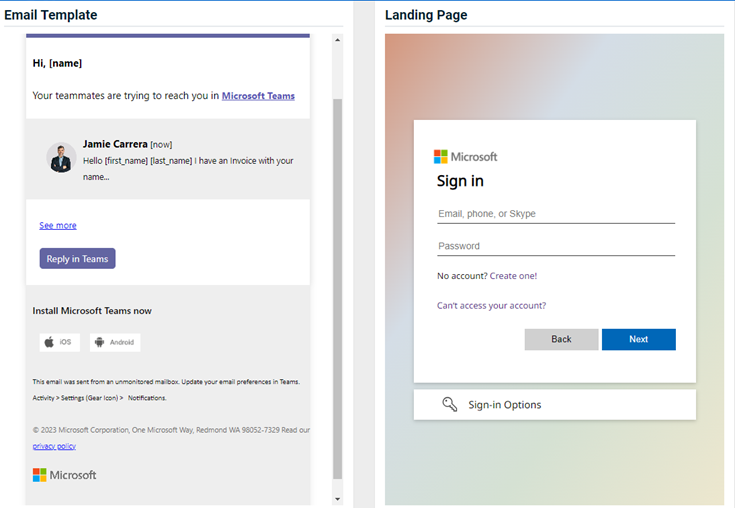
New and updated phishing kits are now available. Each is listed below along with an image of its email template and landing page.
- BambooHR – Important Documents V2
Note: The Sender in this version has been revised to BambooHR.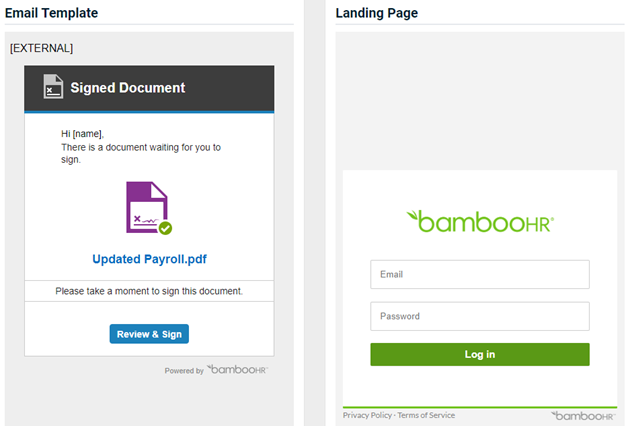
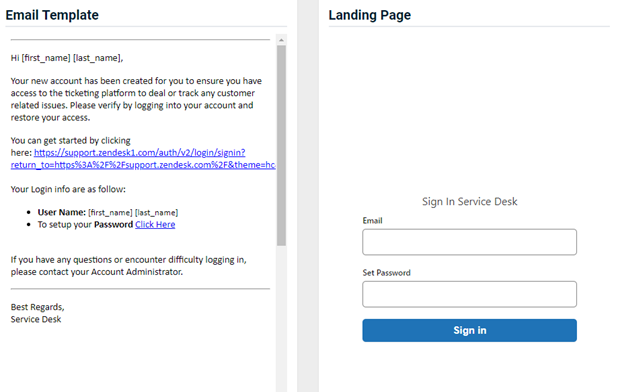
- Service Desk (new)
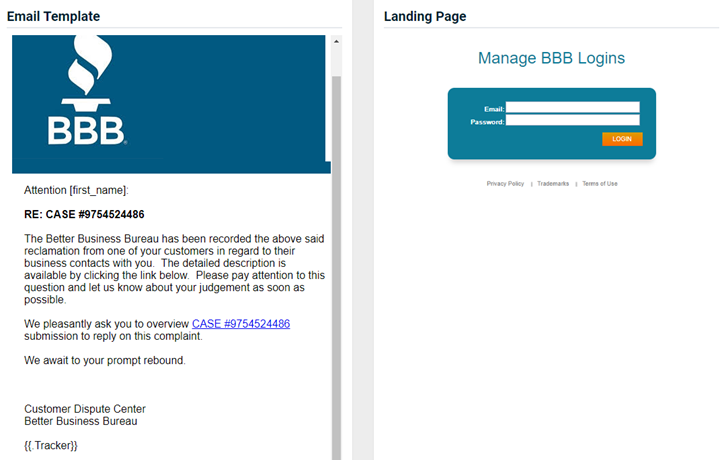
- Better Business Bureau - Customer Dispute (updated)
Fixes
Issue 1
When the Simple Button was used in a custom training email template, the button did not appear in Outlook emails when accessed in a browser. Only the button text appeared.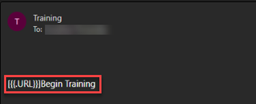
Fix
The issue has been resolved and buttons created using the Simple Button appear in Outlook emails when accessed in a browser.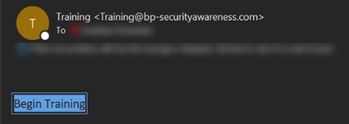
For more information, see the article Creating a custom email template.
Issue 2
When recreating a training or phishing campaign, the campaign start date and time was resetting to the current date and time. The start date and time of the original campaign should have been retained.
Fix
When recreating a campaign, if the start date and time of the original campaign are in the past, you are required to enter a campaign start date and time for the recreated campaign.
Original campaign: Start Date in the past
Recreated campaign: Enter Start Date & Time
Issue 3
The link to the to the Terms of Use page was broken in the Help section.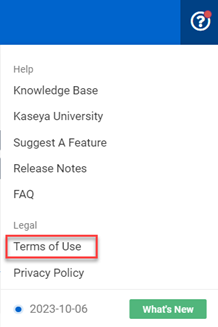
Fix
Link has been fixed and navigates to the Terms of Use page.
Automated reports notification email displayed incorrect sender address
After version 2.87 was released on September 28, 2023, an issue was encountered where some of the monthly and quarterly reports were generated using an incorrect sending profile. This issue has now been resolved. The accurate sender's email address will be utilized for future automated reports.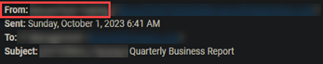
New Features
Automated User Reports
Now partner administrators, partner agents, and privileged users can automatically generate and deliver user reports for an SMB organization. Automated user reports are available for the modules (Training, Phishing) for which the organization has a BullPhish ID subscription.
Automated user report functionality is accessed on the Automate Report page. More information is provided in the next section, Automate Report page redesign.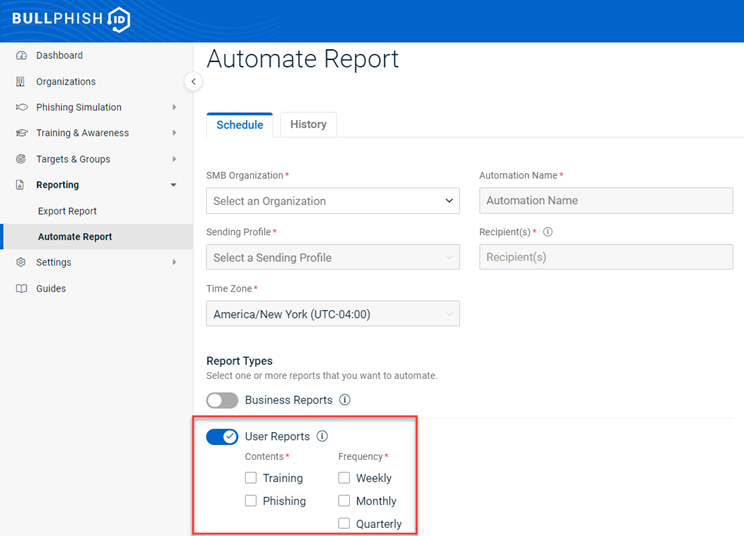
Automate Report page redesign
The Automate Report page has been redesigned. On the Schedule tab, fields have been rearranged and the Time Zone field has been added. Reports are generated between 00:00 AM and 11:59 PM in the selected Time Zone for the selected Frequency (explained below).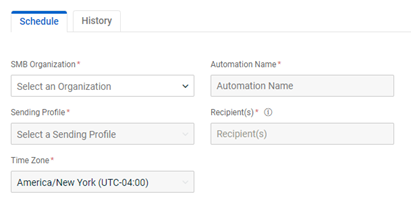
In the Report Types section, you select the reports you want to automate. You can choose to automate Business Reports, User Reports, or both.
A Frequency is required for each report type. The selected Frequency determines the time period for which data is collected and included in the report.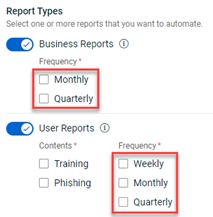
The Report Type column on the History tab now displays the type of report(s) created for each automated report. The Recipients column identifies the number of recipients to whom the report is sent. Hovering over the number displays each recipient’s email address.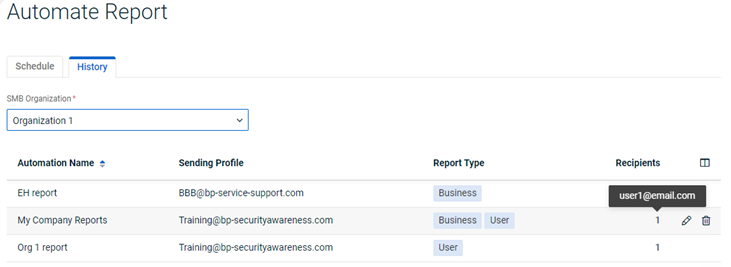
NOTE The user report notification email that is automatically sent to the specified recipients is similar to the business report email. The email reminds recipients to review the report and conveys the report download deadline date. Additionally, the email language is customized based on report frequency.
For more information about Automated User Reports and Automate Report page, see the article Automate business reports and user reports
Enhancements
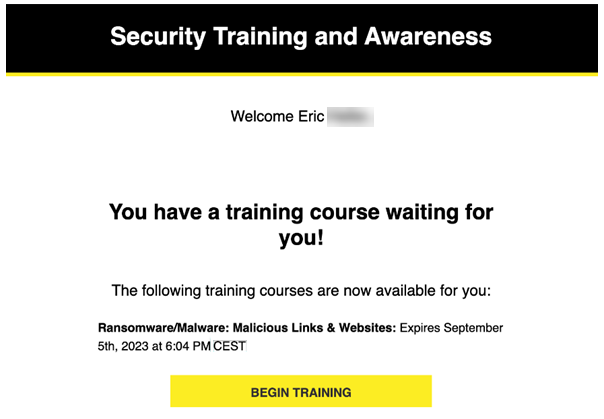
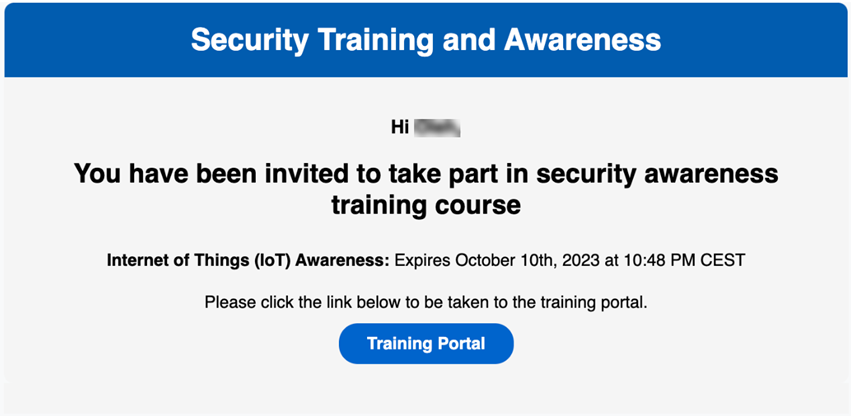
Updated training course email invitation
The format and content of the training course email invitation has been updated. The old version and new version are displayed below.
Old version
New version
Fixes
Issue 1
When using the Associated Organization filter, if the organization selected in the filter was subsequently deleted, a 403 Forbidden error occurred on the page for which the filter was being used. This issue occurred on any page (e.g. View All Training Campaigns page, Targets page, etc.) for which the Associated Organization filter was used.
In this example, the View All Campaigns page displays only training campaigns for Organization 1 and FilterOrg, as selected in the Associated Organization filter.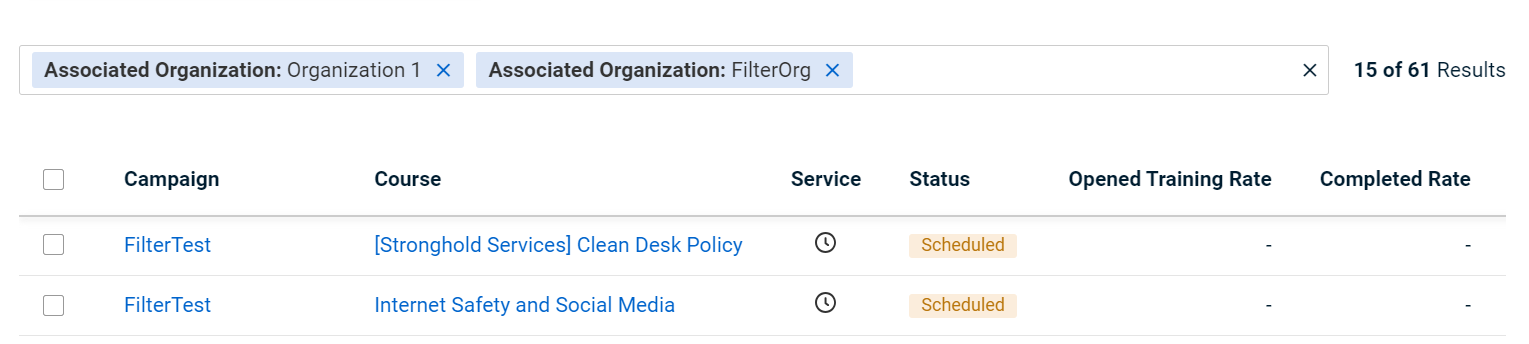
If one of the organizations were to be deleted, FilterOrg for example, when displaying the View All Campaigns page again (with the same organizations selected in Associated Organization filter), the 403 Forbidden error would occur.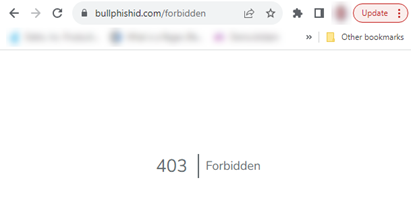
Fix
Now, if an organization selected in the Associated Organization filter is subsequently deleted, the 403 Forbidden error does not occur when displaying the applicable page.
In this example, the View All Campaigns page displays only training campaigns for TestOrg, as selected in the Associated Organization filter.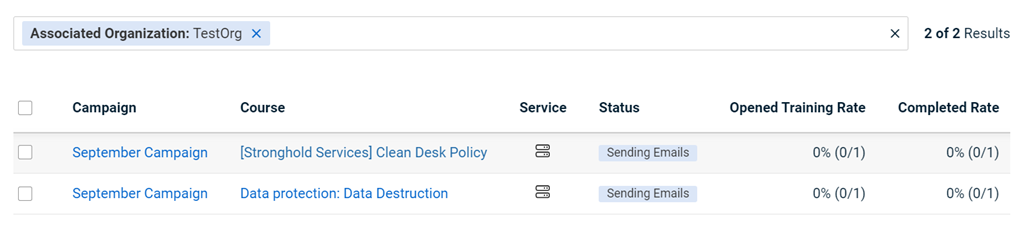
When the organization TestOrg is deleted, TestOrg results are removed from the View All Campaigns page.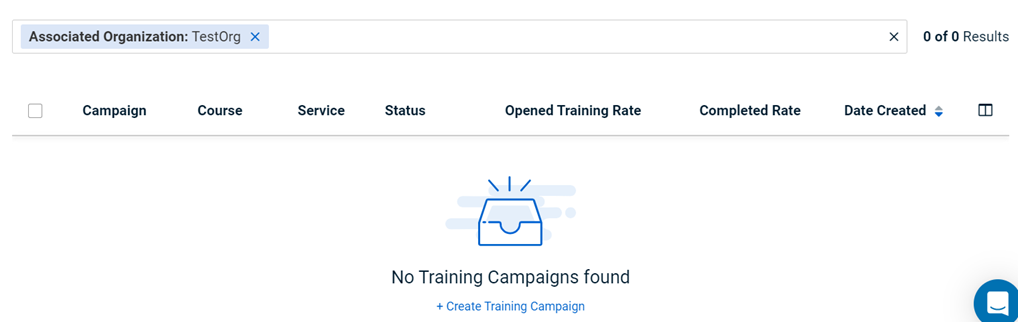
NOTE The deleted organization still appears in the Associated Organization filter. You can click the X to close the filter. Or, refresh the page in approximately 10 minutes and the filter will be removed.
Issue 2
When resending a training campaign email, if the campaign included a Sending Profile that had been previously deleted and replaced, the email would fail to be sent.
Fix
Now, when resending a training campaign email that includes a deleted and replaced Sending Profile, the email is sent successfully. The campaign’s Details page shows the name of the profile that was deleted, the date and time it was replaced, and the name of the current profile.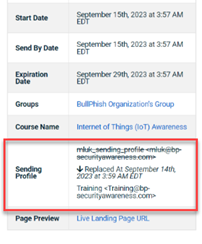
The User Training Log indicates the date and time for which the training email was resent.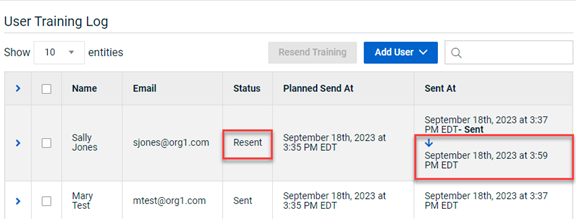
New/updated phishing kits
New and updated phishing kits are now available. Each is listed below along with an image of its email template and landing page.
Duplication of campaigns due to recalculation of statistics
Some organizations have randomly experienced an issue where statistics were recalculated for the same phishing or training campaigns. This resulted in campaigns being duplicated on the applicable "View All" page or videos appearing twice in the training portal.
When you created a campaign, it may have been displayed twice. The second campaign was a mirror image of the original campaign, except the statistics of each campaign differed.
In this example, the highlighted training campaign was displayed as a duplicate on the View All Training Campaigns page. Deleting the duplicate would also delete the original campaign.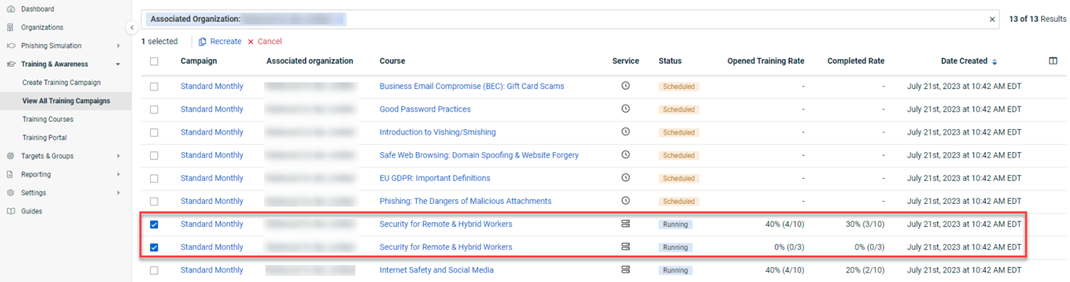
In this training portal example for a particular target, each course appears as an open course and as a completed course.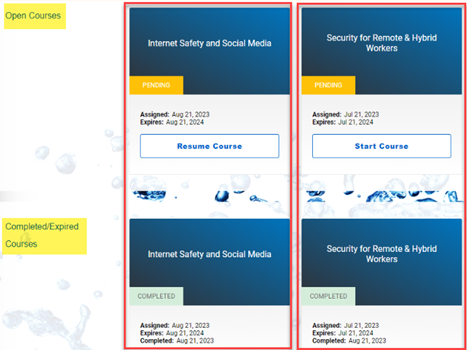
This issue has been resolved. All duplicate campaigns and videos have been deleted. The valid videos will appear with the correct Status (i.e. Open, Completed/Expired) in the training portal.
Fixes
Issue 1
When attempting to perform an IT Glue contact sync in BullPhish ID, if another IT Glue contact sync was already in progress, an error message was displayed indicating a sync could not be performed.
Fix
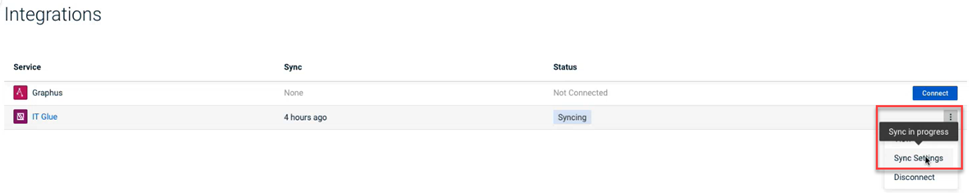
To address the issue, the following enhancements have been made to convey when a sync is currently in progress:
- On the Integrations page, in the three-dot menu, the Sync Settings option is disabled. Hovering over the Sync Settings option displays the Sync in progress tooltip.
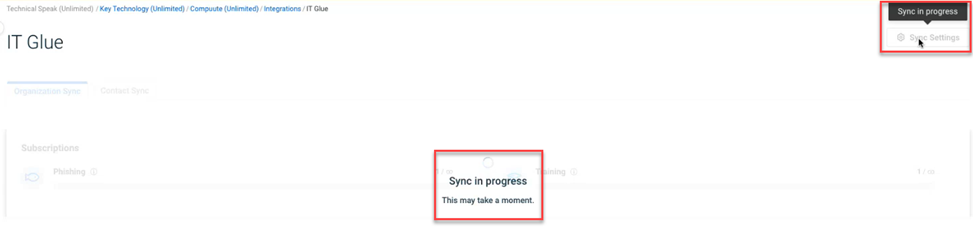
- On the Integrations > IT Glue page, the Sync Settings button is disabled. Hovering over the Sync Settings button displays the Sync in progress tooltip.
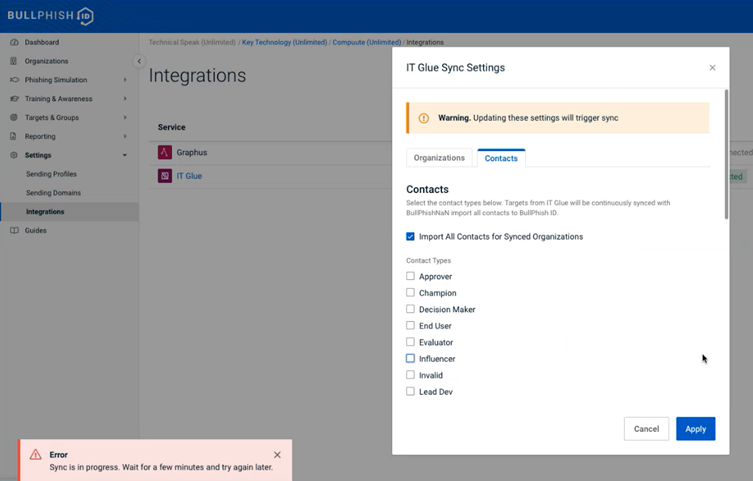
- In the IT Glue Sync Settings modal, when the Apply button is clicked and a sync is already in progress, an error message is displayed indicating that a sync is in progress. This situation may occur if more than one user attempts to perform a sync at approximately the same time. Or, the error may occur if the same user attempts to perform more than one sync (e.g., on a second browser tab) at approximately the same time.
Issue 2
For phishing campaign emails that included attachments, the attachment icons appeared oversized in Outlook for Windows-based laptop users.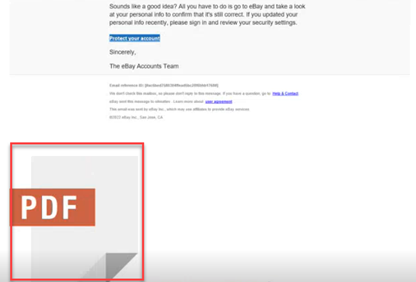
Fix
This issue has been resolved. Now, attachment icons appear at the appropriate size.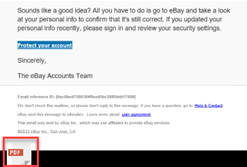
MME organization users were unable to create child SMB organizations
After version 2.85 was released on August 28, 2023, an issue was encountered where MME organization users were unable to create child SMB organizations. This issue has been resolved.
New Features
Automatic User Creation
After you have enabled KaseyaOne Unified Login and Automatic User Creation for your organization, your users in KaseyaOne who are granted access to the BullPhish ID module will automatically have a user created in BullPhish ID. The Automatic User Creation feature is available on the KaseyaOne tab on the organization's Settings page.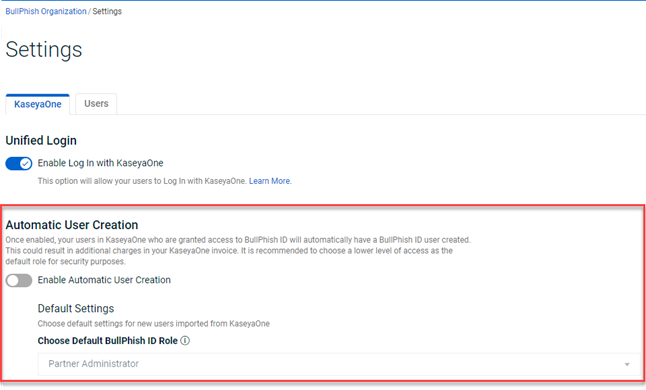
With the Automatic User Creation feature, you can select a default access role that will automatically be assigned to newly created users. For user role information, refer to the BullPhish ID user roles article.
IMPORTANT The Enable Log In with KaseyaOne toggle must be activated before the Automatic User Creation feature can be enabled.
For more information about the Automatic User Creation feature, see the article Enabling automatic user creation.
Fixes
Issue 1
Training campaign invitations for campaigns created for the Pacific time zone were displaying the Eastern time zone instead for the course expiration date and time.
Fix
This issue has been resolved. Now, the course expiration date and time in the invitation:
- reflects the timezone selected at the time of campaign creation.
- displays the abbreviation of the time zone, if one exists (e.g., PST).
Issue 2
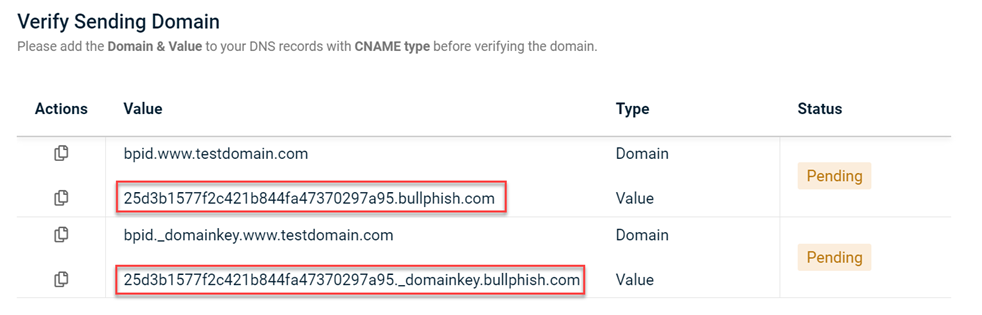
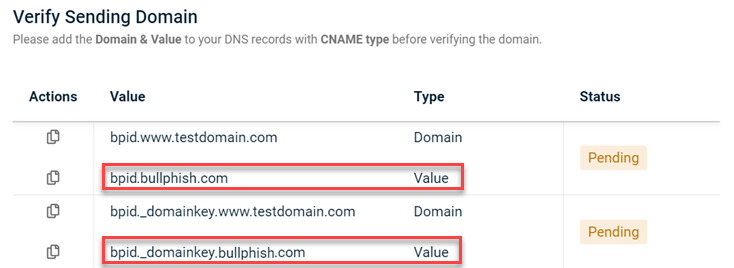
When using a custom domain in a phishing or training campaign, the campaign emails were failing the email spoofing test. The DNS records used to validate the custom domain were missing.
Fix
The issue has been fixed so DNS records are now available when validating custom domains. Also, when you create a custom domain, bpid is assigned as the Value instead of the long character string. The fix applies to all previously created campaigns in the Scheduled or Processing Status and to all newly created campaigns going forward.
Old value
New value
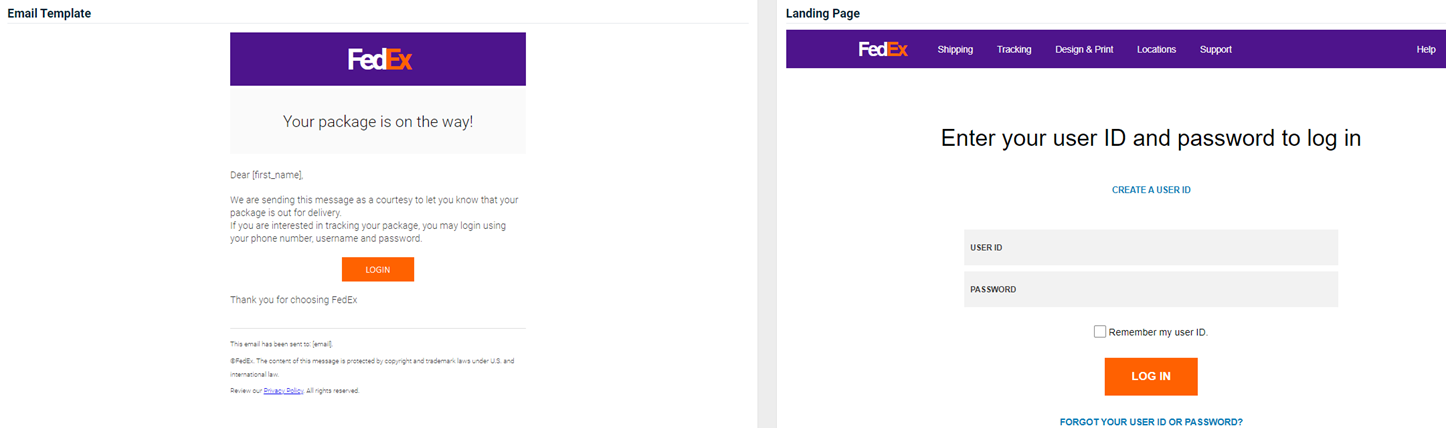
New phishing kit
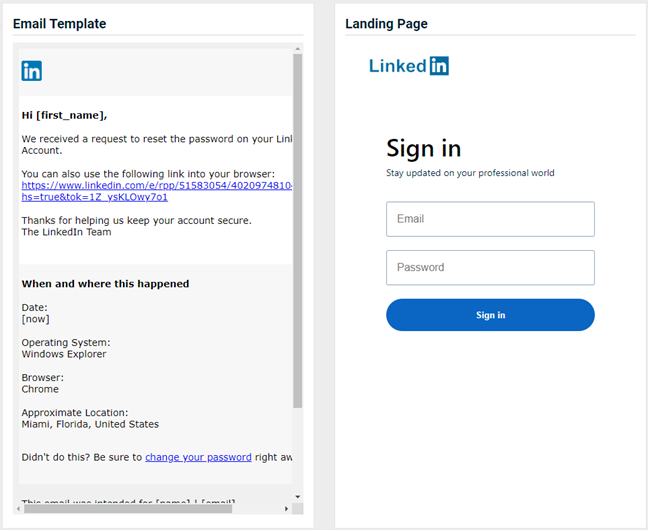
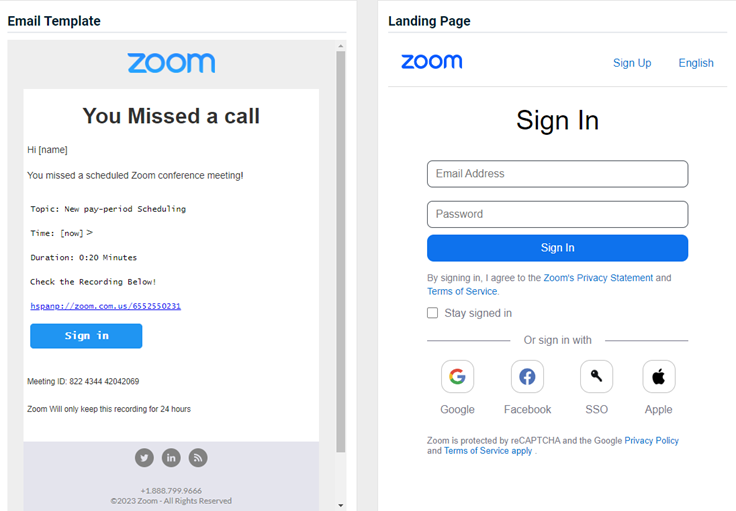
The new Netflix - Free Trial v2 phishing kit is now available. The email template and landing page are displayed below.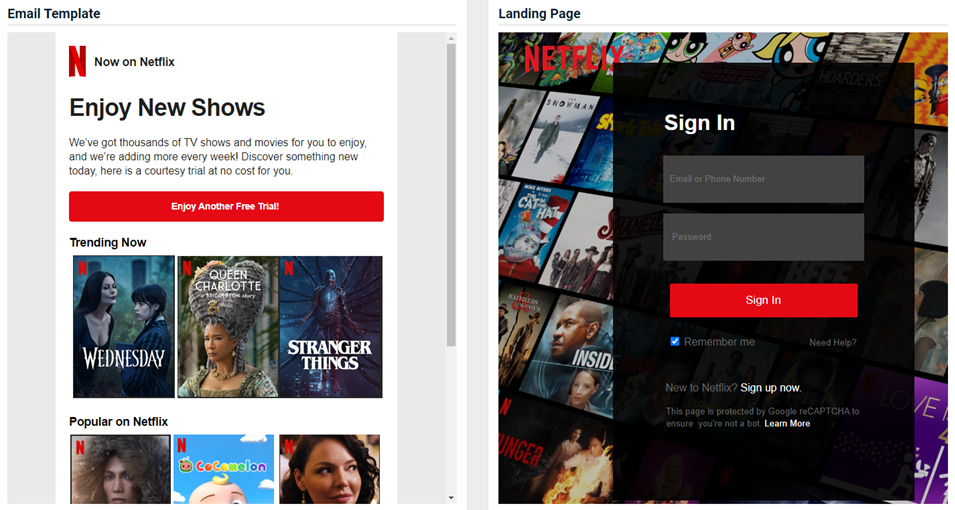
New phishing kit landing page
A new landing page is now available in English for use when creating a custom phishing kit. The landing page is called OopsLandingPage. When you use this landing page in your phishing kit, users will be taken to this OopsLandingPage after clicking on the email. The step to take users to the credentials submission page will be skipped in the phishing kits using this landing page. Therefore, the Data Submitted status won't be tracked, but No Action, Emails Opened, and Links Clicked will be tracked.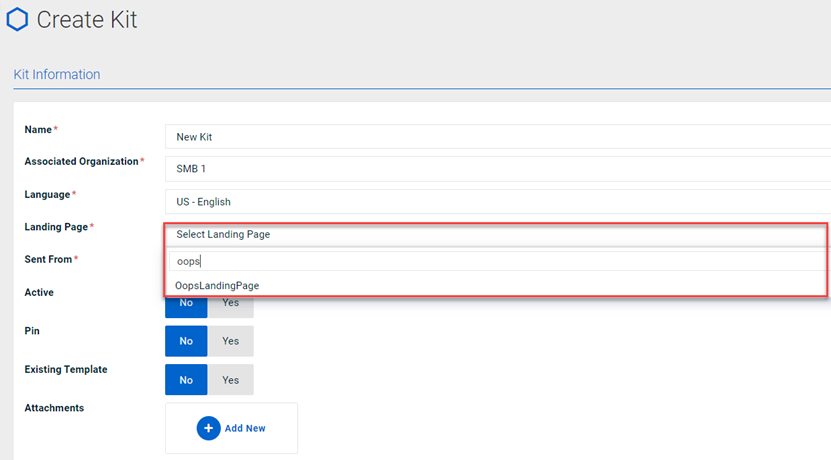
The landing page includes guidelines for identifying phishing threats and a link to the course How to Avoid Phishing Scams.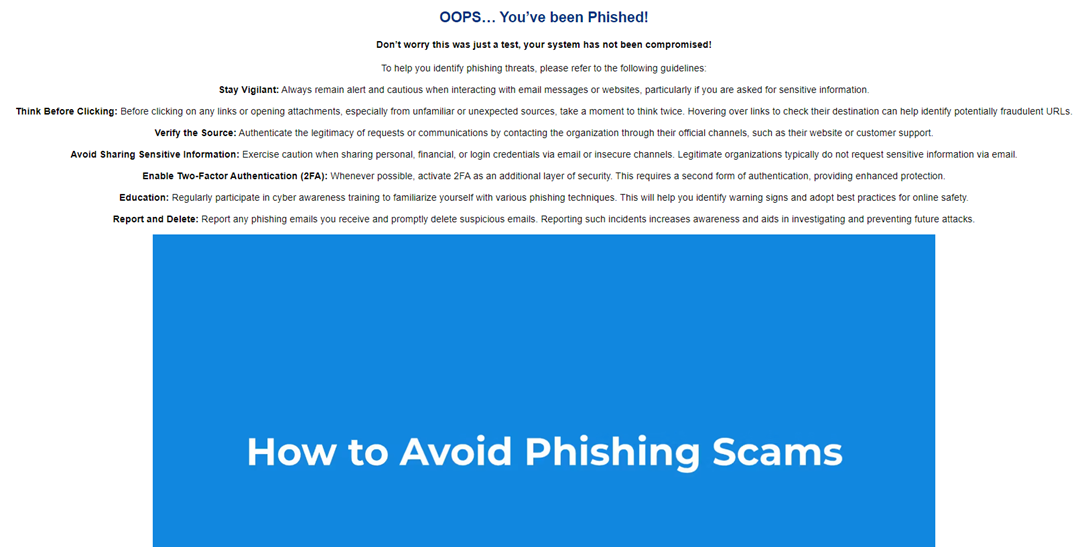
New training courses
New training courses are now available in the Training portal. For the courses available in different languages, see the table that follows the course descriptions.
- Introduction to Protecting Credentials: In this course, learn simple practices you should follow that make it nearly impossible for cybercriminals to compromise your credentials.
- Common Attack Types: Phishing is the most common attack used by cybercriminals to gain wrongful access to computer systems. In this course, you’ll examine the common phishing attack types.
Course names
| English | Spanish | French | Portuguese | German | Dutch |
|---|---|---|---|---|---|
| Introduction to Protecting Credentials | Introducción a la Protección de Credenciales VO | Introduction à la Protection des Identifiants VO | Introdução à Proteção de Credenciais VO | Einführung in den Schutz von Anmeldedaten | Inleiding tot het Beschermen van Toegangsgegevens |
| Common Attack Types | Tipos De Ataque Comunes VO | Types D’attaques Courantes VO | Tipos De Ataque Comuns VO | Häufige Angriffsarten | Veel Voorkomende Aanvallen |
Documentation updates
Directory sync guides updated
In the Add Directory Sync modal, the Where do I find this? link opens the updated integration guide for the Directory Type selected. Each guide includes the steps for performing the integration. For example, selecting Azure as the Directory Type and clicking Where do I find this? opens the guide Integrating with Microsoft Entra ID.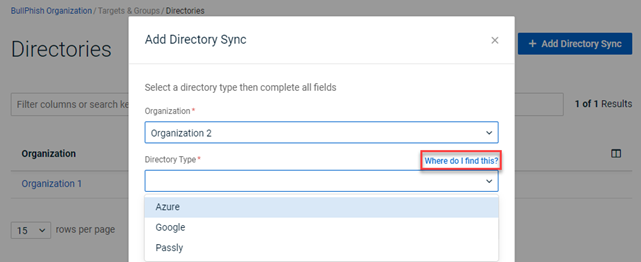
New article: BullPhish ID user roles
BullPhish ID user roles is a new article that identifies the BullPhish ID user roles that can be assigned to employees of MSP and SMB organizations. In addition, the user permissions granted for each role are described.
Training courses update
New training courses are now available in the Training portal. For the courses available in different languages, see the table that follows the course descriptions.
- The Dangers of Password Sharing: Learn why password sharing is a bad idea and a fast path to a data breach or cyberattack for your organization.
- The Basics of Multi-Factor Authentication: In this course, Multi-Factor Authentication is examined and the benefits of implementing it are described.
- Introduction to Phishing (updated version): In this course, you’ll examine the components of phishing and its various attack types and learn the steps to take if you suspect you have received a phishing email.

Course names
| English | Spanish | French | Portuguese | German | Dutch |
|---|---|---|---|---|---|
| The Dangers of Password Sharing (English version previously published) | Los peligros de divulgar contraseñas VO | Les dangers liés au partage des mots de passe VO |
O risco de compartilhar senhas VO | Gefahren beim Teilen von Kennwörtern | Gevaren van delen
van wachtwoorden |
| The Basics of Multi-Factor Authentication (English version previously published) |
Aspectos Básicos de la Autenticación Multifactor VO | Les Bases de L’authentification Multifactorielle VO |
Os Fundamentos da Autenticação Multifactor VO |
Die Grundlagen der Multi-Faktor-Authentifizierung | De Belangrijkste Principes van Multifactorauthenticatie |
| Introduction to Phishing | Introducción al Phishing VO | Introduction а́ L’hameçonnage VO | Introdução ao Phishing VO | Einführung in Phishing | Inleiding tot Phishing |
Enhancements
Updating the Client Secret for Microsoft Azure integrations
For Microsoft Azure integrations, the Client Secret field in the BullPhish ID Directory Settings modal is now editable.
When you create a new Client Secret in Microsoft Azure, you can copy and paste it into the Client Secret field of your existing Azure directory sync.
After updating the Client Secret in the Directory Settings, there is no need to worry about existing synced groups getting delinked. The system has been enhanced to ensure that these groups will continue to sync effortlessly with the directory.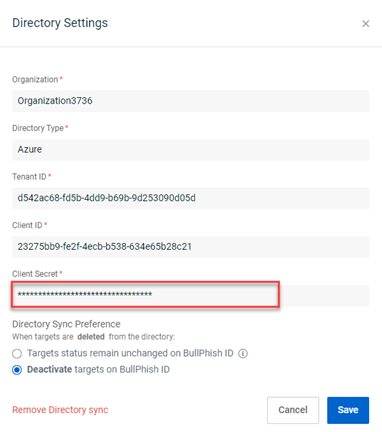
Expanded selection limit for IT Glue Sync Settings
Previously, users were restricted to selecting a maximum of 100 IT Glue statuses, organization types, and contact types for synchronization. With this improvement, we have increased the selection limit to 200 for each type. This enhancement provides users with greater flexibility and the ability to synchronize a broader range of data, streamlining the integration process between BullPhish ID and IT Glue.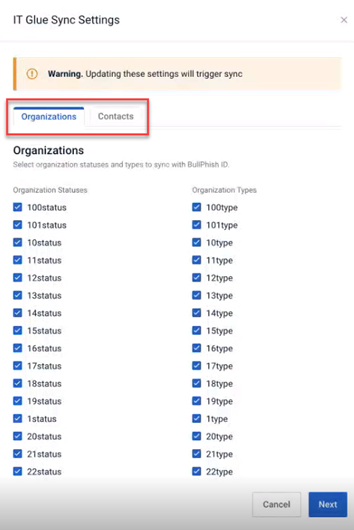
IT Glue integration throttling behavior
The IT Glue API limits the total number of API requests it receives from each client within a specific timeframe. These limits exist to prevent the API and the client account from being overwhelmed by too many requests.
When an API limit is reached, the API sends an error code to the client indicating the request can't be handled. Instead of resending the request immediately, which could further compound the issue, there is now a delay of a few seconds before BullPhish ID resends the request. This will help alleviate the throttling issue, resulting in better IT Glue integration performance.
Improved tracking for attachments in phishing emails
In this release, we have implemented an improvement to the tracking of attachment clicks in phishing emails. When targets interact with the attachment links included in a phishing campaign email, these clicks are now accurately recorded under the Clicked Link statistic for the campaign.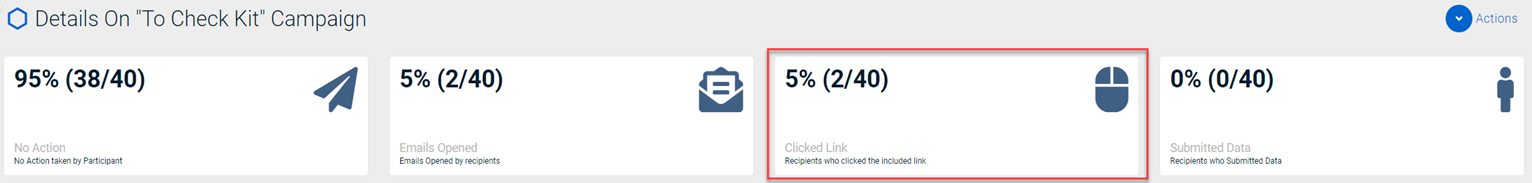
Also, the Status column of the target's record in the Email Log indicates Clicked Link. The Event record displays more information about the Attachment Clicked event.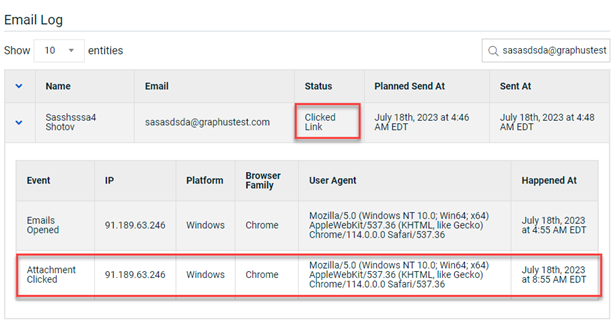
New Training course
A new training course The Basics of Multi-factor Authentication in English is now available in the Training portal. Multi-Factor Authentication is examined and the benefits of implementing it are described. This course is an addition to our credential security series.
Enhancements
IT Glue contact sync
Previously, when importing IT Glue contacts, if a contact did not have a primary email address, the contact would not be imported.
Now, if a contact does not have a primary email address, BullPhish ID will use the contact's secondary email address, if one exists. If a contact has multiple email addresses, the first email listed will be used.
NOTE BullPhish ID always uses the contact's primary email address, if one exists.
For more information, see the article Integrating with IT Glue.
Fixes
Issue
The Start Date and email Send By Date were calculated incorrectly for some phishing campaigns created with the following criteria:
- Time zone selected was ahead of the Eastern time zone
- Campaign start date was on a Monday
- Skip Weekends option was selected
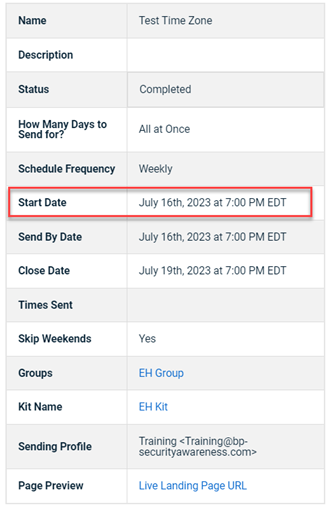
In this example, the phishing Campaign Starting Date & Time is July 17, 2023 at 9:00 AM in the Australia/Sydney time zone.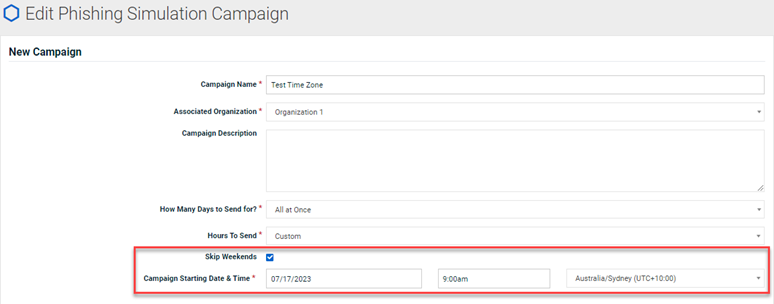
The campaign's Details page indicates the Start Date and email Send By Date is July 16th, 2023 at 7:00 PM Eastern. July 16th is a Sunday. Because the Skip Weekends option is selected, BullPhish ID will not send email notifications until the next day. However, the Australia/Sydney time zone is one day ahead, meaning the campaign emails won't be sent until Tuesday July 18th. BullPhish ID was not basing the Start Date and email Send By Date on the time zone selected.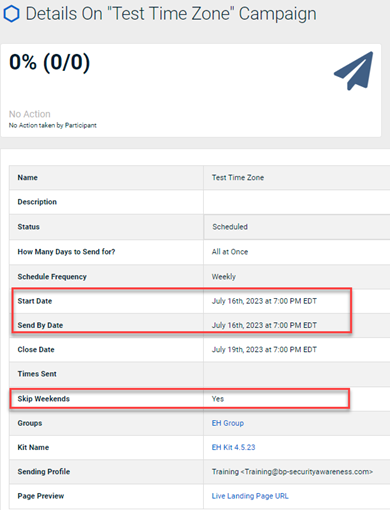
Fix
This issue has been resolved. BullPhish ID is now basing the Start Date and email Send By Date on the time zone selected. In the example, the campaign would start on Monday July 17, 2023 at 9:00 AM in the Australia/Sydney time zone.
NOTE The campaign's Details page continues to display the Start Date and email Send By Date in the Eastern time zone.
Training campaigns with more than 200 targets
An issue was encountered where training campaigns that included more than 200 targets were cancelled. This affected training campaigns that started processing between July 4, 2023 at 8:56 AM and July 10, 2023 at 1:00 PM.
The issue has been resolved and all campaigns that were cancelled due to this issue have been recreated.
Phishing kits with attachments
After version 2.81 was released on July 4, 2023, an issue was encountered where emails were not being sent for phishing campaigns whose kits included attachments. This affected phishing campaigns scheduled between July 4, 2023 at 12:00 AM and July 5, 2023 at 2:16:04 AM.
This issue has now been resolved. The phishing emails for the affected campaigns were sent immediately after the issue was resolved.
New Features
Add Users to Ongoing Training Campaigns
The new Continuous Target Sync feature in BullPhish ID makes it much easier to add new targets to ongoing training campaigns.
When Continuous Target Sync is enabled, after a target is added to a group that is part of an ongoing training campaign, the target is automatically added to the campaign.
The Continuous Target Sync toggle is available on the Training & Awareness Dashboard (select Training & Awareness > View All Training Campaigns) and applies only to training campaigns.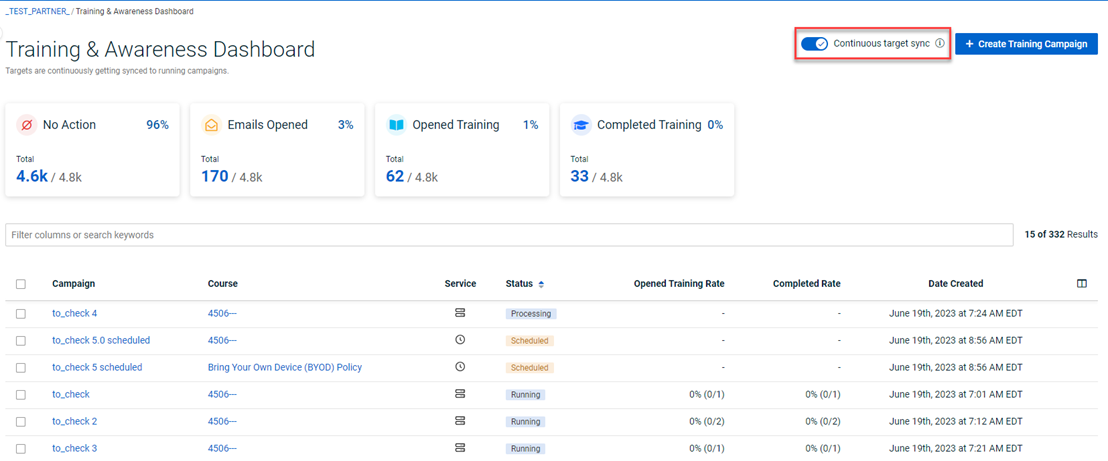
When Continuous Target Sync is enabled, a one-time sync is initiated for all ongoing training campaigns associated with your SMB organizations. Note that it may take several hours for the campaigns to be updated with the latest target list.
For more details, refer to the article Adding new targets to ongoing training campaigns. Along with more detailed information about the Continuous Target Sync feature, the article also describes specific scenarios that apply.
Enhancements
Resending an email invitation for one training course from a multi-course campaign
You now have the ability to resend an email invitation for one training course from a campaign that includes multiple courses. The email includes only the information for the course selected and is sent only to the target selected from the group.
The Resend Training button is available when a target is selected in the User Training Log table on the selected campaign's Details page. Multiple targets can be selected and an email invite would be sent to each target.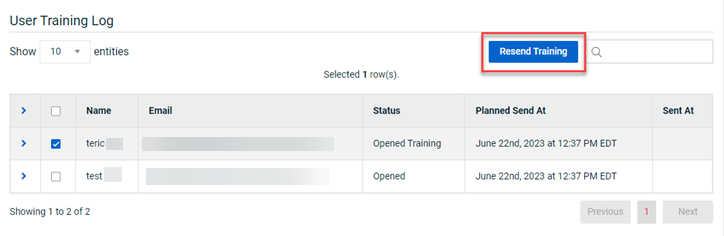
For more information, see the article Resending an email invitation for one training course from a multi-course campaign from a campaign that includes multiple courses.
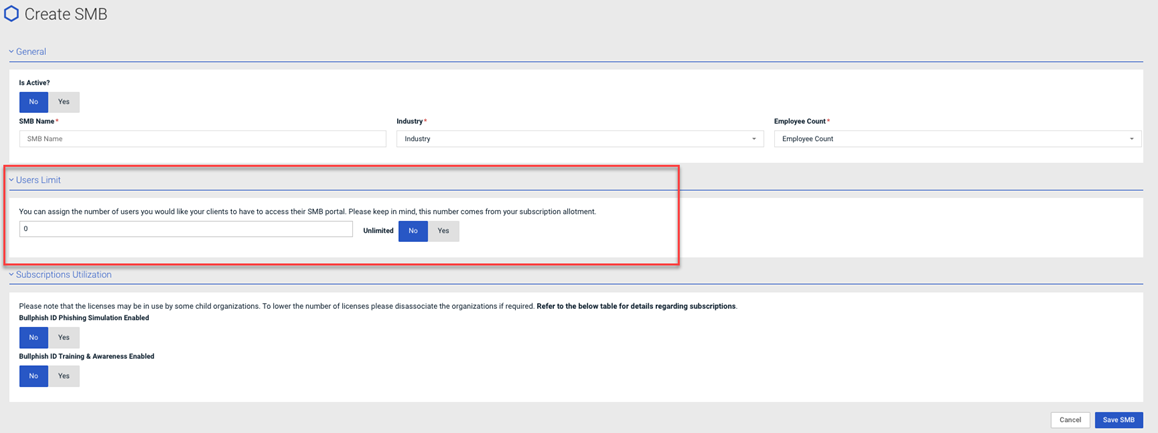
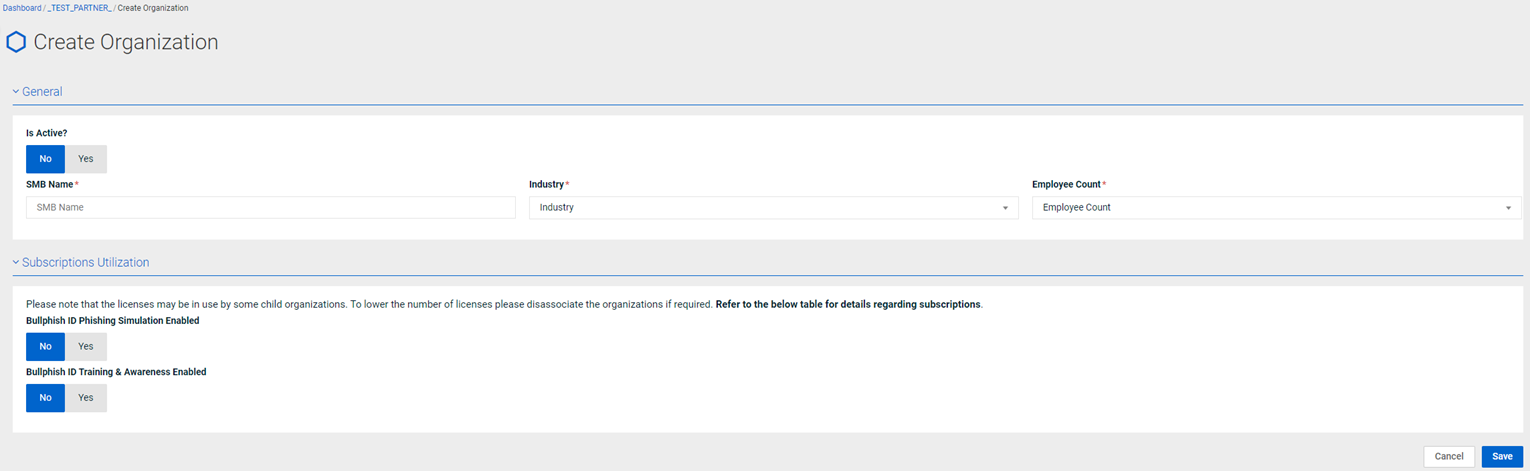
Creating a new SMB organization
When creating a new SMB organization, the requirement to specify the SMB user limit has been eliminated.
Old page
New page
UI label updates
You will notice some terminology updates have been made throughout the BullPhish ID user interface. These changes were made to align BullPhish ID with the common terminology being used across all Kaseya products.
- On the MSP, MME Dashboard & Organizations pages, the Add SMB button is now the + Add SMB Organization button.

- For MSP, MME accounts, My Profile page is now My Settings page. (Select Username > My Settings).
- On the Username dropdown, Organization Settings is now Settings.
- The term 2FA has been updated to Two-Factor Authentication across the platform.
- MME is now MME Organization (e.g., Create MME is now Create MME Organization).
- On the MME Organization tab, Local Organization Settings is now MME Organization Settings.
- Create SMB page is now the Create Organization page.
- On the SMB Dashboard, SMB Settings is now Add SMB User.

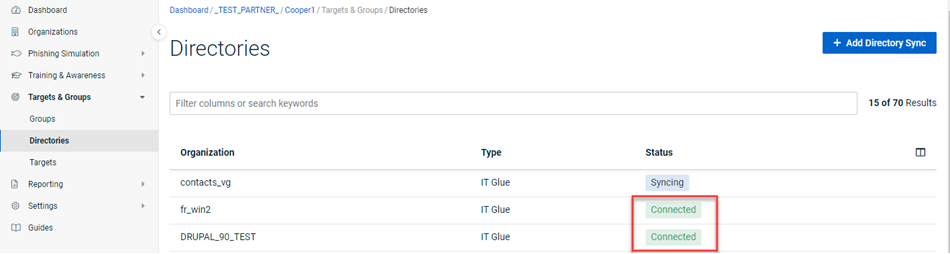
- On the Directories page, the Status field value Active is now Connected.
- On the Help menu, Product Documentation is now Knowledge Base.
Phishing kits update
Four new phishing kits are available. Each is listed below along with an image of its email template and landing page.
This release includes system enhancements, bug fixes, and training course updates.
Enhancements
IT Glue integration
System improvements have been made to enhance performance when integrating BullPhish ID with IT Glue. These improvements aim to reduce the number of API calls and enhance responsiveness by utilizing local caching.
Updates made directly in IT Glue involving organizations, organization types, organization statuses, and contact types will appear in BullPhish ID within one minute.
Therefore, the data presented when using the Add from IT Glue, IT Glue Organization, and Sync Settings functionality in BullPhish ID is automatically synced within one minute of IT Glue updates.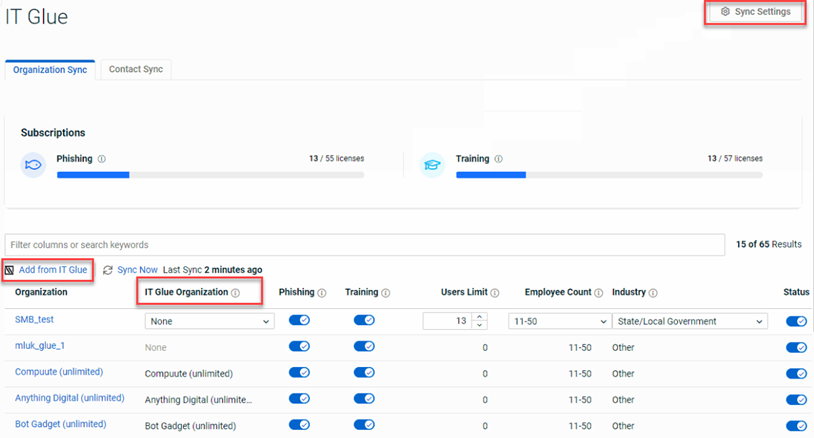
Updated Microsoft Office 365 Automatic Safelisting Guide
The Microsoft Office 365: Automatically adding safe senders to Microsoft Outlook has been updated to improve the process of whitelisting the sending domains you want to use in your campaigns.
The instructions provide additional guidance for registering your application in Azure and for editing and running the scripts that whitelist the sending domains.
Improved activity logs
The visibility of training course activities has been improved in the backend activity logs.
Fixes
Issue
When deleting users from their active directory, some organizations encountered a synchronization problem between active directory and BullPhish ID. Targets were not being removed from the BullPhish ID groups synced with the active directory groups from which the target was deleted.
Fix
This issue has now been resolved.
Training courses update
New training courses are now available in the Training portal. For the courses available in different languages, see the table that follows the course descriptions.
- Social Media Safety: Learn the risks of using social media and how to avoid a social media based cyberattack.
- How to Protect Credentials Using Multifactor Authentication: Protecting your credentials is essential in preventing cyberattacks. Multifactor authentication is an easy and effective tool for protecting your credentials.
- The Dangers of Password Sharing: Learn why you should never share your passwords with anyone.
Course names
| English | Spanish | French | Portuguese | German | Dutch |
|---|---|---|---|---|---|
| Social Media Safety | Seguridad en las redes sociales VO | Sécurité des médias sociaux VO | Segurança nas redes sociais VO | Social-Media-Sicherheit | Veiligheid van sociale media |
| How to Protect Credentials Using Multifactor Authentication | Cómo proteger las credenciales usando autenticación multifactor VO | Comment protéger les renseignements d'identification grâce à l'authentification multifactorielle - VO | Como proteger credenciais usando a autenticação multifator VO | Schutz von Anmeldedaten mit Multi-Faktor-Authentifizierung | Inloggegevens beschermen met multifactorauthenticatie |
Syncing IT Glue organization contacts
A synchronization problem between IT Glue contacts and BullPhish ID was encountered when attempting to sync 100 or more contacts. The process would become stuck and fail to complete for impacted organizations. However, this issue has now been resolved.
Now, IT Glue organizations can successfully sync 100 or more contacts with BullPhish ID, as displayed on the Contact Sync tab below.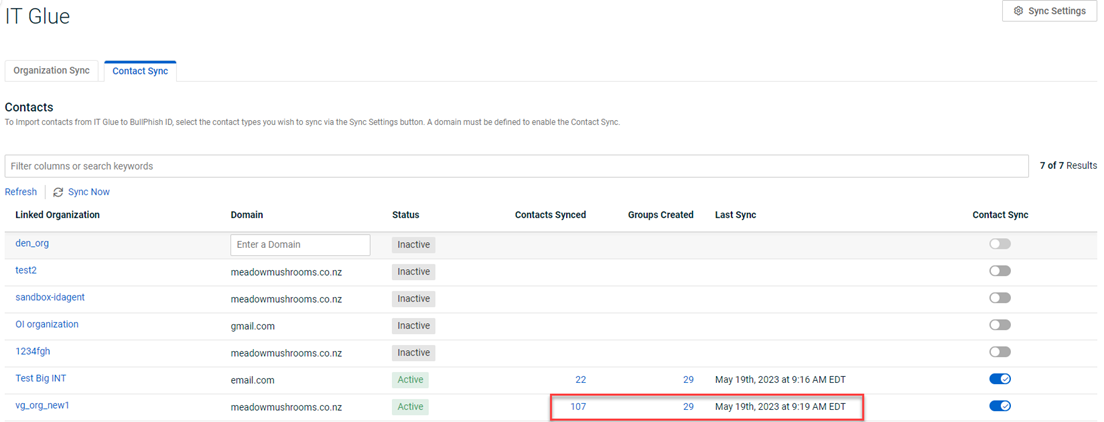
Enhancements
Directory Sync Preference options
Directory Sync Preference options are now available when creating a new directory sync or editing an existing directory sync.
The options determine how targets are handled in BullPhish ID after they have been deleted from an organization's active directory.
The Directory Sync Preference options are:
- Targets status remains unchanged on BullPhish ID: This is the default selection. When targets are deleted from active directory groups:
- The targets are removed from the BullPhish ID groups that are synced with the active directory groups. Targets in groups created manually in BullPhish ID are not affected.
- The Status of each target in BullPhish ID remains the same. In other words, the Active or Inactive Status of each target remains unchanged on the Targets page.
- Deactivate targets on BullPhish ID: When targets are deleted from active directory groups:
- The targets are removed from the BullPhish ID groups that are synced with the active directory groups. Targets in groups created manually in BullPhish ID are not affected.
- Each target is deactivated in BullPhish ID and the Status for each is changed to Inactive.
Here is the Directory Settings modal that is displayed when editing an existing directory sync. The Directory Sync Preference options are at the bottom.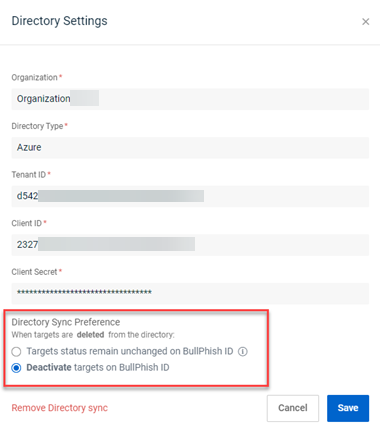
The selected option goes into effect when the next directory sync occurs.
For more information about Directory Sync Preference options, see the article Adding a directory sync.
Viewing MME subscription information
Partners now have the ability to view the subscription information of their MMEs in Dark Web ID. See the article How do I view MME subscription information in Dark Web ID?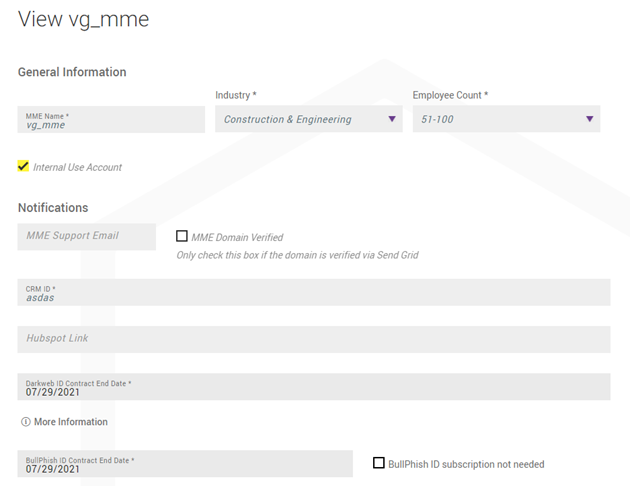
Enhancements
Improved activity logs
Activity logs for targets functionality has been improved. More information regarding adding, deleting, activating, and deactivating targets is now being recorded on the backend.
Training courses update
A new version of the course Phishing: Brand Fraud and Spoofing is now available. In this course, you will learn about brand fraud, spoofing, and how to avoid becoming a victim of this phishing type. The course is available in the following languages:
- English: Phishing - Brand Fraud and Spoofing
- Portuguese: Spoofing e fraude de marcas VO
- Canadian French: Fraude aux marques et usurpation d’identité VO
- Latin American Spanish: Fraude de marca y spoofing VO
Subtitles are available in the following languages:
- German: Markenmissbrauch und Spoofing
- Dutch: Merkfraude en spoofing
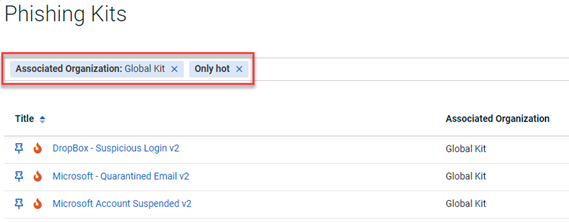
To quickly find these new courses in the Training portal, select Global Course for the Associated Organization filter and select the Only hot filter.
Enhancements
Training portal quiz translations
The True, False options and the Previous, Next buttons in the training portal quizzes now translate to the languages in which the courses were created. The table provides the language translation for each item.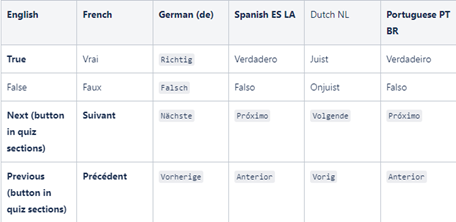
Here is an example of the quiz items that will be translated.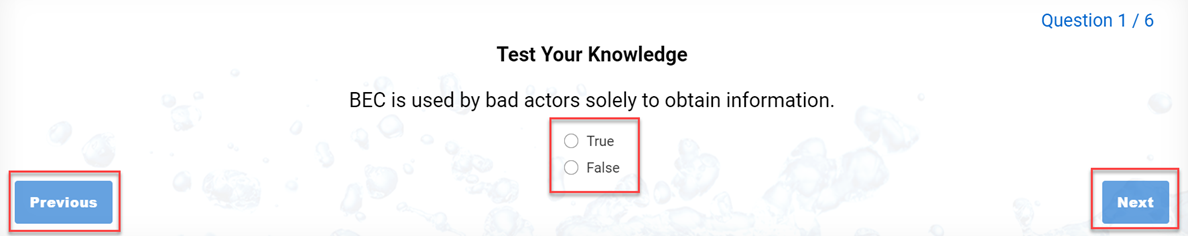
Organization search on the Training Portal page has been optimized
The organization search feature on the Training Portal page has been optimized, resulting in better performance. You perform a search the same way, but results are provided much quicker than they were previously.
New Partner Organization list added to the Targets page (portfolio users only)
For portfolio users, a new Partner Organization list has been added to the Targets page. The list includes the portfolio's partners, direct MMEs, and the MME's partners.
Previously, portfolios with a large number of targets experienced a delay before target information was displayed. By selecting one organization, target information for that organization is displayed much quicker.
When you navigate to the Targets page, the Targets table is empty and the filter bar is not available.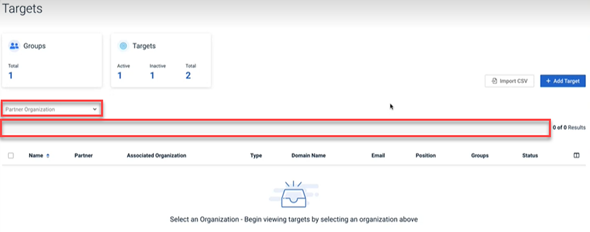
Once you select an organization in the Partner Organization list, the table populates and the filter bar is available.
Security Awareness Training Report email improvements
The template for the automated Security Awareness Training Report email has been updated to produce a more professional, visually appealing email.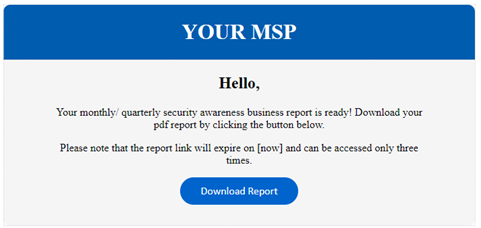
Fixes
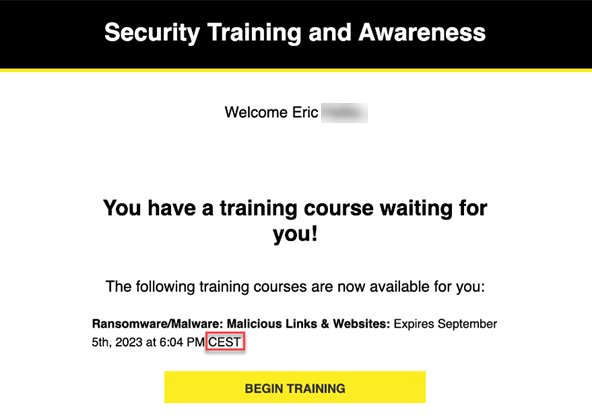
- Issue: When you included the [now] variable in your phishing and training email templates, the date and time in the email invitations was displayed in the Eastern time zone regardless of the time zone selected when creating a campaign.
Fix: Email invitations will now display the date and time for the time zone selected at the time of campaign creation. Also, the time zone is listed next to the local time.
In this example, the date and time is displayed for the Central European Summertime (CEST) time zone.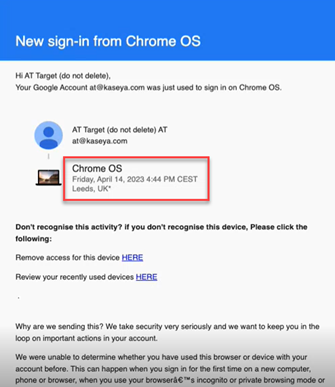
- Issue: Users experienced formatting issues in the Security Awareness Training Report email they received. These issues also occurred when the email was forwarded.
Fix: The template for creating the email has been updated, resolving the formatting issues.
Training courses update
Two new training courses are now available in the Training portal:
- Introduction to Password Security: Learn why password security is more important than you think with a real-life example of the damage that cybercriminals can do with one stolen password.
- Ransomware Basics: Learn the basics of ransomware including how it works and the damage it can do to your company.
Plus, each of these courses is available in the Latin American Spanish, Canadian French, and Portuguese (Brazil) languages.
To quickly find these new courses in the Training portal, select Global Course for the Associated Organization filter and select the Only hot filter.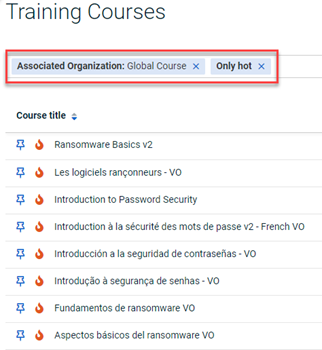
Phishing kits update
Three new phishing kits are available. Each is listed below along with an image of its email template and landing page.
To quickly find these new kits on the Phishing Kits page, select Global Kit for the Associated Organization filter and select the Only hot filter.